SSCP ISC Systems Security Certified Practitioner Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ISC SSCP Systems Security Certified Practitioner certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following elements is NOT included in a Public Key Infrastructure (PKI)?
Which of the following ciphers is a subset on which the Vigenere polyalphabetic cipher was based on?
What uses a key of the same length as the message where each bit or character from the plaintext is encrypted by a modular addition?
Where parties do not have a shared secret and large quantities of sensitive information must be passed, the most efficient means of transferring information is to use Hybrid Encryption Methods. What does this mean?
Which of the following is true about Kerberos?
The Secure Hash Algorithm (SHA-1) creates:
What kind of certificate is used to validate a user identity?
Which of the following statements pertaining to stream ciphers is correct?
What attribute is included in a X.509-certificate?
A one-way hash provides which of the following?
Which of the following would best describe certificate path validation?
Which of the following encryption algorithms does not deal with discrete logarithms?
Which of the following does NOT concern itself with key management?
What is the name of the protocol use to set up and manage Security Associations (SA) for IP Security (IPSec)?
Which of the following service is not provided by a public key infrastructure (PKI)?
What can be defined as an instance of two different keys generating the same ciphertext from the same plaintext?
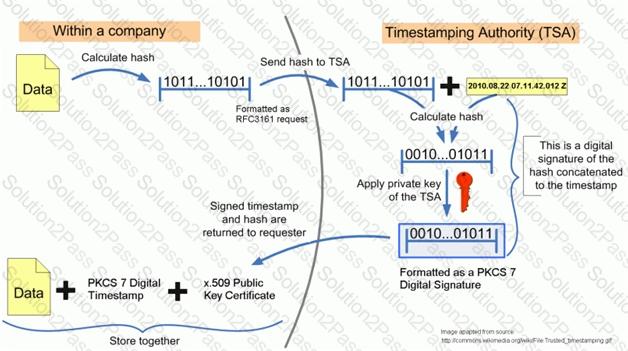
What is used to bind a document to its creation at a particular time?
What is the role of IKE within the IPsec protocol?
Java is not:
Which of the following technologies is a target of XSS or CSS (Cross-Site Scripting) attacks?
In computing what is the name of a non-self-replicating type of malware program containing malicious code that appears to have some useful purpose but also contains code that has a malicious or harmful purpose imbedded in it, when executed, carries out actions that are unknown to the person installing it, typically causing loss or theft of data, and possible system harm.
Which of the following virus types changes some of its characteristics as it spreads?
Virus scanning and content inspection of SMIME encrypted e-mail without doing any further processing is:
Which of the following computer crime is MORE often associated with INSIDERS?
What best describes a scenario when an employee has been shaving off pennies from multiple accounts and depositing the funds into his own bank account?
What is malware that can spread itself over open network connections?
What do the ILOVEYOU and Melissa virus attacks have in common?
The high availability of multiple all-inclusive, easy-to-use hacking tools that do NOT require much technical knowledge has brought a growth in the number of which type of attackers?
Which virus category has the capability of changing its own code, making it harder to detect by anti-virus software?
Crackers today are MOST often motivated by their desire to:
Controls to keep password sniffing attacks from compromising computer systems include which of the following?
An attack initiated by an entity that is authorized to access system resources but uses them in a way not approved by those who granted the authorization is known as a(n):
What is the primary role of smartcards in a PKI?
What is called a password that is the same for each log-on session?
Identification and authentication are the keystones of most access control systems. Identification establishes:
The three classic ways of authenticating yourself to the computer security software are: something you know, something you have, and something:
In the context of access control, locks, gates, guards are examples of which of the following?
The Orange Book is founded upon which security policy model?
Which of the following pairings uses technology to enforce access control policies?
Which of the following is needed for System Accountability?