CFR-210 Logical Operations CyberSec First Responder Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Logical Operations CFR-210 Logical Operations CyberSec First Responder certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An attacker has exfiltrated the SAM file from a Windows workstation. Which of the following attacks is MOST likely being perpetrated?
When performing an investigation, a security analyst needs to extract information from text files in a Windows operating system. Which of the following commands should the security analyst use?
A suspicious laptop is found in a datacenter. The laptop is on and processing data, although there is no application open on the screen. Which of the following BEST describes a Windows tool and technique that an investigator should use to analyze the laptop’s RAM for working applications?
Network engineering has reported low bandwidth during working hours. The incident response team is currently investigating several anomalous activities that may be related. Which of the following is the MOST appropriate method to further investigate this problem?
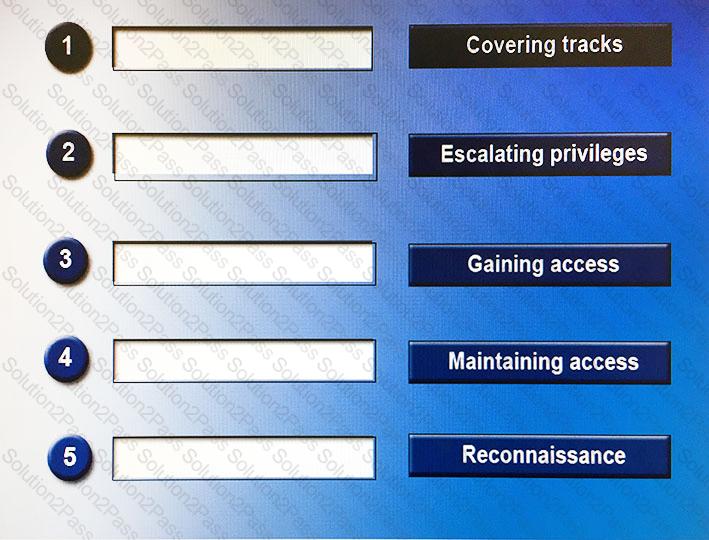
When perpetrating an attack, there are often a number of phases attackers will undertake, sometimes taking place over a long period of time. Place the following phases in the correct chronological order from first (1) to last (5).
A security analyst would like to parse through several SQL logs for indicators of compromise. The analyst is aware that none of the fields should contain a string of text longer than 30 characters; however, the analyst is unaware if there are any implemented controls to prevent such an overflow. Which of the following BEST describes the regular expression the analyst should use to find any alphanumeric character string?
A UNIX workstation has been compromised. The security analyst discovers high CPU usage during off-hours on the workstation. Which of the following UNIX programs can be used to detect the rogue process? (Choose two.)
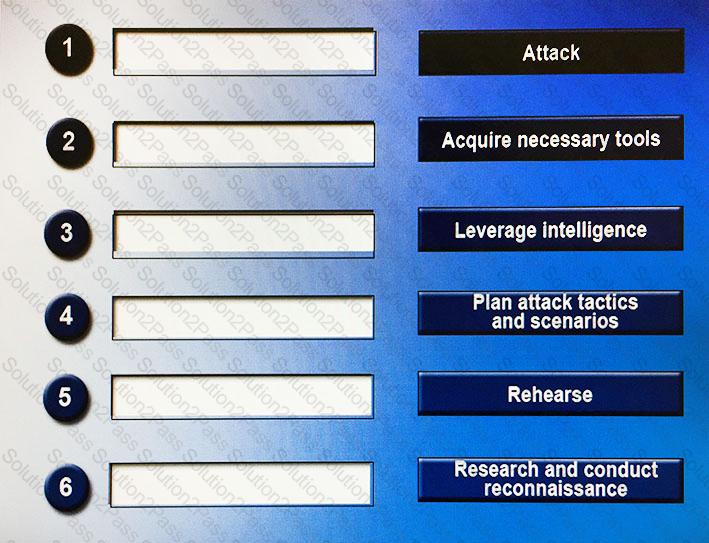
Drag and drop the following steps to perform a successful social engineering attack in the correct order, from first (1) to last (6).
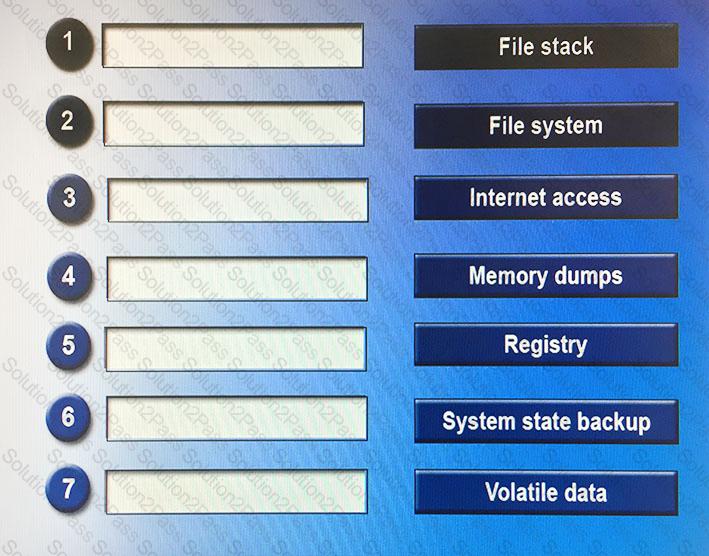
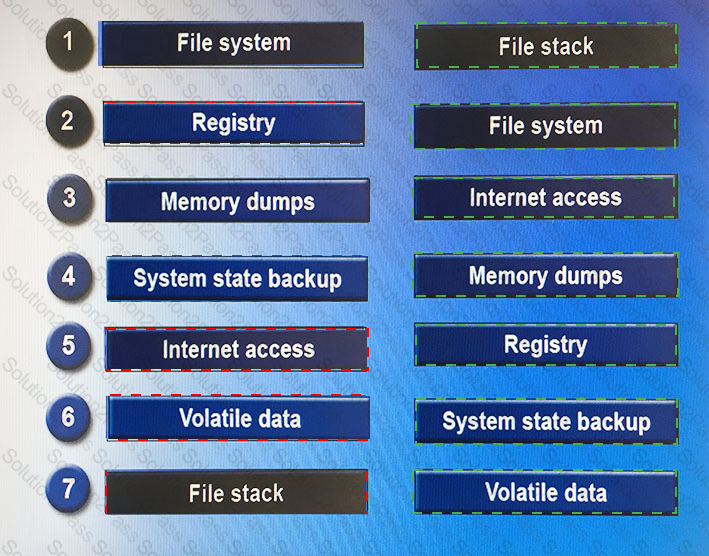
Drag and drop the following steps in the correct order from first (1) to last (7) that a forensic expert would follow based on data analysis in a Windows system.
A DMZ web server has been compromised. During the log review, the incident responder wants to parse all common internal Class A addresses from the log. Which of the following commands should the responder use to accomplish this?
Which of the following could an attacker use to perpetrate a social engineering attack? (Choose two.)
An analyst would like to search for a specific text string at the beginning of a line that begins with four capital alphabetic characters. Which of the following search operators should be used?
During a malware outbreak, a security analyst has been asked to capture network traffic in hourly increments for analysis by the incident response team. Which of the following tcpdump commands would generate hourly pcap files?
Which of the following describes pivoting?
A network administrator has been asked to configure a new network. It is the company’s policy to segregate network functions using different Virtual LANs (VLANs). On which of the following is this configuration MOST likely to occur?
Which of the following commands should be used to print out ONLY the second column of items in the following file?
Source_File,txt
Alpha Whiskey
Bravo Tango
Charlie Foxtrot
Echo Oscar
Delta Roger
An organization’s public information website has been defaced. The incident response team is actively engaged in the following actions:
- Installing patches on the web server
- Turning off unnecessary services on web server
- Adding new ACL rules to the WAF
- Changing all passwords on web server accounts
Which of the following incident response phases is the team MOST likely conducting?
An incident responder is asked to work with the IT department to address patch management issues with the company servers. Which of the following is the BEST source for the incident responder to obtain the CVEs for the latest industry-recognized patches?
Which of the following enables security personnel to have the BEST security incident recovery practices?
From a compromised system, an attacker bypasses a proxy server and sends a large amount of data to a remote location. A security analyst is tasked with finding the conduit that was used by the attacker to bypass the proxy. Which of the following Windows tools should be used to find the conduit?