SC-200 Microsoft Security Operations Analyst Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Microsoft SC-200 Microsoft Security Operations Analyst certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
The issue for which team can be resolved by using Microsoft Defender for Endpoint?
You need to remediate active attacks to meet the technical requirements.
What should you include in the solution?
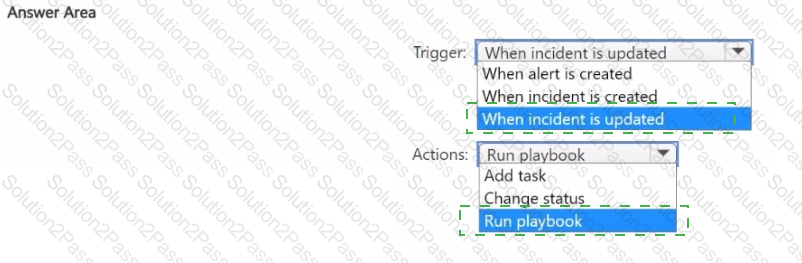
You have a Microsoft Sentinel workspace that uses the Microsoft 365 Defender data connector.
From Microsoft Sentinel, you investigate a Microsoft 365 incident.
You need to update the incident to include an alert generated by Microsoft Defender for Cloud Apps.
What should you use?
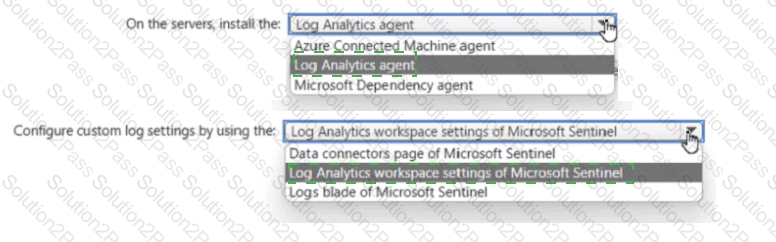
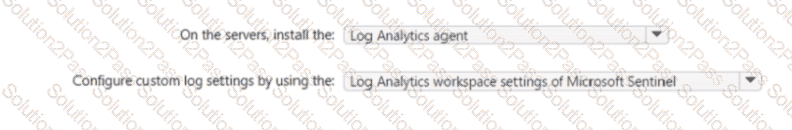
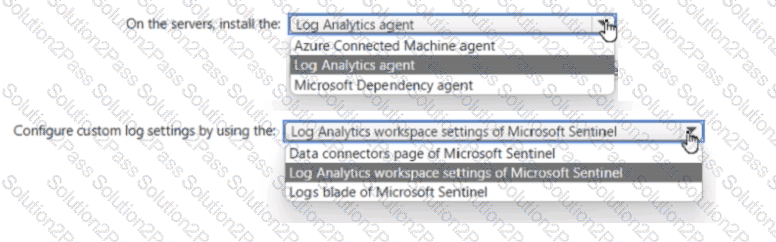
Your on-premises network contains 100 servers that run Windows Server.
You have an Azure subscription that uses Microsoft Sentinel.
You need to upload custom logs from the on-premises servers to Microsoft Sentinel.
What should you do? To answer, select the appropriate options m the answer area.
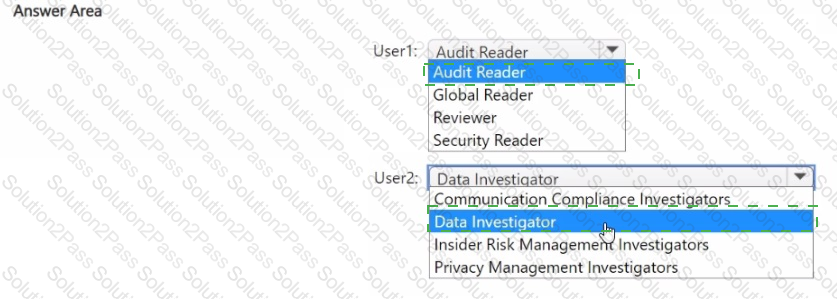
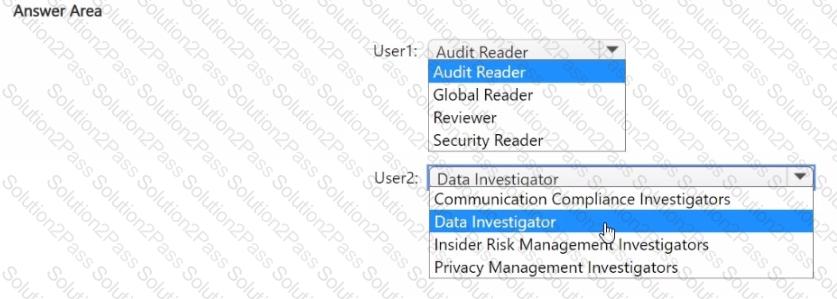
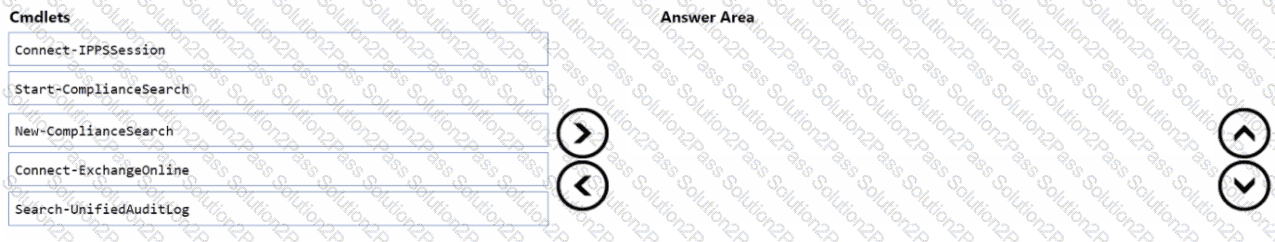
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR and contains two users named User1 and User2.
You need to ensure that the users can perform searches by using the Microsoft Purview portal. The solution must meet the following requirements:
• Ensure that User1 can search the Microsoft Purview Audit service logs and review the Microsoft Purview Audit service configuration.
• Ensure that User2 can search Microsoft Exchange Online mailboxes.
• Follow the principle of least privilege.
To which Microsoft Purview role group should you add each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains a Windows device named Device 1. You initiate a live response session on Device1 and launch an executable file named File1.exe in the background. You need to perform the following actions:
• Identify the command ID of File1 exe.
• lnteractwithFile1.exe.
Which live response command should you run for each action? To answer, select the appropriate options in the answer area.
NOTE Each correct selection is worth one point.

You have a Microsoft Sentinel workspace that contains the following incident.
Brute force attack against Azure Portal analytics rule has been triggered.
You need to identify the geolocation information that corresponds to the incident.
What should you do?
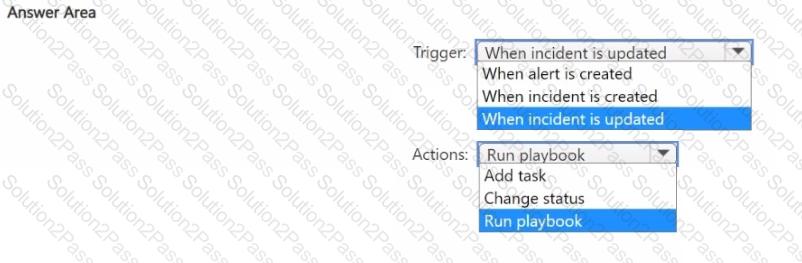
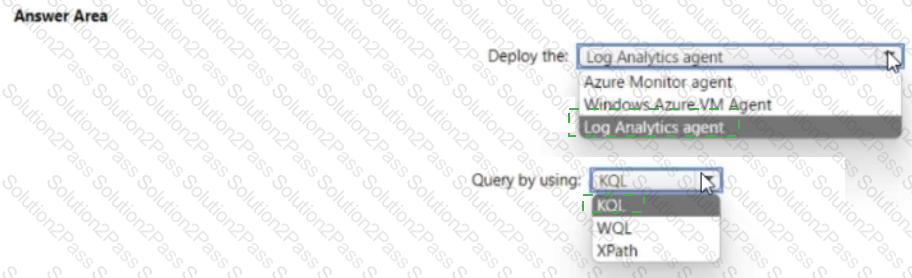
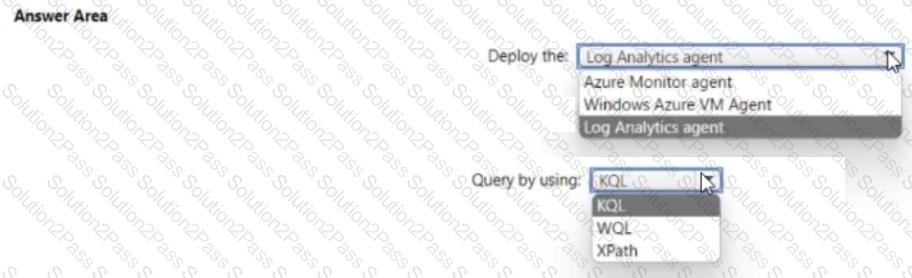
You need to meet the Microsoft Sentinel requirements for collecting Windows Security event logs. What should you do? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring Microsoft Defender for Identity integration with Active Directory.
From the Microsoft Defender for identity portal, you need to configure several accounts for attackers to exploit.
Solution: You add each account as a Sensitive account.
Does this meet the goal?
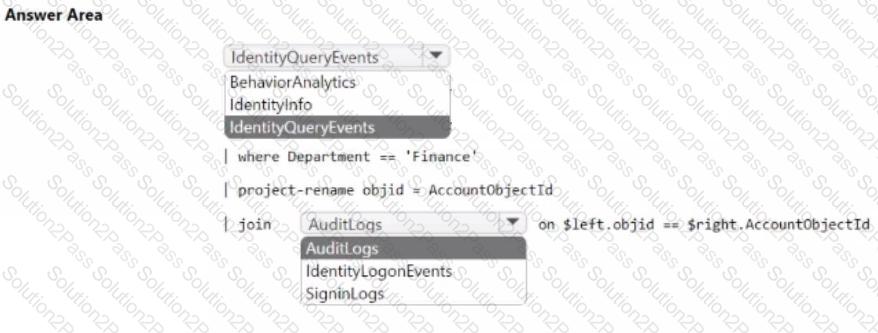
Your network contains an on-premises Active Directory Domain Services (AD DS) domain that syncs with Azure AD.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365.
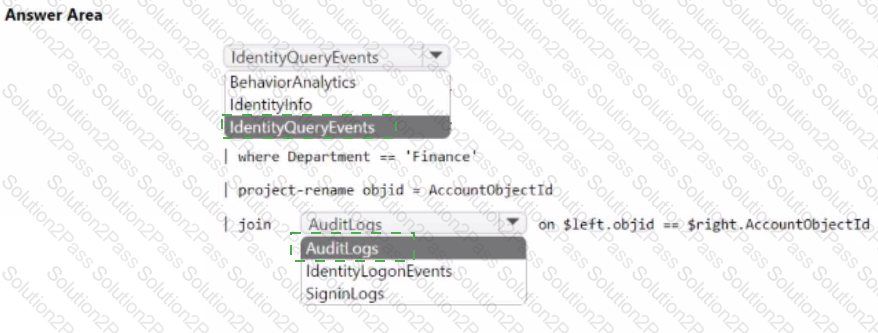
You need to identify all the interactive authentication attempts by the users in the finance department of your company.
How should you complete the KQL query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have 50 Microsoft Sentinel workspaces.
You need to view all the incidents from all the workspaces on a single page in the Azure portal. The solution must minimize administrative effort.
Which page should you use in the Azure portal?
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains 500 Windows devices. As part of an incident investigation, you identify the following suspected malware files:
• sys
• docx
• xlsx
You need to create indicator hashes to block users from downloading the files to the devices. Which files can you block by using the indicator hashes?
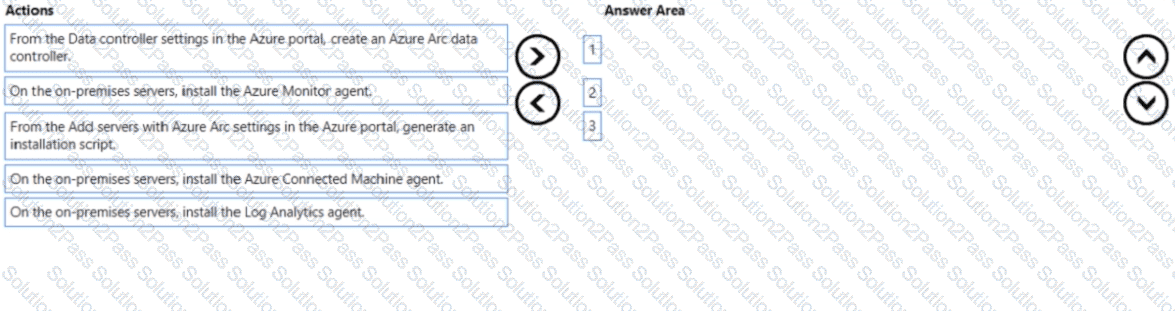
You have 50 on-premises servers.
You have an Azure subscription that uses Microsoft Defender for Cloud. The Defender for Cloud deployment has Microsoft Defender for Servers and automatic provisioning enabled.
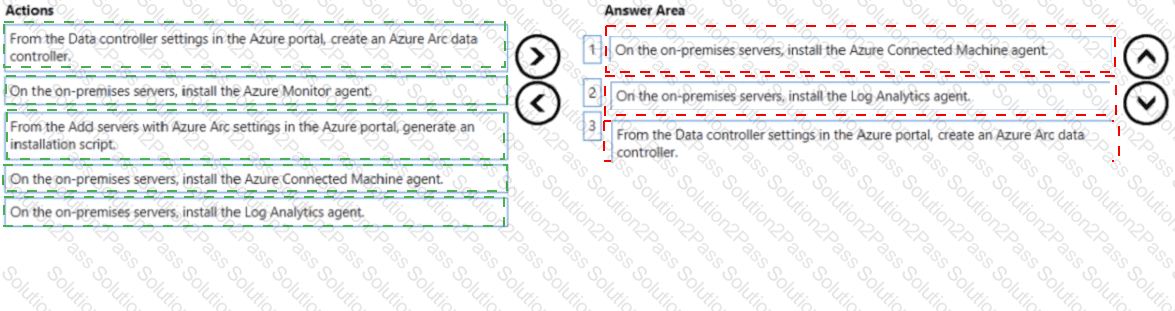
You need to configure Defender for Cloud to support the on-premises servers. The solution must meet the following requirements:
• Provide threat and vulnerability management.
• Support data collection rules.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft 365 E5 subscription that uses Microsoft Exchange Online.
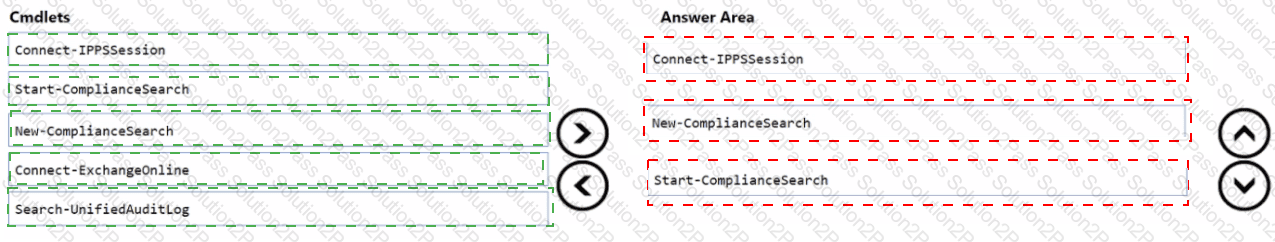
You need to identify phishing email messages.
Which three cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.
You have an Azure Sentinel workspace.
You need to test a playbook manually in the Azure portal. From where can you run the test in Azure Sentinel?
You have a Microsoft Sentinel workspace.
You need to configure the Fusion analytics rule to temporarily supress incidents generated by a Microsoft Defender connector. The solution must meet the following requirements:
• Minimize impact on the ability to detect multistage attacks.
• Minimize administrative effort.
How should you configure the rule? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.