C9510-401 IBM D Application Server Network Deployment V8.5.5 and Liberty Profile System Administration Free Practice Exam Questions (2026 Updated)
Prepare effectively for your IBM C9510-401 D Application Server Network Deployment V8.5.5 and Liberty Profile System Administration certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
The application placement controller has been configured with elasticity mode enabled. Intermittently, all instances of a dynamic cluster are removed. After further review, the system administrator noticed that it occurs during peak load on another dynamic cluster.
The administrator wants to keep at least one instance available. Which configuration is needed in the dynamic clusters?
A system administrator completed a WebSphere Application Server installation by using the Installation Manager. During installation, all defaults were selected for the installation root directories and the shared resources directory. Over time, the administrator has updated the installation with various interim fixes and fix packs. The administrator notices that the shared resources directory is very large in size and grows larger each time the Installation Manager is run.
How can the administrator decrease the size and remove some of the content from the shared resources directory?
After collecting diagnostic trace from a server running under a cell, a system administrator noticed that the trace files contained sensitive information.
To avoid this issue in the future, what can the administrator do?
An application deployed to a multi-node cluster is reported to have slowness and hung threads. A system administrator is asked to review the logs on each node and identify if the hung threads are a false alarm.
How can the administrator determine that the hung threads are a false alarm?
Analyze the:
A system administrator needs to create a cell for a test environment. The administrator uses the Profile Management Tool (PMT) to create the deployment manager profile using the advanced profile creation option and creates a custom profile using the typical profile creation option. The administrator examines the log files for the custom profile creation and sees an INSTCONFFAIL message indicating the deployment manager was not running during the custom profile creation.
How should the administrator fix this?
A system administrator has installed WebSphere Application Server Network Deployment V8.5.5 using the silent installation process and needs the verify that the installation completed successfully.
What does the administrator need to do to verify a successful installation?
Within a WebSphere Application Server Network Deployment cell, a system administrator needs to write a script to determine if a particular server is stopped. It is important that the wsadmin script explicitly return a status of stopped as opposed to just failing.
What wsadmin object should the administrator use to write this script?
A system administrator needs to configure a JDBC provider and a data source for an application in a clustered environment. The administrator also needs to copy the JDBC drivers from the database server to the application server machines.
How can the administrator meet these requirements?
A system administrator has configured a network deployment cell containing multiple nodes and global security enabled with an LDAP repository. To increase capacity, the administrator needs to add additional nodes to the cell. After adding the nodes by using both scripts and the Integrated Solutions Console (ISC), the administrator examines the System.out log for the deployment manager and notices the following message:
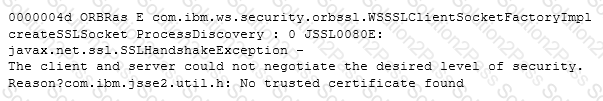
How can the administrator resolve this problem?
A system administrator in a bank was asked by business users to determine the most accessed JSP page in a web application at normal work load for marketing purpose.
Which tool should the administrator use to find the most used JSP page?
An EJB application posts a request message into a JMS destination and waits for a response message on a different JMS destination. To correlate the response message to the request message, the application uses the JMS correlationId of the message. The application waits up to five seconds for a response before timing out the request.
A Message Driven Bean (MDB) running on a different cluster is responsible for consuming the request message, process it and post a response message.
The destinations are defined in a Service Integration Bus (SIB) within the cell.
Intermittent timeout exceptions have occurred for the requester application. How can a system administrator correlate and analyze the debug information from both requester and consumer applications?
A system administrator wants to learn some of the Jython scripting commands for the administration of the environment.
Which product feature should the administrator use?
A system administrator suspects that the slow performance of an application might be caused by lock contention.
To debug this further, what can the administrator do using IBM Support Assistant?
In a test environment, a system administrator has configured an external HTTP server in the DMZ that is routing to a cluster of application servers. The administrator wants to achieve higher performance when routing and prioritizing incoming requests to the back-end cluster.
How can the system administrator achieve this task?
A system administrator, Admin1, with Administrator privileges has archived full repository checkpoints. Another administrator, Configurator1, with Configurator privileges has copied the checkpoint contents directory from one of the archived check points to its original location. Configurator1 tries to restore the configuration using the copied archived checkpoint contents and the restore fails.
How can Configurator1 restore the configuration using the copied archived full repository checkpoint?
A developer created an enterprise application which contained data source and security role information. The developer asked a system administrator to install this application to an application server where global security is enabled using the Integrated Solutions Console (ISC). A new data source was configured at the server scope for the use of this application. While load testing the application, the developer noticed that the attributes configured on the new data source were ignored by the application server.
How can the administrator ensure that the attributes configured on the new data source are used by the application server?
A system administrator has configured a cluster containing 40 servers. The cluster members all belong to one core group. While examining the log files, the administrator notices that the core group coordinator is consuming abnormally high amounts of memory and CPU resources.
How can the system administrator reduce the memory and CPU resource usage of the core group coordinator?
A system administrator decides to use the advice from the Performance and Diagnostic Advisor to identify the optimum connection pool settings for data sources. In a cell, the data source db2datasource is defined under node scope and used by two servers from that node. The administrator receives two different sets of advice for db2datasource.
One set of advice suggests to increase the maximum connection pool size for db2datasource.
The other suggests reducing the maximum connection pool size for db2datasource.
How should the administrator configure the data sources before reusing the Performance and Diagnostic Advisor?
A system administrator has created a Python script that will run in WebSphere Network cell where administrative security is enabled. This script is named doUpdate.py and will be run by using the following:
wsadmin -connType RMI -f doUpdate.py
How can the administrator suppress a user/password prompt from appearing when this script is run?
Set the user and password in the:
Which one of the following options describes the runtime flow starting from the client browser in a clustered WebSphere Application Server Network Deployment topology?
