SC-401 Microsoft Administering Information Security in Microsoft 365 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Microsoft SC-401 Administering Information Security in Microsoft 365 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You have a Microsoft 365 E5 subscription.
Users access their mailbox by using the following apps.
• Outlook for Microsoft 365
• Outlook on the web
• Outlook Mobile fiOS. Android)
You create a data loss prevention (DLP) policy named DLP1 that has the following settings:
• Location; Exchange email
• Status: On
• User notifications: On
• Notify users with a policy tip: Enabled
Which apps display a policy tip when content is matched by using DIP1 ?
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
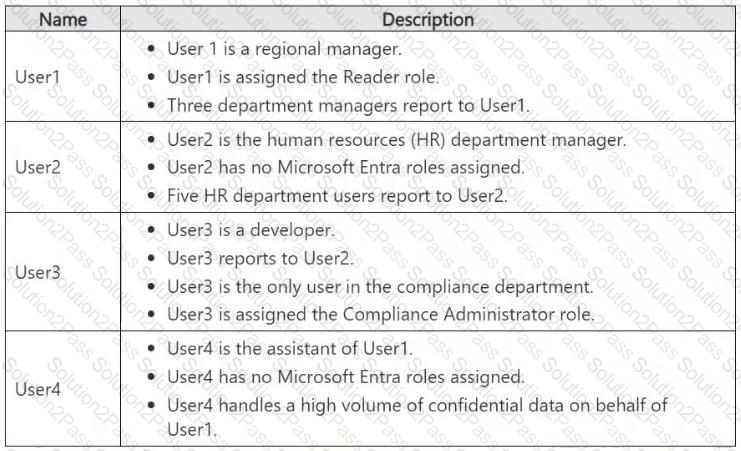
Which users will Microsoft Purview insider risk management flag as potential high-impact users?
HOTSPOT
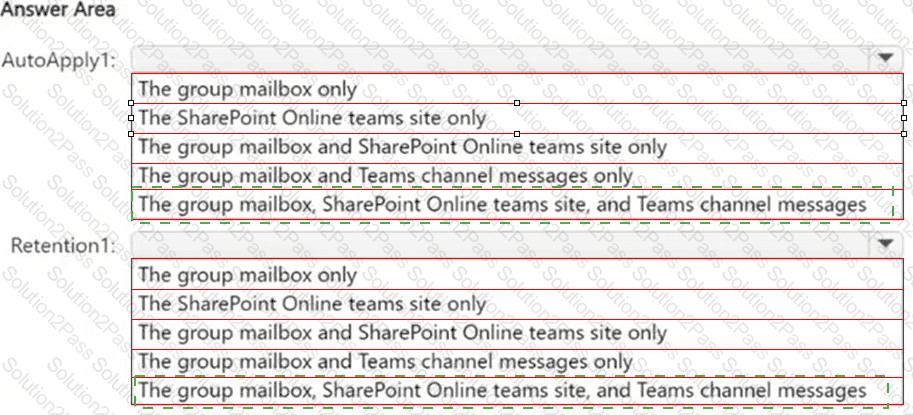
You have a Microsoft 365 E5 subscription that contains two Microsoft 365 groups named Group1 and Group2. Both groups use the following resources:
● A group mailbox
● Microsoft Teams channel messages
● A Microsoft SharePoint Online teams site
You create the objects shown in the following table.
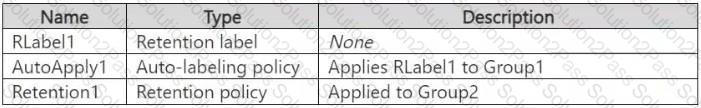
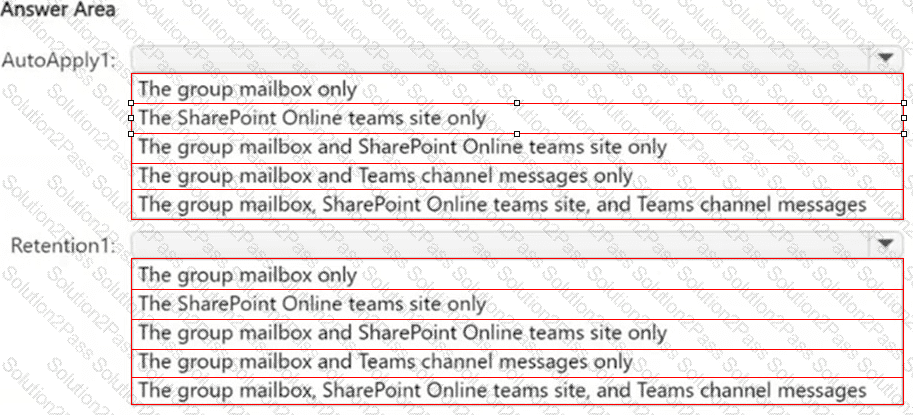
To which resources will AutoApply1 and Retention1 be applied? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a data loss prevention (DLP) policy configured for endpoints as shown in the following exhibit.

From a computer named Computer1, a user can sometimes upload files to cloud services and sometimes cannot. Other users experience the same issue.
What are two possible causes of the issue? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
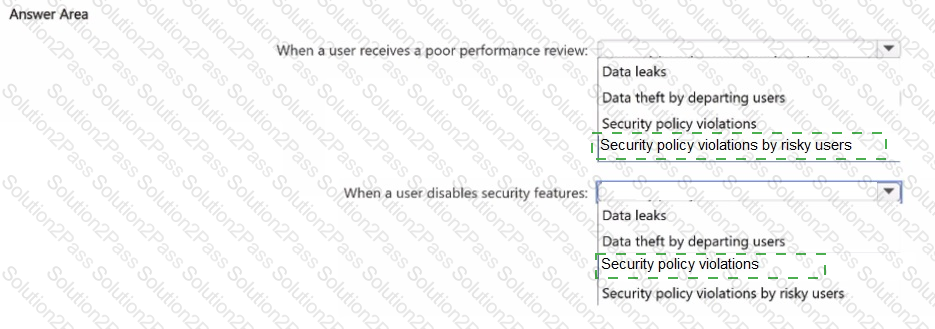
You plan to implement Microsoft Purview insider risk management.
You need to recommend policy templates that meet the following requirements:
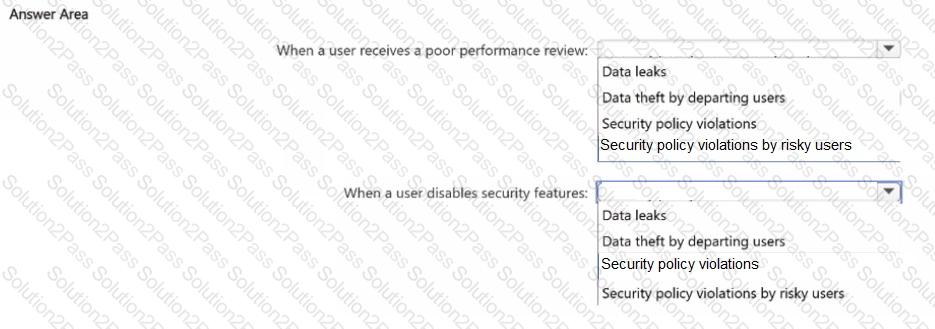
• Contain risk indicators and scoring for when a user receives a poor performance review
• Contain risk indicators and scoring for when a user disables security features on a device.
Which template should you use for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription. The subscription contains 500 devices that are onboarded to Microsoft Purview.
You select Activate Microsoft Purview Audit.
You need to ensure that you can track interactions between users and generative AI websites.
What should you deploy to the devices?
You have a Microsoft 365 subscription. You create a retention policy and apply the policy to Exchange Online mailboxes.
You need to ensure that the retention policy tags can be assigned to mailbox items as soon as possible.
What should you do?
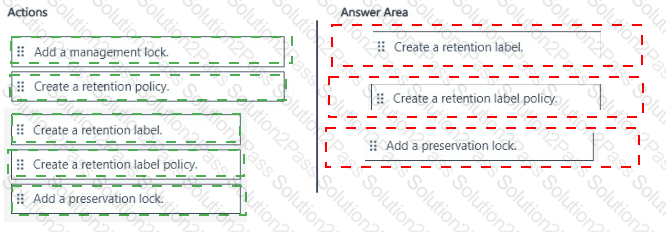
You have a Microsoft 365 tenant.
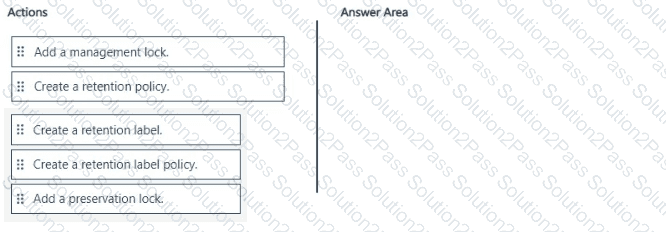
A new regulatory requirement states that all documents containing a patent ID be labeled, retained for 10 years, and then deleted. The policy used to apply the retention settings must never be disabled or deleted by anyone.
You need to implement the regulatory requirement.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft 365 E5 subscription that contains a trainable classifier named Trainable1.
You plan to create the items shown in the following table.
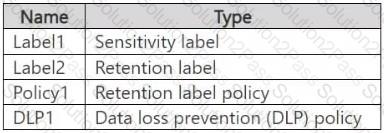
Which items can use Trainable 1?
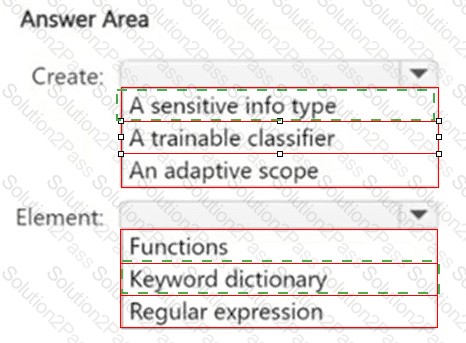
You have a Microsoft 365 E5 subscription.
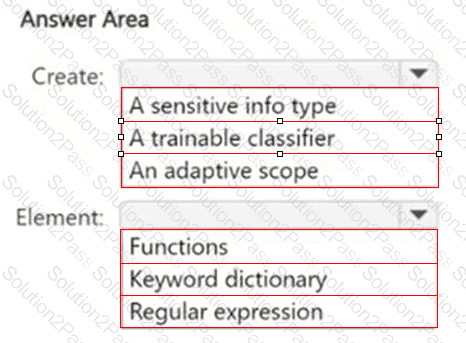
You have a file named Customer.csv that contains a list of 1,000 customer names.
You plan to use Customer.csv to classify documents stored in a Microsoft SharePoint Online library.
What should you create in the Microsoft Purview portal, and which type of element should you select? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
HOTSPOT
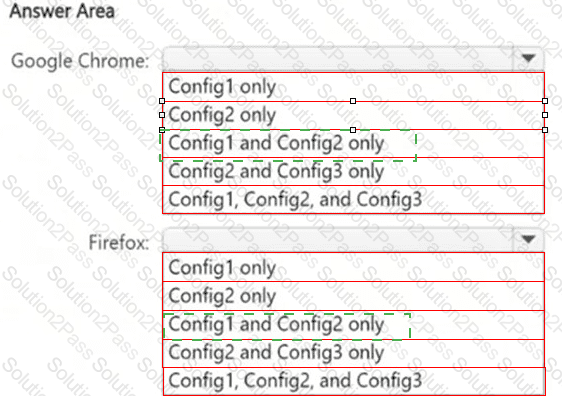
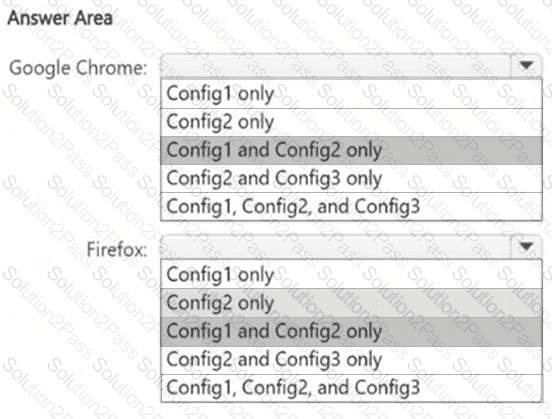
You have a Microsoft 365 E5 subscription that contains the device configurations shown in the following table.
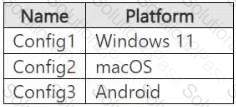
Each configuration uses either Google Chrome or Firefox as a default browser.
You need to implement Microsoft Purview and deploy the Microsoft Purview browser extension to the configurations.
To which configuration can each extension be deployed? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. Site1 contains the files shown in the following table.
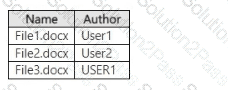
In the Microsoft Purview portal, you create a content search named Conlent1 and configure the search conditions as shown in the following exhibit.
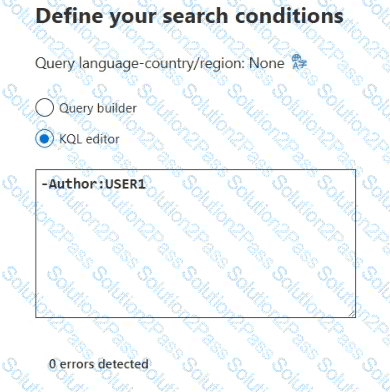
Which files will be returned by Content1?
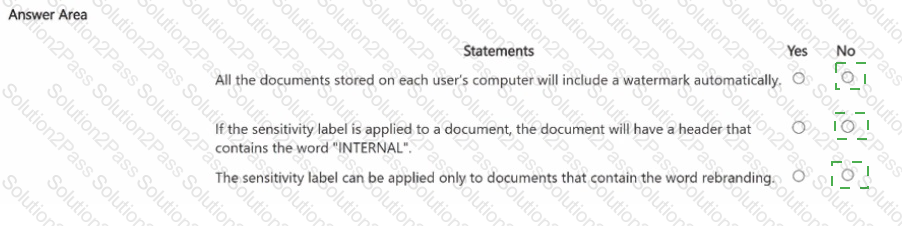
You have a Microsoft 365 sensitivity label that is published to all the users in your Microsoft Entra tenant as shown in the following exhibit.
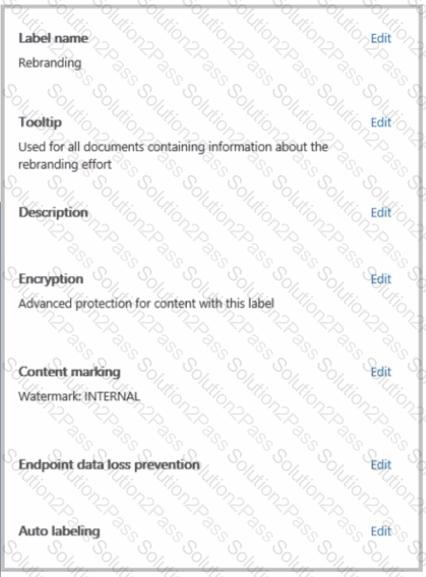
For each of the following statements, select Yes if the statement is true. Otherwise, select No
NOTE: Each correct selection is worth one point.
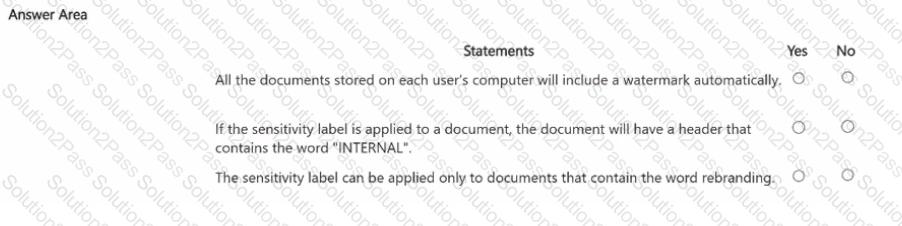
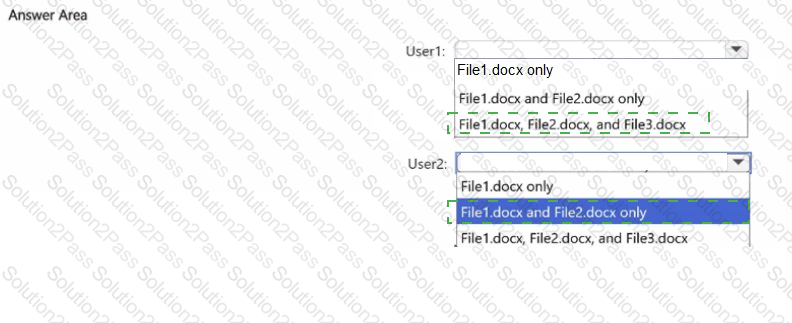
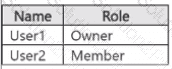
You have a Microsoft 365 E5 tenant that contains two users named User1, and User2 and a Microsoft SharePoint Online site named Site! as shown in the following exhibit.

For Site1, the users are assigned the roles shown in the following table.
You publish a retention label named Retention1 to Site1.
To which files can the users apply Retention!? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
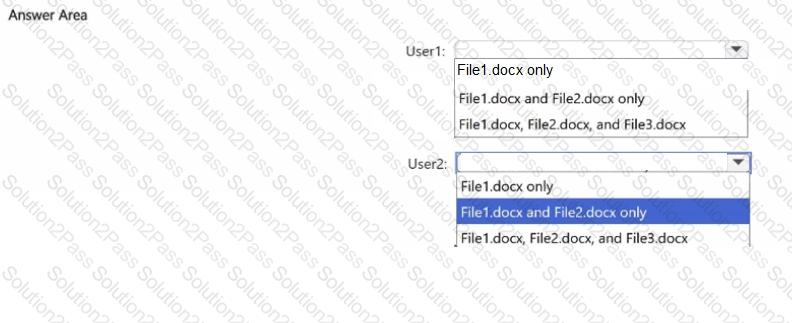
You have a Microsoft 365 E5 subscription that contains three users named User1, User2, and User3 and a file named Filetdocx.
You create a sensitivity label named Label1 as shown in the following exhibit.

You apply Label1 to File1.
For which users can Microsoft 365 Copilot summarize File1?
You have a Microsoft 365 E5 subscription.
You plan to use insider risk management to collect and investigate forensic evidence.
You need to enable forensic evidence capturing.
What should you do first?
You are configuring a data loss prevention (DLP) policy to report when credit card data is found on a Microsoft Entra joined Windows device.
You plan to use information from the policy to restrict the ability to copy the sensitive data to the clipboard.
What should you configure in the policy advanced DLP rule?
You have a Microsoft 365 tenant that is opt-in for trainable classifiers.
You need to ensure that a user named User1 can create custom trainable classifiers. The solution must use the principle of least privilege.
Which role should you assign to User1?
You have a Microsoft 365 subscription.
You create a new trainable classifier.
You need to train the classifier.
Which source can you use to train the classifier?
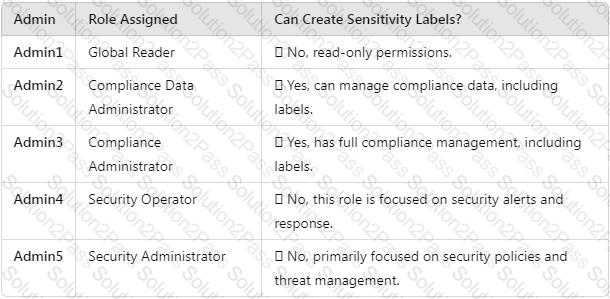
You need to meet the technical requirements for the creation of the sensitivity labels.
To which user or users must you assign the Sensitivity Label Administrator role?