1z0-588 Oracle Hyperion Data Relationship Management Essentials Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Oracle 1z0-588 Oracle Hyperion Data Relationship Management Essentials certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Per the example:
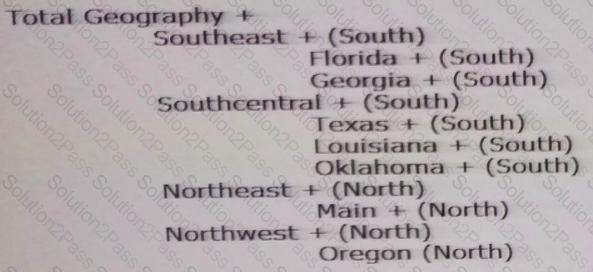
You have a property definition called Region with possible valid values "east", "West", "North", and "South".
How do you set this property for end users?
You are ready to run batch validations against a version before exporting to target systems. Identify two valid version statuses that allow batch validations to be run and issues to be corrected before the exports to target systems.
You want an import to stop if a duplicate node is found. How do you do this?
Which filters can you apply to narrow the transaction history results when searching the transaction history?
Per the example:
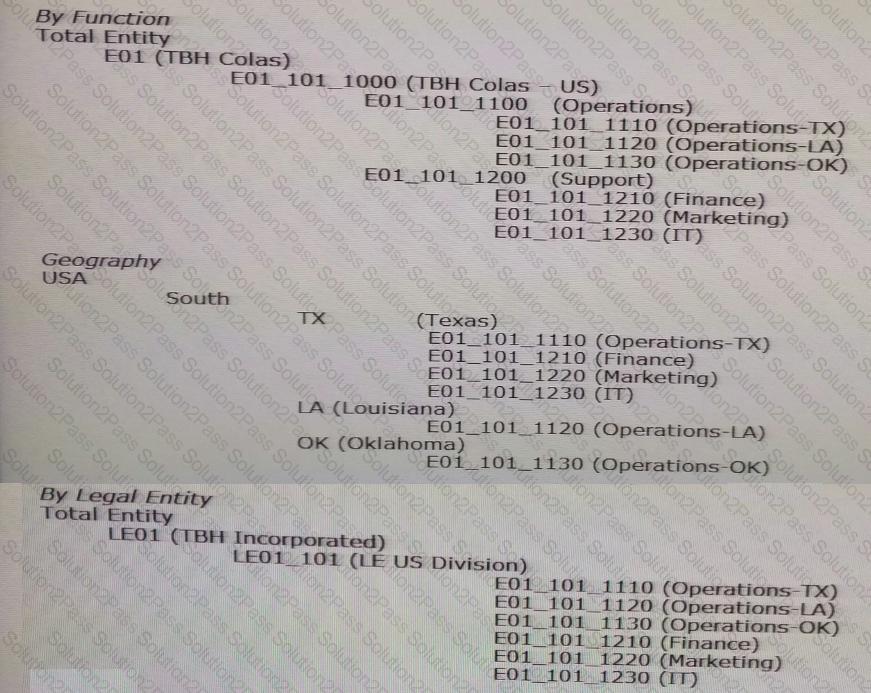
You have three entity hierarchies within the same version. The Essbase Storage property is set to local. The Alias Description property is set to Global. Identify the true statements.
1. If the Essbase administrator changes the Essbase Storage property from "Stored" to "Dynamic" for a node in the primary hierarchy, the property will change for all hierarchies.
2. If the Essbase administrator changes the Alias Description property for a node it\ the primary hierarchy, the property will change for all hierarchies,
3. If the Ecssbase administrator changes the Alias Description property for a node in the non- primary hierarchy, the property will not change for other hierarchies.
4. If the Essbase administrator changes the Alias Description or Essbase Storage property to a node in a hierarchy, the values will not update in the other hierarchies unless the DisableSharedNodes is set to False.
5. Because the Alias Description property is set to Global, the property will update across all versions for the node.
Identify the true statements about the DRM Change Tracking properties.
You have built a validation to ensure that a hierarchy has no more than 20,000 nodes. What is the correct validation level?
You maintain the Market hierarchy in DRM.
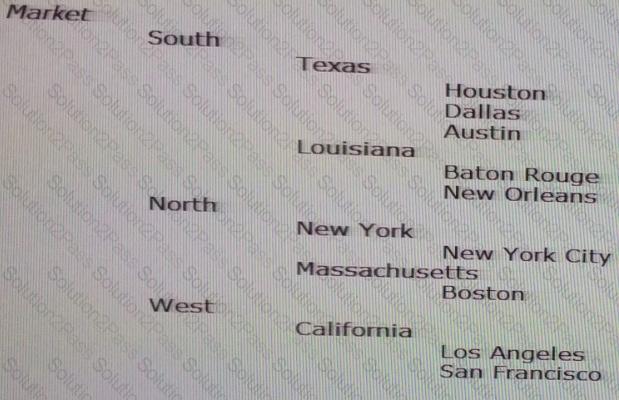
A target system needs an alternate hierarchy of the Market dimension that contains the lowest level of markets (city) rolling up by market size (nodes Large, Medium, and Small).
Identify the ways to meet this requirement in DRM.
1. Create a property category called "Market Size" and populate the values as "Large", "Medium", and "Small"
2. Create a property called "Market Size" and populate the values as "Large", "Medium", and "Small"
3. Create a node type called "Market Size" and populate the values as "Large", "Medium", and "Small"
4. Create an alternate hierarchy in the Market dimension with nodes "Large", "Medium", and "Small". Add cities as shared nodes under the appropriate Market Size nodes.
Which three statements are true about the stakeholders in a DRM implementation?
New cost centers are added to the Entity hierarchy nightly from the ERP system. Identify the two true statements about the ERP system.
Your ETL must leverage a mapping maintained in DRM. How can your ETL access the mapping data from DRM?
Select the three options that will complete this sentence to make it a true statement:
"Batch validations in DRM may be run for a_____."
Identify the three benefits of adding a standard prefix to a related set of property definitions.
Identify the three true statements about the Initial Data Load process when you first implement DRM.
Identify the two true statements about user permissions.
Per the example:
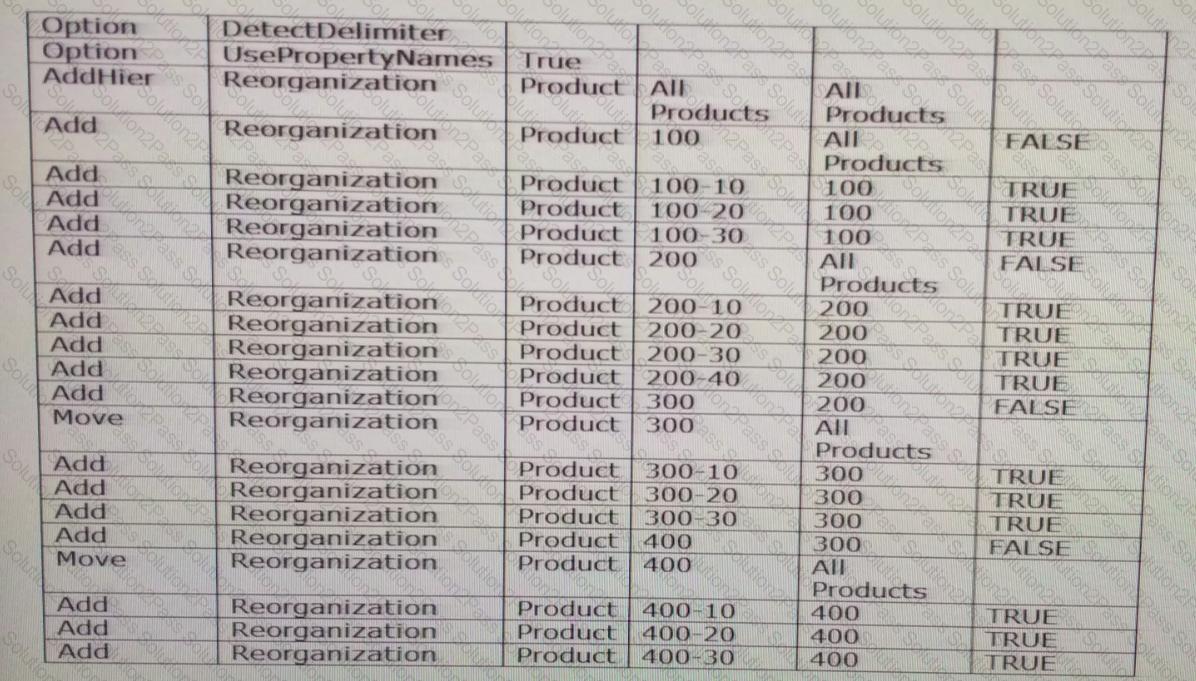
What are the three outcomes after running the action script?
select the three valid web service methods from DRM workflow actions.
Identify the three true statements.
Choose three validations that are often implemented for downstream systems.
Identify the three true statements about Workflow in DRM.
