CC ISC CC - Certified in Cybersecurity Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ISC CC CC - Certified in Cybersecurity certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which is not possible models for an Incident Response Team (IRT):
Common network device used to connect networks?
Events with a negative consequence, such as system crashes, network packet floods, unauthorized use of system privileges, defacement of a web page or execution of malicious code that destroys data.
A new BYOD policy has been enforced in NEW Corp which type of control is used to enforce thissecurity policies
In what way do a victim's files get affected by ransomware?
Exhibit.
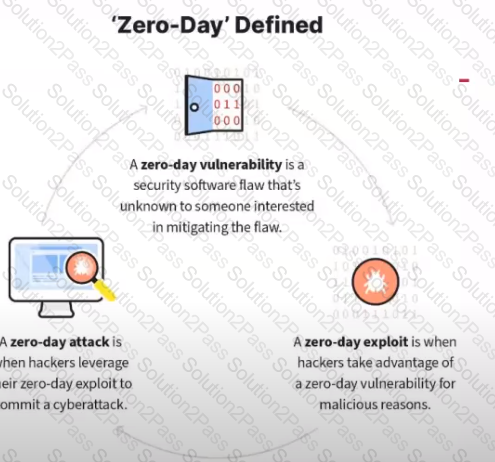
What kind of vulnerability is typically not identifiable through a standard vulnerability assessment?
Which type of encryption uses only one shared key to encrypt and decrypt?
What is the primary goal of the incident management team in the organization
Ignoring the risk and proceeding the business operations
Are a measure of an organization's baseline of security performance
Which type of attack attempts to gain information by observing the devices power consumption
A device that routes traffic to the port of a known device
When responding to a security incident, your team determines that the vulnerability that was exploited was not widely known to the security community, and that there are no currently known definitions/listings in common vulnerability databases or collections. This vulnerability and exploit might be called______
What is the purpose of multi-factor authentication (MFA) in 1AM?
A company primary data center goes down due to a hardware failure causing a major disruption to the IT and communications systems. What is the focus of disaster recovery planning in this scenario
What is the priority of incident response in the context of incident management
The purpose of risk identification:
What is the range of well known ports
Which of these is WEAKEST form of authentication we can implement?
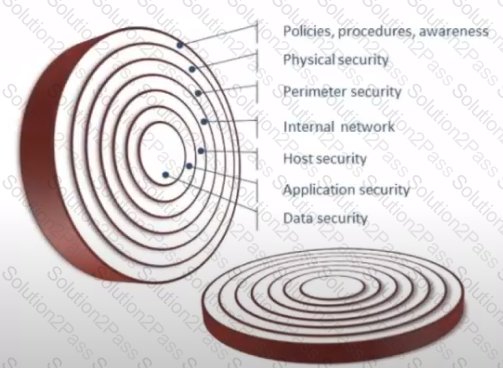
Which layer of OSI the Firewall works
