SSCP ISC Systems Security Certified Practitioner Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ISC SSCP Systems Security Certified Practitioner certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
In order to ensure the privacy and integrity of the data, connections between firewalls over public networks should use:
The International Standards Organization / Open Systems Interconnection (ISO/OSI) Layers does NOT have which of the following characteristics?
Which of the following is true related to network sniffing?
What protocol is used to match an IP address to the appropriate hardware address of the packet's destination so it can be sent?
A circuit level proxy is ___________________ when compared to an application level proxy.
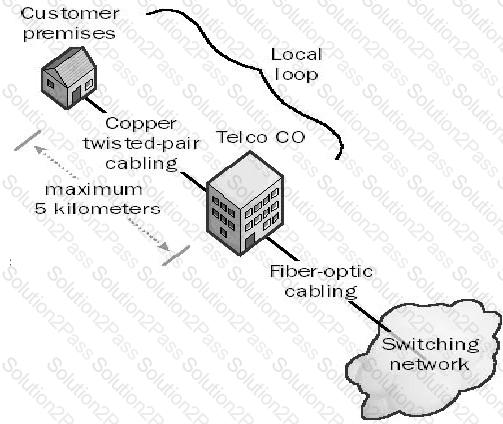
In telephony different types of connections are being used. The connection from the phone company's branch office to local customers is referred to as which of the following choices?
What is the main characteristic of a bastion host?
Domain Name Service is a distributed database system that is used to map:
At which layer of ISO/OSI does the fiber optics work?
SMTP can best be described as:
The IP header contains a protocol field. If this field contains the value of 1, what type of data is contained within the IP datagram?
Which layer of the DoD TCP/IP Model ensures error-free delivery and packet sequencing?
Which layer of the TCP/IP protocol stack corresponds to the ISO/OSI Network layer (layer 3)?
Organizations should consider which of the following first before allowing external access to their LANs via the Internet?
You have been tasked to develop an effective information classification program. Which one of the following steps should be performed first?
Unshielded Twisted Pair cabling is a:
A DMZ is located:
FTP, TFTP, SNMP, and SMTP are provided at what level of the Open Systems Interconnect (OSI) Reference Model?
What protocol is used on the Local Area Network (LAN) to obtain an IP address from it's known MAC address?
Which of the following is the core of fiber optic cables made of?
What is the 802.11 standard related to?
Which one of the following is usually not a benefit resulting from the use of firewalls?
Which of the following elements of telecommunications is not used in assuring confidentiality?
Which of the following is NOT a VPN communications protocol standard?
Which of the following is an example of a connectionless communication protocol?
Which of the following transmission media would NOT be affected by cross talk or interference?
Network cabling comes in three flavors, they are:
Which of the following service is a distributed database that translate host name to IP address to IP address to host name?
Which layer of the DoD TCP/IP model controls the communication flow between hosts?
Which of the following security-focused protocols has confidentiality services operating at a layer different from the others?
Which type of attack consists of modifying the length and fragmentation offset fields in sequential IP packets?
Which of the following statements pertaining to Asynchronous Transfer Mode (ATM) is false?
Secure Shell (SSH) is a strong method of performing:
Application Layer Firewalls operate at the:
Similar to Secure Shell (SSH-2), Secure Sockets Layer (SSL) uses symmetric encryption for encrypting the bulk of the data being sent over the session and it uses asymmetric or public key cryptography for:
Which of the following is a method of multiplexing data where a communication channel is divided into an arbitrary number of variable bit-rate digital channels or data streams. This method allocates bandwidth dynamically to physical channels having information to transmit?