HCISPP ISC HealthCare Information Security and Privacy Practitioner Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ISC HCISPP HealthCare Information Security and Privacy Practitioner certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Under the HIPAA Privacy Rule, who is NOT considered a covered entity?
May a health plan require a provider to use a health care clearinghouse to conduct a HIPPA-covered transaction, or must the health plan acquire the ability to conduct the transaction directly with those providers capable of conducting direct transactions?
He proved the continuous circulation of blood within a contained system.
Title I of The Health Insurance Portability and Accountability Act protects:
Which is NOT one of the three major categories of Security Safeguards identified by HIPAA in the regulations?
According to private sector data classification levels, how would salary levels and medical information be classified?
A release of information must include which of the following?
Among women, which racial/ethnic group has the highest percentage distribution of AIDS?
When controlling the type of supply, increasing the amount of generalists could contain costs because.
Confidential information must not be shared with another unless the recipient has:
Lack of insurance can result in:
As health care resources increase:
What does the federal Ryan White CARE Act fund?
Health Care Providers, however
Is concised, accurate records of actions taken and decisions made during the meeting.
Who discovered that ether gas could safely be used to put patients to sleep for surgery?
When assessing an organization’s security policy according to standards established by the International Organization for Standardization (ISO) 27001 and 27002, when can management responsibilities be defined?
A risk assessment report recommends upgrading all perimeter firewalls to mitigate a particular finding. Which of the following BEST supports this recommendation?
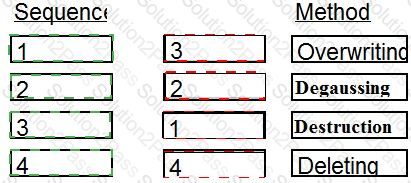
Place in order, from BEST (1) to WORST (4), the following methods to reduce the risk of data remanence on magnetic media.

Which of the following is the PRIMARY risk with using open source software in a commercial software construction?