AZ-500 Microsoft Azure Security Technologies Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Microsoft AZ-500 Microsoft Azure Security Technologies certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You need to implement the planned change for WAF1.
The solution must minimize administrative effort
What should you do?
You need to delegate a user to implement the planned change for Defender for Cloud.
The solution must follow the principle of least privilege.
Which user should you choose?
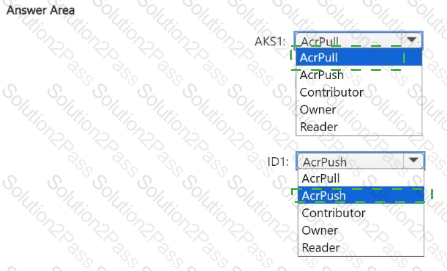
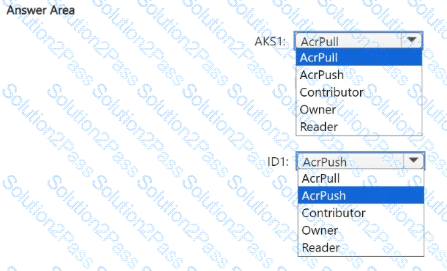
You need to configure the AKS1 and ID1 managed identities to meet the technical requirements. The solution must follow the principle of least privilege.
Which role should you assign to each identity? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains an Azure Key Vault Standard key vault named Vault1. Vault1 hosts a 2048-bit RSA key named key1.
You need to ensure that key1 is rotated every 90 days.
What should you do first?
You need to implement the planned change for SQLdb1.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You need to implement the planned change for VM1 to access storage1.
The solution must meet the technical requirements.
What should you do first?
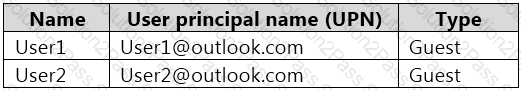
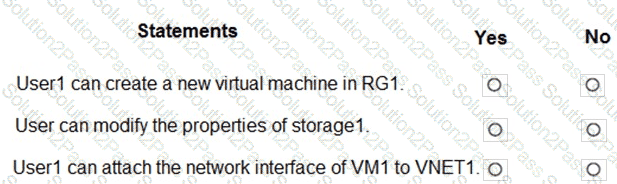
You have an Azure subscription named Subscription1 that contains a resource group named RG1 and the users shown in the following table.
You perform the following tasks:
Assign User1 the Network Contributor role for Subscription1.
Assign User2 the Contributor role for RG1.
To Subscription1 and RG1, you assign the following policy definition: External accounts with write permissions should be removed from your subscription.
What is the Compliance State of the policy assignments?
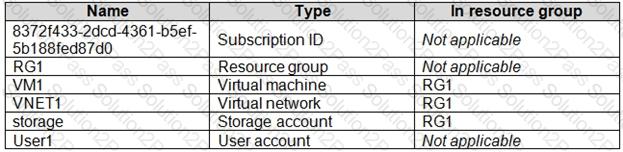
You have an Azure subscription named Subscription1 that contains the resources shown in the following table.
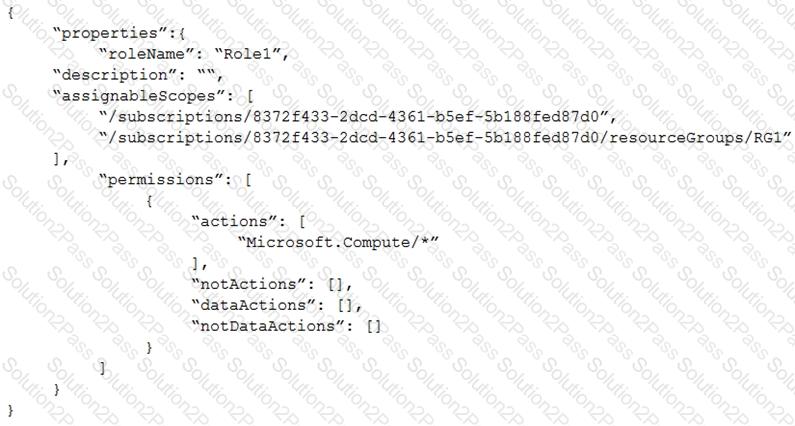
You create an Azure role by using the following JSON file.
You assign Role1 to User1 for RG1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Your company has an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com.
The company develops an application named App1. App1 is registered in Azure AD.
You need to ensure that App1 can access secrets in Azure Key Vault on behalf of the application users.
What should you configure?
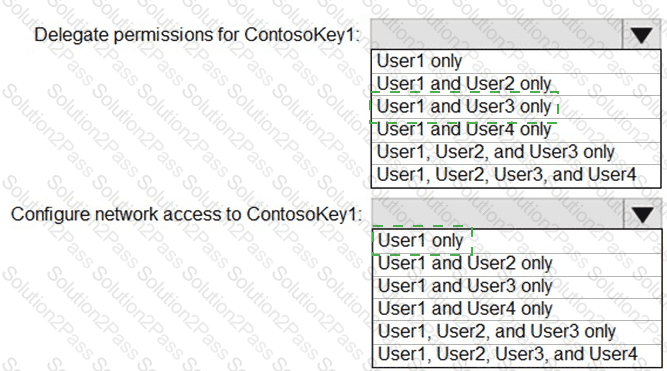
You have an Azure subscription that contains an Azure key vault named ContosoKey1.
You create users and assign them roles as shown in the following table.
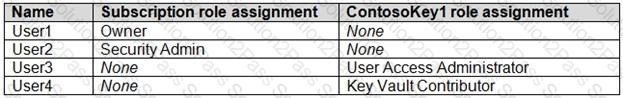
You need to identify which users can perform the following actions:
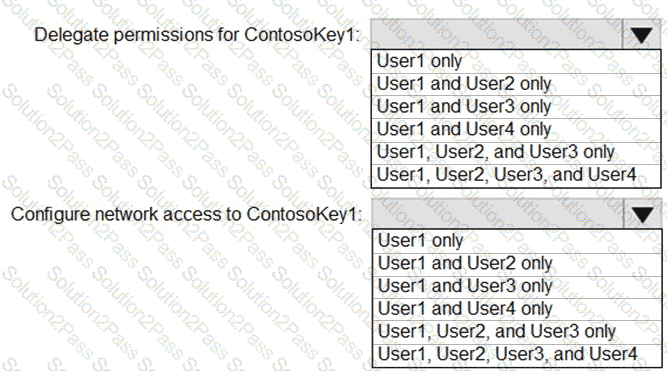
Delegate permissions for ContsosKey1.
Configure network access to ContosoKey1.
Which users should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains a web app named Appl. App1 provides users with product images and videos. Users access App1 by using a URL of HTTPS://appl.contoso.com. You deploy two server pools named Pool! and Pool2. Pool1 hosts product images. Pool2 hosts product videos. You need to optimize The performance of Appl. The solution must meet the following requirements:
• Minimize the performance impact of TLS connections on Pool1 and Pool2.
• Route user requests to the server pools based on the requested URL path.
What should you include in the solution?
You have an Azure subscription that contains the resources shown in the following table.
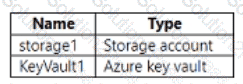
You need to configure storage1 to regenerate keys automatically every 90 days. Which cmdlet should you run?
You onboard Azure Sentinel. You connect Azure Sentinel to Azure Security Center.
You need to automate the mitigation of incidents in Azure Sentinel. The solution must minimize administrative effort.
What should you create?
You have an Azure subscription.
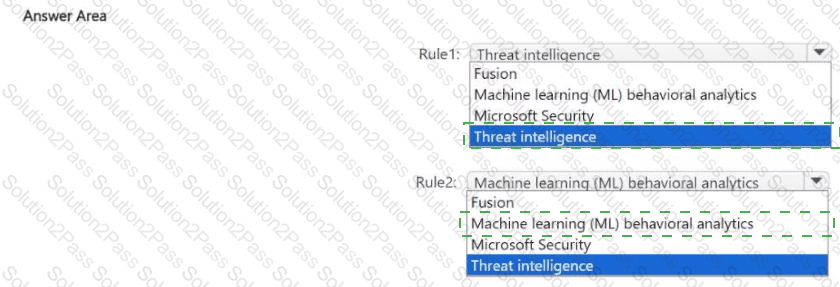
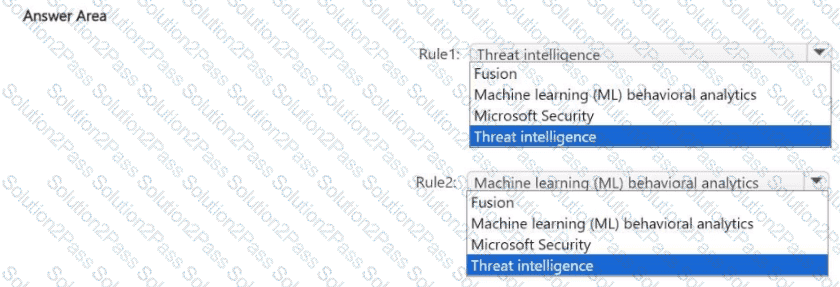
You configure Microsoft Sentinel to use multiple data sources.
You need to create analytic rules that meet the following requirements:
* Rule 1: Automatically match Common Event Format (CEF) logs and syslog data with domain, IP address, and URL indicators.
* Rule 2: Use Microsoft proprietary algorithms.
Which type of detection should you use for each rule? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Your company plans to create separate subscriptions for each department. Each subscription will be
associated to the same Azure Active Directory (Azure AD) tenant.
You need to configure each subscription to have the same role assignments.
What should you use?
You have an Azure subscription that contains the Azure virtual machines shown in the following table.
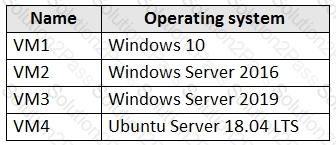
You create an MDM Security Baseline profile named Profile1.
You need to identify to which virtual machines Profile1 can be applied.
Which virtual machines should you identify?
You have an Azure subscription that contains an Azure Active Directory (Azure AD) tenant.
When a developer attempts to register an app named App1 in the tenant, the developer receives the error message shown in the following exhibit.
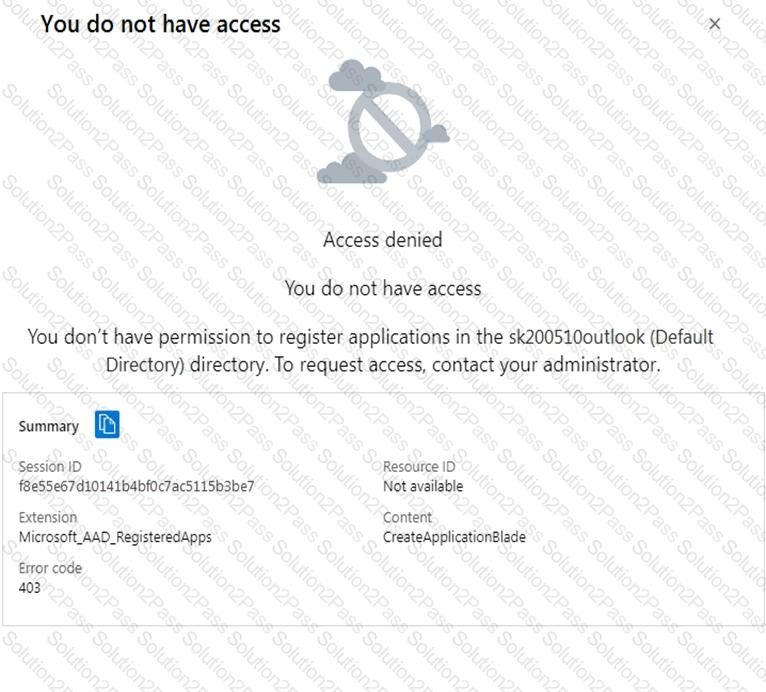
You need to ensure that the developer can register App1 in the tenant.
What should you do for the tenant?
You have an Azure subscription that contains the storage accounts shown in the following table.
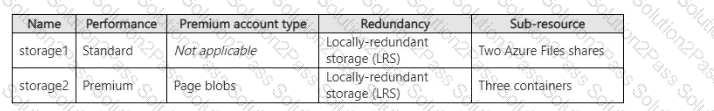
You need to create private endpoints for the target sub-resources of the storage accounts. The solution must ensure that all the target sub-resources can be accessed by using a private endpoint.
What is the minimum number of private endpoints you should create for each storage account? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
 s
s
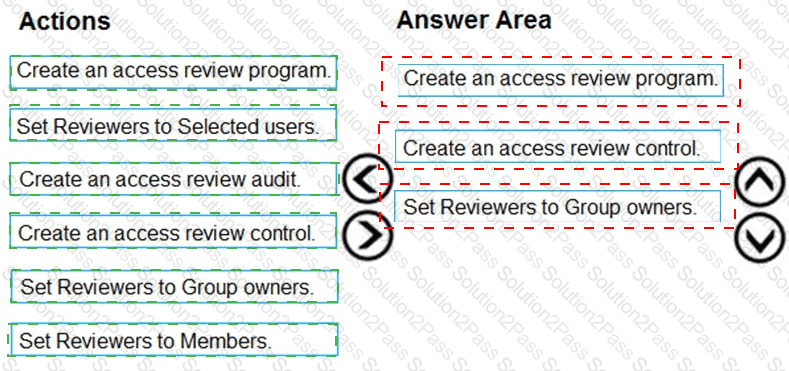
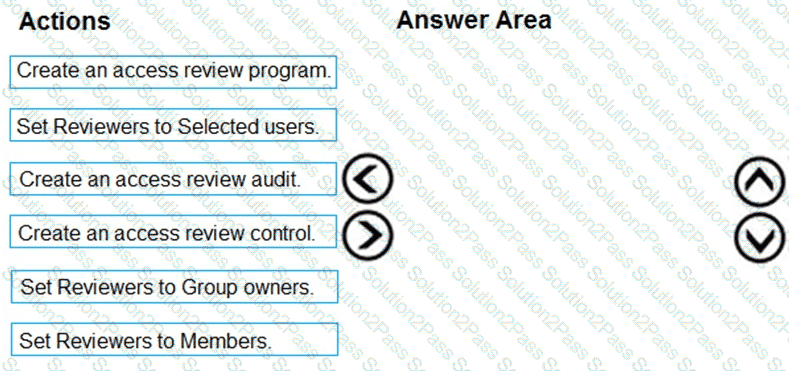
You need to configure an access review. The review will be assigned to a new collection of reviews and reviewed by resource owners.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have an Azure subscription that contains four Azure SQL managed instances.
You need to evaluate the vulnerability of the managed instances to SQL injection attacks.
What should you do first?