SSCP ISC Systems Security Certified Practitioner Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ISC SSCP Systems Security Certified Practitioner certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Who is responsible for implementing user clearances in computer-based information systems at the B3 level of the TCSEC rating ?
What prevents a process from accessing another process' data?
At what stage of the applications development process should the security department become involved?
What security problem is most likely to exist if an operating system permits objects to be used sequentially by multiple users without forcing a refresh of the objects?
What is the goal of the Maintenance phase in a common development process of a security policy?
Which of the following is commonly used for retrofitting multilevel security to a database management system?
What is the act of obtaining information of a higher sensitivity by combining information from lower levels of sensitivity?
Which of the following refers to the data left on the media after the media has been erased?
Which of the following are NOT a countermeasure to traffic analysis?
In an organization, an Information Technology security function should:
Which of the following phases of a software development life cycle normally addresses Due Care and Due Diligence?
Which of the following would be the best reason for separating the test and development environments?
How many bits is the effective length of the key of the Data Encryption Standard algorithm?
What principle focuses on the uniqueness of separate objects that must be joined together to perform a task? It is sometimes referred to as “what each must bring” and joined together when getting access or decrypting a file. Each of which does not reveal the other?
What size is an MD5 message digest (hash)?
In a hierarchical PKI the highest CA is regularly called Root CA, it is also referred to by which one of the following term?
Which of the following keys has the SHORTEST lifespan?
Which of the following would best describe a Concealment cipher?
In a Public Key Infrastructure, how are public keys published?
Which of the following statements pertaining to Secure Sockets Layer (SSL) is false?
Which of the following is not a DES mode of operation?
Which of the following is an Internet IPsec protocol to negotiate, establish, modify, and delete security associations, and to exchange key generation and authentication data, independent of the details of any specific key generation technique, key establishment protocol, encryption algorithm, or authentication mechanism?
Which of the following is true about link encryption?
Which of the following is NOT a true statement regarding the implementaton of the 3DES modes?
Which of the following statements is most accurate regarding a digital signature?
The Data Encryption Standard (DES) encryption algorithm has which of the following characteristics?
Which of the following algorithms is a stream cipher?
Which of the following terms can be described as the process to conceal data into another file or media in a practice known as security through obscurity?
In what type of attack does an attacker try, from several encrypted messages, to figure out the key used in the encryption process?
What is the name of a one way transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string? Such a transformation cannot be reversed?
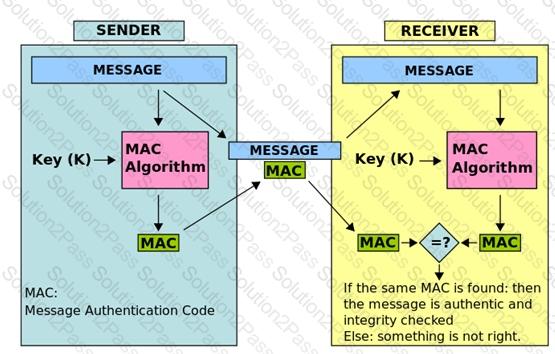
Which of the following is NOT a known type of Message Authentication Code (MAC)?
The Diffie-Hellman algorithm is primarily used to provide which of the following?
Which of the following is not a property of the Rijndael block cipher algorithm?
Which of the following services is NOT provided by the digital signature standard (DSS)?
What algorithm was DES derived from?
Virus scanning and content inspection of SMIME encrypted e-mail without doing any further processing is:
Which of the following is the most secure form of triple-DES encryption?
Which of the following is NOT an asymmetric key algorithm?
Which is NOT a suitable method for distributing certificate revocation information?
Which of the following was developed in order to protect against fraud in electronic fund transfers (EFT) by ensuring the message comes from its claimed originator and that it has not been altered in transmission?