NSK101 Netskope Certified Cloud Security Administrator (NCCSA) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Netskope NSK101 Netskope Certified Cloud Security Administrator (NCCSA) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A company user cannot open a sports news site. You want to review the category of the website and see how the rules are applied even though this category is allowed. In this scenario, which action will accomplish this task?
Your customer asks you to secure all Web traffic as part of the initial configuration. In the Netskope platform, which statement is correct in this scenario?
You want to see the actual data that caused the policy violation within a DLP Incident view.
In this scenario, which profile must be set up?
You want to block access to sites that use self-signed certificates. Which statement is true in this scenario?
The Netskope deployment for your organization is deployed in CASB-only mode. You want to view dropbox.com traffic but do not see it when using SkopeIT.
In this scenario, what are two reasons for this problem? (Choose two.)
Which two traffic steering configurations are supported by Netskope? (Choose two.)
What are two characteristics of Netskope's Private Access Solution? (Choose two.)
Which three components make up the Borderless SD-WAN solution? (Choose three)
Click the Exhibit button.

You configured a set of Cloud Firewall policies as shown in the exhibit and changed your Steering Configuration to All Traffic for Group A and Group B. Users in Group A report that they are unable to access a third-party server using TCP port 3389. Referring to the exhibit, which action correctly describes how you would allow these connections without allowing unnecessary access?
A new customer is concerned about performance, especially with respect to Microsoft 365. They have offices in 20 countries around the world and their workforce is mostly mobile.
In this scenario, which two statements about NewEdge would align with the customer's requirements? (Choose two.)
As an administrator, you are investigating an increase in the number of incidents related to compromised credentials. You are using the Netskope Compromised Credentials feature on your tenant to assess the situation. Which insights would you find when using this feature? (Choose two)
In the Skope IT interface, which two event tables would be used to label a cloud application instance? (Choose two.)
How does a cloud security solution achieve visibility into TLS/SSL-protected Web traffic?
You want to use an out-of-band API connection into your sanctioned Microsoft 365 OneDrive for Business application to find sensitive content, enforce near real-time policy controls, and quarantine malware.
In this scenario, which primary function in the Netskope platform would you use to connect your application to Netskope?
You investigate a suspected malware incident and confirm that it was a false alarm.
You have an issue with the Netskope client connecting to the tenant.
In this scenario, what are two ways to collect the logs from the client machine? (Choose two.)
You are working with a large retail chain and have concerns about their customer data. You want to protect customer credit card data so that it is never exposed in transit or at rest. In this scenario, which regulatory compliance standard should be used to govern this data?
Exhibit
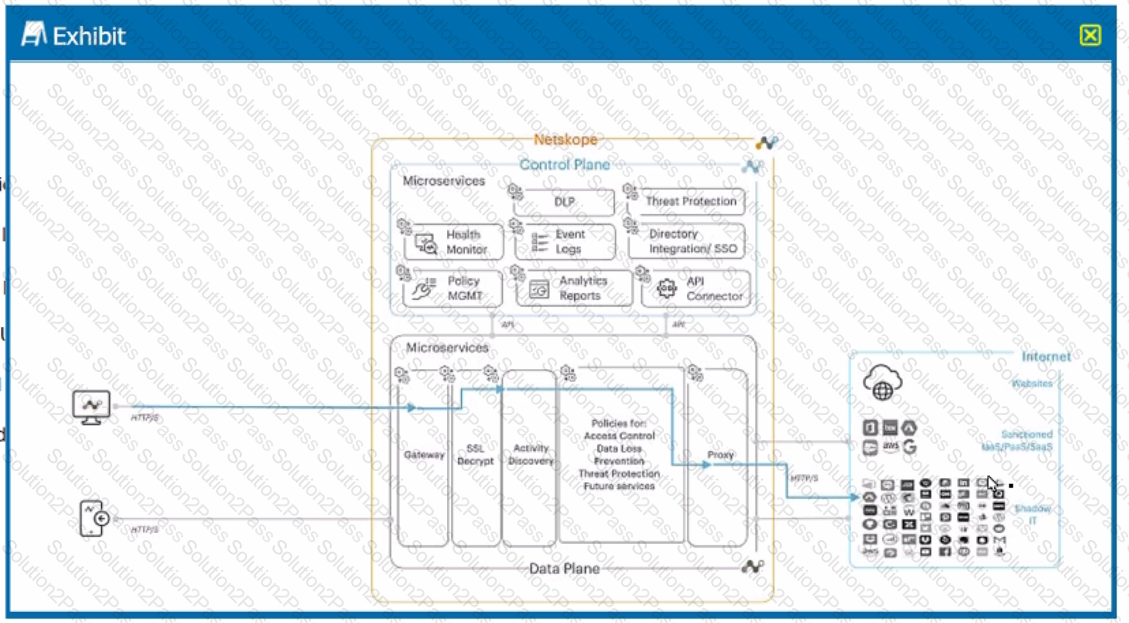
A user is connected to a cloud application through Netskope's proxy.
In this scenario, what information is available at Skope IT? (Choose three.)
