202-450 LPIC-2 - Exam 202 (part 2 of 2), version 4.5 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your LPI 202-450 LPIC-2 - Exam 202 (part 2 of 2), version 4.5 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which BIND option should be used to limit the IP addresses from which slave name servers may connect?
Which of the following services belongs to NFSv4 and does not exist in NFSv3?
The following Apache HTTPD configuration has been set up to create a virtual host available at www.example.com and www2.example.com:
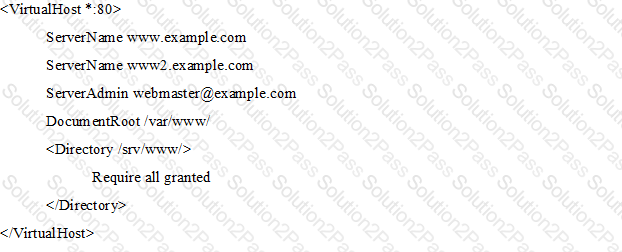
Even though Apache HTTPD correctly processed the configuration file, requests to both names are not handled correctly. What should be changed in order to ensure correct operations?
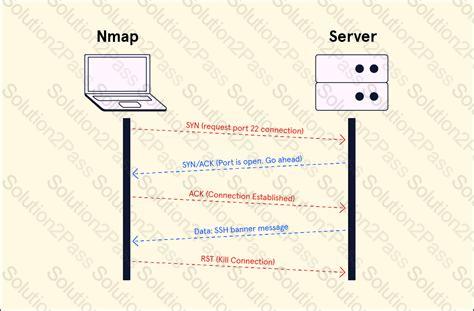
For what purpose is TCP/IP stack fingerprinting used by nmap?
Which Apache HTTPD directive enables HTTPS protocol support?
Which of the following nmap parameters scans a target for open TCP ports? (Choose two.)
Which doveadm sub-command displays a list of connections of Dovecot in the following format? (Specify ONLY the command without any parameters.)
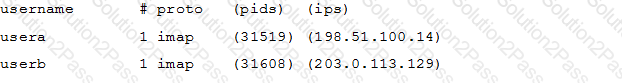
Which Postfix command can be used to rebuild all of the alias database files with a single invocation and without the need for any command line arguments?
With Nginx, which of the following directives is used to proxy requests to a FastCGI application?
Which of the following DNS records could be a glue record?
Which of the following authentication mechanisms are supported by Dovecot? (Choose three.)
What command creates a SSH key pair? (Specify ONLY the command without any path or parameters)
What option in the sshd configuration file instructs sshd to permit only specific user names to log in to a system? (Specify ONLY the option name without any values.)
Which of the following lines in the sshd configuration file should, if present, be changed in order to increase the security of the server? (Choose two.)
Which of the following values can be used in the OpenLDAP attribute olcBackend for any object of the class olcBackendConfig to specify a backend? (Choose three.)
 Cybersecurity | Nmap | TCP Connect Scan | Codecademy
Cybersecurity | Nmap | TCP Connect Scan | Codecademy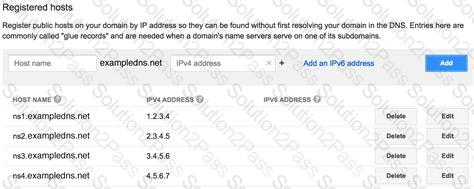 Glue Records and Dedicated DNS - NS1, an IBM Company
Glue Records and Dedicated DNS - NS1, an IBM Company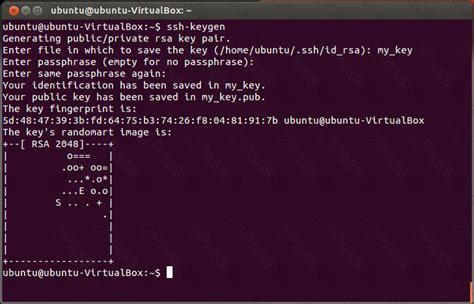 How to Use ssh-keygen to Generate a New SSH Key?
How to Use ssh-keygen to Generate a New SSH Key?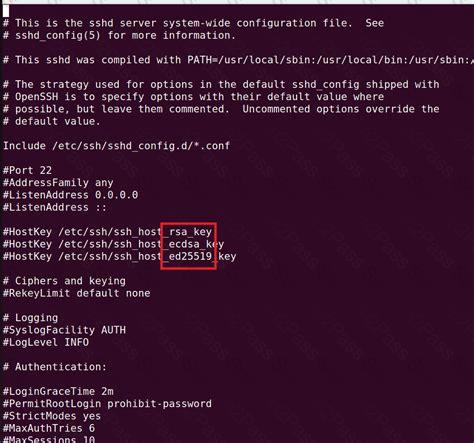 Linux SSH Server (sshd) Configuration and Security Options With ...1
Linux SSH Server (sshd) Configuration and Security Options With ...1 The Best Ways to Secure Your SSH Server - How-To Geek
The Best Ways to Secure Your SSH Server - How-To Geek