ISO-IEC-27001-Lead-Auditor PECB Certified ISO/IEC 27001 2022 Lead Auditor exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your PECB ISO-IEC-27001-Lead-Auditor PECB Certified ISO/IEC 27001 2022 Lead Auditor exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Scenario 3
NightCore, a multinational technology enterprise headquartered in the United States, specializes in e-commerce, cloud computing, digital streaming, and artificial intelligence (AI). After having an information security management system (ISMS) implemented for over a year, NightCore contracted a certification body to perform an audit for ISO/IEC 27001 certification.
The certification body formed a team of five auditors, with Jack as a team leader. Jack is renowned for his extensive auditing experience in risk management, information security controls, and incident management. His skill set aligns well with the requirements of auditing principles and processes, enabling him to effectively comprehend the audit scope and apply relevant criteria effectively. Jack also demonstrates a solid understanding of NightCore’s organizational structure, purpose, and management practices, as well as the statutory and regulatory requirements applicable to its activities.
The audit carried out by the audit team followed a rational method to reach reliable and reproducible conclusions systematically. The audit team recognized that only information capable of being verified to some extent should be considered valid evidence. In some rare instances during the audit where the verification of certain information posed challenges and where its degree of verifiability was low, the auditors exercised their professional judgment to assess the reliability and determine the level of reliance that could be placed on such evidence.
During the audit, the auditors documented their observations and inspection notes regarding the operational planning and control of NightCore’s ISMS operations. They also recorded observations of NightCore’s inventory of information and associated assets. Additionally, the auditors reviewed the configuration of firewalls implemented to secure connections to network services.
As the audit approached its final stages, NightCore’s commitment to upholding the highest levels of information security became evident. With ISO/IEC 27001 certification within reach, NightCore is well-positioned to achieve ISO/IEC 27001 certification, enhancing its reputation in the technology sector.
Question
Does Jack possess the necessary knowledge and skills required of an auditor? Refer to Scenario 3.
During a Stage 1 audit opening meeting, the Management System Representative (MSR) asks to extend the audit scope to include a new site overseas which they have expanded into since the certification application was made.
Select two options for how the auditor should respond.
Advise the MSR that an extension of the scope may be incorporated but will have to go through established procedures
Scenario 9: Techmanic is a Belgian company founded in 1995 and currently operating in Brussels. It provides IT consultancy, software design, and hardware/software services, including deployment and maintenance. The company serves sectors like public services, finance, telecom, energy, healthcare, and education. As a customer-centered company, it prioritizes strong client relationships and leading security practices.
Techmanic has been ISO/IEC 27001 certified for a year and regards this certification with pride. During the certification audit, the auditor found some inconsistencies in its ISMS implementation. Since the observed situations did not affect the capability of its ISMS to achieve the intended results, Techmanic was certified after auditors followed up on the root cause analysis and corrective actions remotely During that year, the company added hosting to its list of services and requested to expand its certification scope to include that area The auditor in charge approved the request and notified Techmanic that the extension audit would be conducted during the surveillance audit
Techmanic underwent a surveillance audit to verify its iSMS's continued effectiveness and compliance with ISO/IEC 27001. The surveillance audit aimed to ensure that Techmanic’s security practices, including the recent addition of hosting services, aligned seamlessly with the rigorous requirements of the certification
The auditor strategically utilized the findings from previous surveillance audit reports in the recertification activity with the purpose of replacing the need for additional recertification audits, specifically in the IT consultancy sector. Recognizing the value of continual improvement and learning from past assessments. Techmanic implemented a practice of reviewing previous surveillance audit reports. This proactive approach not only facilitated identifying and resolving potential nonconformities but also aimed to streamline the recertification process in the IT consultancy sector.
During the surveillance audit, several nonconformities were found. The ISMS continued to fulfill the ISO/IEC 27001*s requirements, but Techmanic failed to resolve the nonconformities related to the hosting services, as reported by its internal auditor. In addition, the internal audit report had several inconsistencies, which questioned the independence of the internal auditor during the audit of hosting services. Based on this, the extension certification was not granted. As a result. Techmanic requested a transfer to another certification body. In the meantime, the company released a statement to its clients stating that the ISO/IEC 27001 certification covers the IT services, as well as the hosting services.
Based on the scenario above, answer the following question:
Question:
What action should be taken regarding Techmanic’s certification?
Question:
What is the main difference between qualitative and quantitative evidence?
Scenario 7: Lawsy is a leading law firm with offices in New Jersey and New York City. It has over 50 attorneys offering sophisticated legal services to clients in business and commercial law, intellectual property, banking, and financial services. They believe they have a comfortable position in the market thanks to their commitment to implement information security best practices and remain up to date with technological developments.
Lawsy has implemented, evaluated, and conducted internal audits for an ISMS rigorously for two years now. Now, they have applied for ISO/IEC 27001 certification to ISMA, a well-known and trusted certification body.
During stage 1 audit, the audit team reviewed all the ISMS documents created during the implementation. They also reviewed and evaluated the records from management reviews and internal audits.
Lawsy submitted records of evidence that corrective actions on nonconformities were performed when necessary, so the audit team interviewed the internal auditor. The interview validated the adequacy and frequency of the internal audits by providing detailed insight into the internal audit plan and procedures.
The audit team continued with the verification of strategic documents, including the information security policy and risk evaluation criteria. During the information security policy review, the team noticed inconsistencies between the documented information describing governance framework (i.e., the information security policy) and the procedures.
Although the employees were allowed to take the laptops outside the workplace, Lawsy did not have procedures in place regarding the use of laptops in such cases. The policy only provided general information about the use of laptops. The company relied on employees' common knowledge to protect the confidentiality and integrity of information stored in the laptops. This issue was documented in the stage 1 audit report.
Upon completing stage 1 audit, the audit team leader prepared the audit plan, which addressed the audit objectives, scope, criteria, and procedures.
During stage 2 audit, the audit team interviewed the information security manager, who drafted the information security policy. He justified the Issue identified in stage 1 by stating that Lawsy conducts mandatory information security training and awareness sessions every three months.
Following the interview, the audit team examined 15 employee training records (out of 50) and concluded that Lawsy meets requirements of ISO/IEC 27001 related to training and awareness. To support this conclusion, they photocopied the examined employee training records.
Based on the scenario above, answer the following question:
Should the auditor archive the copies of employee training records after the completion of the audit? Refer to scenario 7.
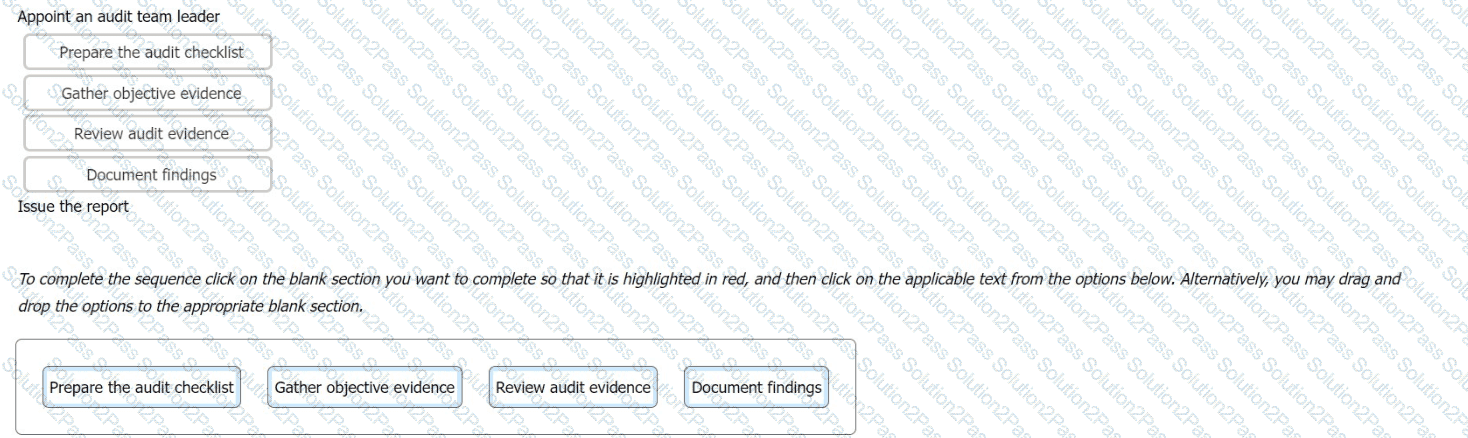
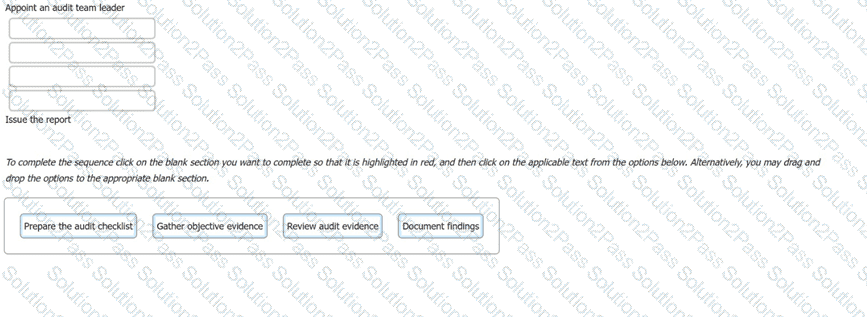
The following options are key actions involved in a first-party audit. Order the stages to show the sequence in which the actions should take place.
Which two of the following options do not participate in a second-party audit to ISO/IEC 27001?
Scenario:
After an information security incident, an organization created a comprehensive backup procedure involving regular, automated backups of all critical data to offsite storage locations. By doing so, which principle of information security is the organization applying in this case?
You are conducting an ISMS audit in the despatch department of an international logistics organisation that provides shipping services to large organisations including local hospitals and government offices. Parcels typically contain pharmaceutical products, biological samples, and documents such as passports and driving licences. You note that the company records show a very large number of returned items with causes including misaddressed labels and, in 15% of cases, two or more labels for different addresses for the one package. You are interviewing the Shipping Manager (SM).
You: Are items checked before being dispatched?
SM: Any obviously damaged items are removed by the duty staff before being dispatched, but the small profit margin makes it uneconomic to implement a formal checking process.
You: What action is taken when items are returned?
SM: Most of these contracts are relatively low value, therefore it has been decided that it is easier and more convenient to simply reprint the label and re-send individual parcels than it is to implement an investigation.
You raise a nonconformity against ISO 27001:2022 based on the lack of control of the labelling process.
At the closing meeting, the Shipping Manager issues an apology to you that his comments may have been misunderstood. He says that he did not realise that there is a background IT process that automatically checks that the right label goes onto the right parcel otherwise the parcel is ejected at labelling. He asks that you withdraw your nonconformity.
Select three options of the correct responses that you as the audit team leader would make to the request of the Shipping Manager.
Which two of the following phrases would apply to "act" in relation to the Plan-Do-Check-Act cycle for a business process?
You are an ISMS auditor conducting a third-party surveillance audit of a telecom's provider. You are in the equipment staging room where network switches are pre-programmed before being despatched to clients. You note that recently there has been a significant increase in the number of switches failing their initial configuration test and being returned for reprogramming.
You ask the Chief Tester why and she says, 'It's a result of the recent ISMS upgrade'. Before the upgrade each technician had their own hard copy work instructions. Now, the eight members of my team have to share two laptops to access the clients' configuration instructions online. These delays put pressure on the technicians, resulting in more mistakes being made'.
Based solely on the information above, which clause of ISO to raise a nonconformity against' Select one.
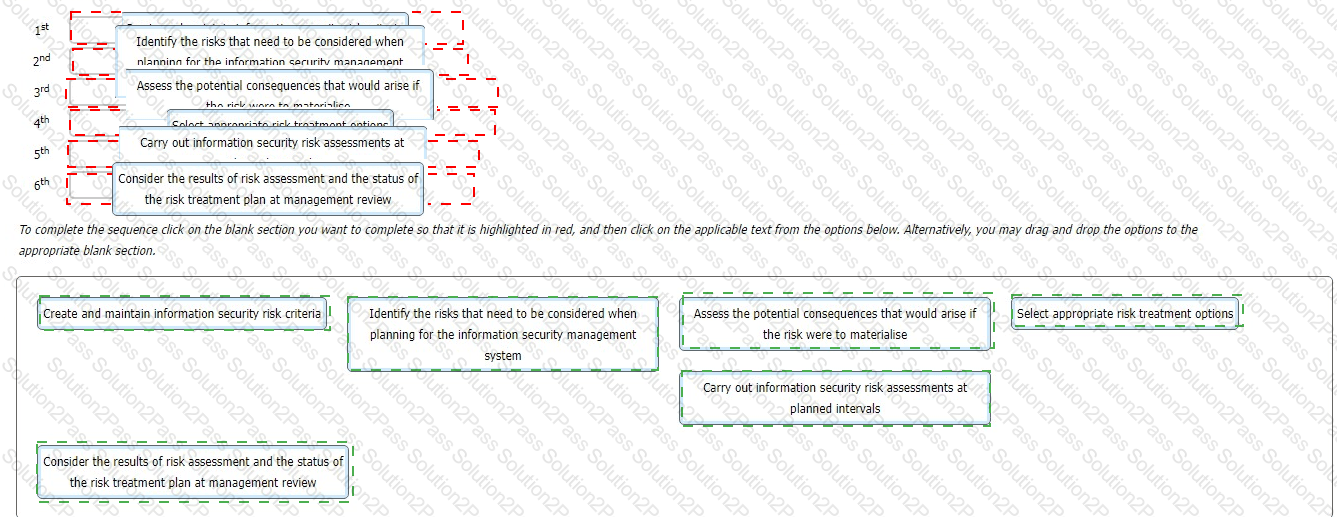
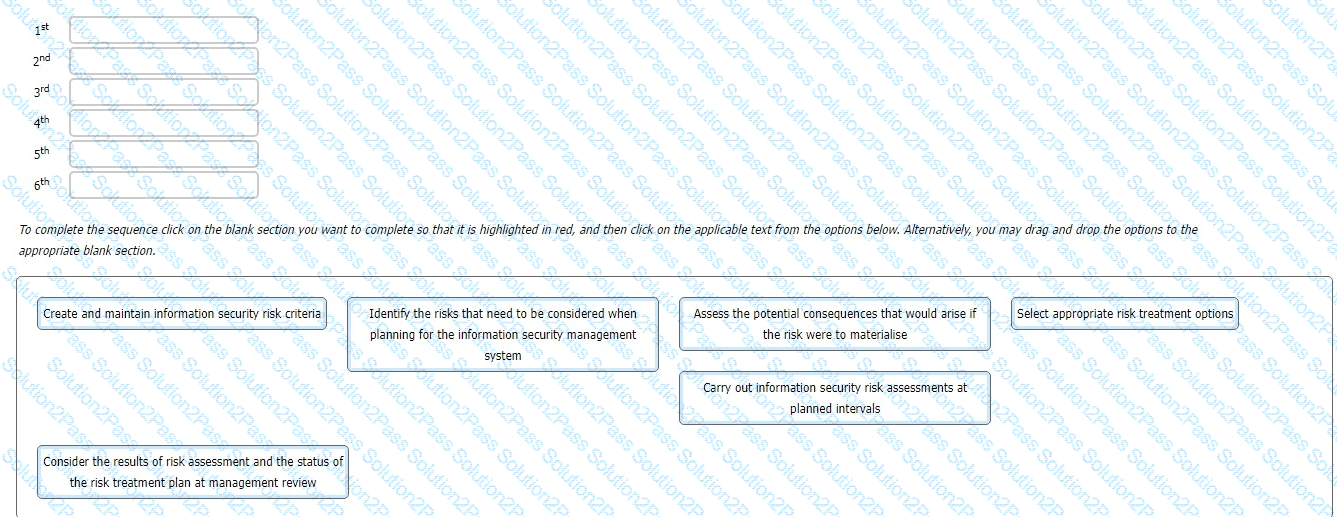
You are an experienced ISMS audit team leader providing instruction to a class of auditors in training. The subject of today's lesson is the management of information security risk in accordance with the requirements of ISO/IEC 27001:2022.
You provide the class with a series of activities. You then ask the class to sort these activities into the order in which they appear in the standard.
What is the correct sequence they should report back to you?
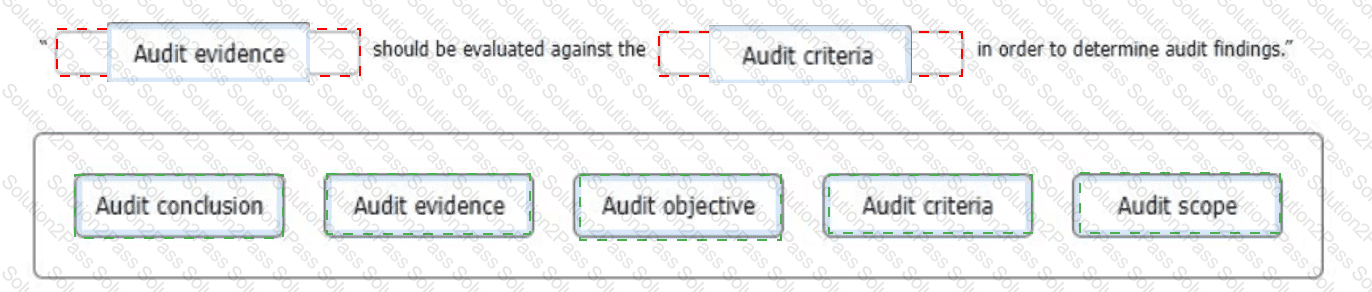
In regard to generating an audit finding, select the words that best complete the following sentence.
To complete the sentence with the best word(s), click on the blank section you want to complete so that it Is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.

Question:
Which situation presented below represents a threat?
Scenario 2: Knight is an electronics company from Northern California, US that develops video game consoles. Knight has more than 300 employees worldwide. On the
fifth anniversary of their establishment, they have decided to deliver the G-Console, a new generation video game console aimed for worldwide markets. G-Console is
considered to be the ultimate media machine of 2021 which will give the best gaming experience to players. The console pack will include a pair of VR headset, two
games, and other gifts.
Over the years, the company has developed a good reputation by showing integrity, honesty, and respect toward their customers. This good reputation is one of the
reasons why most passionate gamers aim to have Knight's G-console as soon as it is released in the market. Besides being a very customer-oriented company, Knight
also gained wide recognition within the gaming industry because of the developing quality. Their prices are a bit higher than the reasonable standards allow.
Nonetheless, that is not considered an issue for most loyal customers of Knight, as their quality is top-notch.
Being one of the top video game console developers in the world, Knight is also often the center of attention for malicious activities. The company has had an
operational ISMS for over a year. The ISMS scope includes all departments of Knight, except Finance and HR departments.
Recently, a number of Knight's files containing proprietary information were leaked by hackers. Knight's incident response team (IRT) immediately started to analyze
every part of the system and the details of the incident.
The IRT's first suspicion was that Knight's employees used weak passwords and consequently were easily cracked by hackers who gained unauthorized access to their
accounts. However, after carefully investigating the incident, the IRT determined that hackers accessed accounts by capturing the file transfer protocol (FTP) traffic.
FTP is a network protocol for transferring files between accounts. It uses clear text passwords for authentication.
Following the impact of this information security incident and with IRT's suggestion, Knight decided to replace the FTP with Secure Shell (SSH) protocol, so anyone
capturing the traffic can only see encrypted data.
Following these changes, Knight conducted a risk assessment to verify that the implementation of controls had minimized the risk of similar incidents. The results of
the process were approved by the ISMS project manager who claimed that the level of risk after the implementation of new controls was in accordance with the
company's risk acceptance levels.
Based on this scenario, answer the following question:
FTP uses clear text passwords for authentication. This is an FTP:
The audit lifecycle describes the ISO 19011 process for conducting an individual audit. Drag and drop the steps of the audit lifecycle into the correct sequence.

Which of the options below is a control related to the management of personnel that aims to avoid the occurrence of incidents?
Scenario 6
Sinvestment is an insurance provider that offers a wide range of coverage options, including home, commercial, and life insurance. Originally established in North California, the company has expanded its operations to other locations, including Europe and Africa. In addition to its growth, Sinvestment is committed to complying with laws and regulations applicable to its industry and preventing any information security incident. They have implemented an information security management system (ISMS) based on ISO/IEC 27001 and have applied for certification.
A team of auditors was assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment, they started the audit activities. For the activities of the stage 1 audit, it was decided that they would be performed on site, except the review of documented information, which took place remotely, as requested by Sinvestment.
The audit team started the stage 1 audit by reviewing the documentation required, including the declaration of the ISMS scope, information security policies, and internal audit reports. The evaluation of the documented information was based on the content and procedure for managing the documented information.
In addition, the auditors found out that the documentation related to information security training and awareness programs was incomplete and lacked essential details. When asked, Sinvestment’s top management stated that the company has provided information security training sessions to all employees.
The stage 2 audit was conducted three weeks after the stage 1 audit. The audit team observed that the marketing department (not included in the audit scope) had no procedures to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the company's information security policy, the issue was included in the audit report.
Question
Was Sinvestment’s request for reviewing documented information remotely acceptable?
Which two of the following statements are true?
The benefit of certifying an ISMS is to show the accreditation certificate on the website.
Scenario 3: NightCore is a multinational technology company based in the United States that focuses on e-commerce, cloud computing, digital streaming, and artificial intelligence. After having an information security management system (ISMS) implemented for over 8 months, they contracted a certification body to conduct a third party audit in order to get certified against ISO/IEC 27001.
The certification body set up a team of seven auditors. Jack, the most experienced auditor, was assigned as the audit team leader. Over the years, he received many well known certifications, such as the ISO/IEC 27001 Lead Auditor, CISA, CISSP, and CISM.
Jack conducted thorough analyses on each phase of the ISMS audit, by studying and evaluating every information security requirement and control that was implemented by NightCore. During stage 2 audit. Jack detected several nonconformities. After comparing the number of purchased invoices for software licenses with the software inventory, Jack found out that the company has been using the illegal versions of a software for many computers. He decided to ask for an explanation from the top management about this nonconformity and see whether they were aware about this. His next step was to audit NightCore's IT Department. The top management assigned Tom, NightCore's system administrator, to act as a guide and accompany Jack and the audit team toward the inner workings of their system and their digital assets infrastructure.
While interviewing a member of the Department of Finance, the auditors discovered that the company had recently made some unusual large transactions to one of their consultants. After gathering all the necessary details regarding the transactions. Jack decided to directly interview the top management.
When discussing about the first nonconformity, the top management told Jack that they willingly decided to use a copied software over the original one since it was cheaper. Jack explained to the top management of NightCore that using illegal versions of software is against the requirements of ISO/IEC 27001 and the national laws and regulations. However, they seemed to be fine with it.
Several months after the audit, Jack sold some of NightCore's information that he collected during the audit for a huge amount of money to competitors of NightCore.
Based on this scenario, answer the following question:
According to scenario 3, which audit principle has Jack compromised when he sold NightCore’s information after the audit?