ISO-IEC-27001-Lead-Auditor PECB Certified ISO/IEC 27001 2022 Lead Auditor exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your PECB ISO-IEC-27001-Lead-Auditor PECB Certified ISO/IEC 27001 2022 Lead Auditor exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Total 418 questions
You are an experienced audit team leader guiding an auditor in training.
Your team is currently conducting a third-party surveillance audit of an organisation that stores data on behalf of external clients. The auditor in training has been tasked with reviewing the ORGANISATIONAL controls listed in the Statement of Applicability (SoA) and implemented at the site.
Select four controls from the following that would you expect the auditor in training to review.
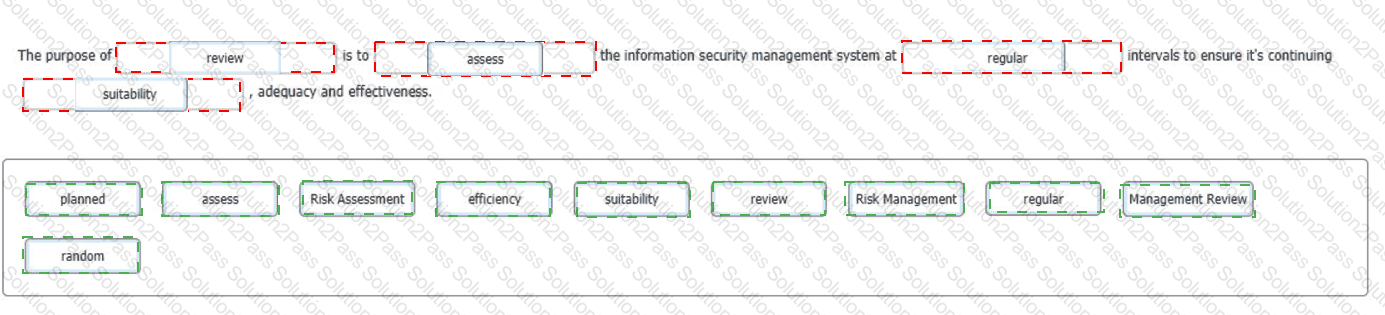
You are an experienced ISMS audit team leader, talking to an Auditor in training who has been assigned to your audit team. You want to ensure that they understand the importance of the Check stage of the Plan-Do-Check-Act cycle in respect of the operation of the information security management system.
You do this by asking him to select the words that best complete the sentence:
To complete the sentence with the best word(s), click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.
Scenario 8
Trustingo has been providing banking and financial services in Estonia since 2010. The company has a network of 30 branches with over 100 ATMs nationwide. To meet strict data security and privacy regulations, Trustingo implemented an information security management system (ISMS) based on ISO/IEC 27001, ensuring better security, improved risk management, and compliance with legal requirements.
Nine months after the successful implementation of the ISMS, Trustingo decided to pursue certification for their ISMS based on ISO/IEC 27001 by an independent certification body. The certification audit included Trustingo's systems, processes, and technologies.
The audit team conducted the Stage 1 and Stage 2 audits jointly, and several nonconformities were detected. The first nonconformity was related to Trustingo’s labeling of information. The company had an information classification scheme but no information labeling procedure. As a result, documents requiring the same level of protection would be labeled differently.
The nonconformity also impacted media handling. The audit team used sampling and concluded that 50 of 200 removable media stored sensitive information mistakenly classified as confidential. According to the classification scheme, confidential information may be stored on removable media, whereas sensitive information is strictly prohibited.
The audit team drafted the nonconformity report and discussed conclusions with Trustingo’s representatives. Trustingo accepted the audit team leader’s proposed solution and addressed the nonconformities by drafting an information labeling procedure and updating the removable media procedure.
Two weeks after audit completion, Trustingo submitted a general corrective action plan. Although it addressed the nonconformities, it lacked detailed action steps and system-specific impacts. As a result, Trustingo received an unfavorable certification recommendation.
Question
Which action in Scenario 8 is unacceptable in an external audit?
You are carrying out a third-party surveillance audit of a client's ISMS. You are currently in the secure storage area of the data centre where the organisation's customers are able to temporarily locate equipment coming into or going out of the site. The equipment is contained within locked cabinets and each cabinet is allocated to a single, specific client.
Out of the corner of your eye you spot movement near the external door of the storage area. This is followed by a loud noise. You ask the guide what is going on. They tell you that recent high rainfall has raised local river levels and caused an infestation of rats. The noise was a specialist pest control stunning device being triggered. You check the device in the corner and find there is a large immobile rat contained within it.
What three actions would be appropriate to take next?
The auditor used sampling to ensure that event logs recording information security events are maintained and regularly reviewed. Sampling was based on the audit objectives, whereas the sample selection process was based on the probability theory. What type of sampling was used?
Scenario 6: Cyber ACrypt is a cybersecurity company that provides endpoint protection by offering anti-malware and device security, asset life cycle management, and device encryption. To validate its ISMS against ISO/IEC 27001 and demonstrate its commitment to cybersecurity excellence, the company underwent a meticulous audit process led by John, the appointed audit team leader.
Upon accepting the audit mandate, John promptly organized a meeting to outline the audit plan and team roles This phase was crucial for aligning the team with the audit's objectives and scope However, the initial presentation to Cyber ACrypt’s staff revealed a significant gap in understanding the audit's scope and objectives, indicating potential readiness challenges within the company
As the stage 1 audit commenced, the team prepared for on-site activities. They reviewed Cyber ACrypt's documented information, including the information security policy and operational procedures ensuring each piece conformed to and was standardized in format with author identification, production date, version number, and approval date Additionally, the audit team ensured that each document contained the information required by the respective clause of the standard This phase revealed that a detailed audit of the documentation describing task execution was unnecessary, streamlining the process and focusing the team's efforts on critical areas During the phase of conducting on-site activities, the team evaluated management responsibility for the Cyber Acrypt's policies This thorough examination aimed to ascertain continual improvement and adherence to ISMS requirements Subsequently, in the document, the stage 1 audit outputs phase, the audit team meticulously documented their findings, underscoring their conclusions regarding the fulfillment of the stage 1 objectives. This documentation was vital for the audit team and Cyber ACrypt to understand the preliminary audit outcomes and areas requiring attention.
The audit team also decided to conduct interviews with key interested parties. This decision was motivated by the objective of collecting robust audit evidence to validate the management system’s compliance with ISO/IEC 27001 requirements. Engaging with interested parties across various levels of Cyber ACrypt provided the audit team with invaluable perspectives and an understanding of the ISMS's implementation and effectiveness.
The stage 1 audit report unveiled critical areas of concern. The Statement of Applicability (SoA) and the ISMS policy were found to be lacking in several respects, including insufficient risk assessment, inadequate access controls, and lack of regular policy reviews. This prompted Cyber ACrypt to take immediate action to address these shortcomings. Their prompt response and modifications to the strategic documents reflected a strong commitment to achieving compliance.
The technical expertise introduced to bridge the audit team's cybersecurity knowledge gap played a pivotal role in identifying shortcomings in the risk assessment methodology and reviewing network architecture. This included evaluating firewalls, intrusion detection and prevention systems, and other network security measures, as well as assessing how Cyber ACrypt detects, responds to, and recovers from external and internal threats. Under John's supervision, the technical expert communicated the audit findings to the representatives of Cyber ACrypt. However, the audit team observed that the expert s objectivity might have been compromised due to receiving consultancy fees from the auditee. Considering the behavior of the technical expert during the audit, the audit team leader decided to discuss this concern with the certification body.
Based on the scenario above, answer the following question:
Question:
According to Scenario 6, Cyber ACrypt modified the SoA and the ISMS policy after the Stage 1 audit report. How do you define this situation?
Which one of the following options is the definition of an interested party?
A third party can appeal to an organisation when it perceives itself to be affected by a decision or activity
A marketing agency has developed its own risk assessment approach as part of the ISMS implementation. Is this acceptable?
AppFolk, a software development company, is seeking certification against ISO/IEC 27001. In the initial phases of the external audit, the certification body in discussion with the company excluded the marketing division from the audit scope, although they stated in their ISMS scope that the whole company is included. Is this acceptable?
Costs related to nonconformities and failures to comply with legal and contractual requirements are assessed when defining:
Scenario 6: Cyber ACrypt is a cybersecurity company that provides endpoint protection by offering anti-malware and device security, asset life cycle management, and device encryption. To validate its ISMS against ISO/IEC 27001 and demonstrate its commitment to cybersecurity excellence, the company underwent a meticulous audit process led by John, the appointed audit team leader.
Upon accepting the audit mandate, John promptly organized a meeting to outline the audit plan and team roles This phase was crucial for aligning the team with the audit's objectives and scope However, the initial presentation to Cyber ACrypt’s staff revealed a significant gap in understanding the audit's scope and objectives, indicating potential readiness challenges within the company
As the stage 1 audit commenced, the team prepared for on-site activities. They reviewed Cyber ACrypt's documented information, including the information security policy and operational procedures ensuring each piece conformed to and was standardized in format with author identification, production date, version number, and approval date Additionally, the audit team ensured that each document contained the information required by the respective clause of the standard This phase revealed that a detailed audit of the documentation describing task execution was unnecessary, streamlining the process and focusing the team's efforts on critical areas During the phase of conducting on-site activities, the team evaluated management responsibility for the Cyber Acrypt's policies This thorough examination aimed to ascertain continual improvement and adherence to ISMS requirements Subsequently, in the document, the stage 1 audit outputs phase, the audit team meticulously documented their findings, underscoring their conclusions regarding the fulfillment of the stage 1 objectives. This documentation was vital for the audit team and Cyber ACrypt to understand the preliminary audit outcomes and areas requiring attention.
The audit team also decided to conduct interviews with key interested parties. This decision was motivated by the objective of collecting robust audit evidence to validate the management system’s compliance with ISO/IEC 27001 requirements. Engaging with interested parties across various levels of Cyber ACrypt provided the audit team with invaluable perspectives and an understanding of the ISMS's implementation and effectiveness.
The stage 1 audit report unveiled critical areas of concern. The Statement of Applicability (SoA) and the ISMS policy were found to be lacking in several respects, including insufficient risk assessment, inadequate access controls, and lack of regular policy reviews. This prompted Cyber ACrypt to take immediate action to address these shortcomings. Their prompt response and modifications to the strategic documents reflected a strong commitment to achieving compliance.
The technical expertise introduced to bridge the audit team's cybersecurity knowledge gap played a pivotal role in identifying shortcomings in the risk assessment methodology and reviewing network architecture. This included evaluating firewalls, intrusion detection and prevention systems, and other network security measures, as well as assessing how Cyber ACrypt detects, responds to, and recovers from external and internal threats. Under John's supervision, the technical expert communicated the audit findings to the representatives of Cyber ACrypt. However, the audit team observed that the expert s objectivity might have been compromised due to receiving consultancy fees from the auditee. Considering the behavior of the technical expert during the audit, the audit team leader decided to discuss this concern with the certification body.
Based on the scenario above, answer the following question:
Question:
Which criteria for evaluating documented information was NOT validated by the audit team? (Refer to Scenario 6)
You are performing an ISMS initial certification audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to conduct the closing meeting. During the final audit team meeting, as an audit team leader, you agree to report 2 minor nonconformities and 1 opportunity for improvement as below:
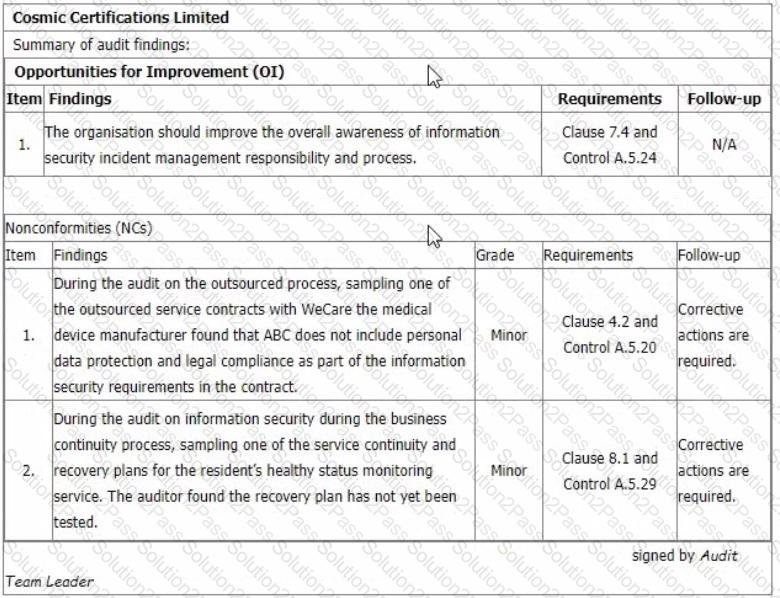
Select one option of the recommendation to the audit programme manager you are going to advise to the auditee at the closing meeting.
Scenario 3: NightCore is a multinational technology company based in the United States that focuses on e-commerce, cloud computing, digital streaming, and artificial intelligence. After having an information security management system (ISMS) implemented for over 8 months, they contracted a certification body to conduct a third party audit in order to get certified against ISO/IEC 27001.
The certification body set up a team of seven auditors. Jack, the most experienced auditor, was assigned as the audit team leader. Over the years, he received many well known certifications, such as the ISO/IEC 27001 Lead Auditor, CISA, CISSP, and CISM.
Jack conducted thorough analyses on each phase of the ISMS audit, by studying and evaluating every information security requirement and control that was implemented by NightCore. During stage 2 audit. Jack detected several nonconformities. After comparing the number of purchased invoices for software licenses with the software inventory, Jack found out that the company has been using the illegal versions of a software for many computers. He decided to ask for an explanation from the top management about this nonconformity and see whether they were aware about this. His next step was to audit NightCore's IT Department. The top management assigned Tom, NightCore's system administrator, to act as a guide and accompany Jack and the audit team toward the inner workings of their system and their digital assets infrastructure.
While interviewing a member of the Department of Finance, the auditors discovered that the company had recently made some unusual large transactions to one of their consultants. After gathering all the necessary details regarding the transactions. Jack decided to directly interview the top management.
When discussing about the first nonconformity, the top management told Jack that they willingly decided to use a copied software over the original one since it was cheaper. Jack explained to the top management of NightCore that using illegal versions of software is against the requirements of ISO/IEC 27001 and the national laws and regulations. However, they seemed to be fine with it.
Several months after the audit, Jack sold some of NightCore's information that he collected during the audit for a huge amount of money to competitors of NightCore.
Based on this scenario, answer the following question:
Based on audit principles, should Jack contact the certification body regarding the second nonconformity? Refer to scenario 3.
Scenario 9: Techmanic is a Belgian company founded in 1995 and currently operating in Brussels. It provides IT consultancy, software design, and hardware/software services, including deployment and maintenance. The company serves sectors like public services, finance, telecom, energy, healthcare, and education. As a customer-centered company, it prioritizes strong client relationships and leading security practices.
Techmanic has been ISO/IEC 27001 certified for a year and regards this certification with pride. During the certification audit, the auditor found some inconsistencies in its ISMS implementation. Since the observed situations did not affect the capability of its ISMS to achieve the intended results, Techmanic was certified after auditors followed up on the root cause analysis and corrective actions remotely During that year, the company added hosting to its list of services and requested to expand its certification scope to include that area The auditor in charge approved the request and notified Techmanic that the extension audit would be conducted during the surveillance audit
Techmanic underwent a surveillance audit to verify its iSMS's continued effectiveness and compliance with ISO/IEC 27001. The surveillance audit aimed to ensure that Techmanic’s security practices, including the recent addition of hosting services, aligned seamlessly with the rigorous requirements of the certification
The auditor strategically utilized the findings from previous surveillance audit reports in the recertification activity with the purpose of replacing the need for additional recertification audits, specifically in the IT consultancy sector. Recognizing the value of continual improvement and learning from past assessments. Techmanic implemented a practice of reviewing previous surveillance audit reports. This proactive approach not only facilitated identifying and resolving potential nonconformities but also aimed to streamline the recertification process in the IT consultancy sector.
During the surveillance audit, several nonconformities were found. The ISMS continued to fulfill the ISO/IEC 27001*s requirements, but Techmanic failed to resolve the nonconformities related to the hosting services, as reported by its internal auditor. In addition, the internal audit report had several inconsistencies, which questioned the independence of the internal auditor during the audit of hosting services. Based on this, the extension certification was not granted. As a result. Techmanic requested a transfer to another certification body. In the meantime, the company released a statement to its clients stating that the ISO/IEC 27001 certification covers the IT services, as well as the hosting services.
Based on the scenario above, answer the following question:
Question:
According to ISO/IEC 17021-1, what is the purpose of surveillance audits?
Which four of the following statements about audit reports are true?
You are an experienced ISMS audit team leader guiding an auditor in training. You are testing her understanding of follow-up audits by asking her a series of questions to which the answer is either "true* or 'false'. Which four of the following questions should the answer be true"'
You ask the IT Manager why the organisation still uses the mobile app while personal data
encryption and pseudonymisation tests failed. Also, whether the Service Manager is authorised to approve the test.
The IT Manager explains the test results should be approved by him according to the software security management procedure. The reason why the encryption and pseudonymisation functions failed is that these functions heavily slowed down the system and service performance. An extra 150% of resources are needed to cover this. The Service Manager agreed that access control is good enough and acceptable. That's why the Service Manager signed the approval.
You are preparing the audit findings. Select the correct option.
There is a nonconformity (NC). The organisation and developer do not perform acceptance tests. (Relevant to clause 8.1, control A.8.29)
The scope of an organization certified against ISO/IEC 27001 states that they provide editing and web hosting services. However, due to some changes in the organization, the technical support related to the web hosting services has been outsourced. Should a change in the scope be initiated in this case?
Audit methods can be either with or without interaction with individuals representing the auditee. Which two of the following methods are with interaction?
Which two of the following statements are true?
The benefits of implementing an ISMS primarily result from a reduction in information security risks
Total 418 questions