ISO-IEC-27001-Lead-Auditor PECB Certified ISO/IEC 27001 2022 Lead Auditor exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your PECB ISO-IEC-27001-Lead-Auditor PECB Certified ISO/IEC 27001 2022 Lead Auditor exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Total 418 questions
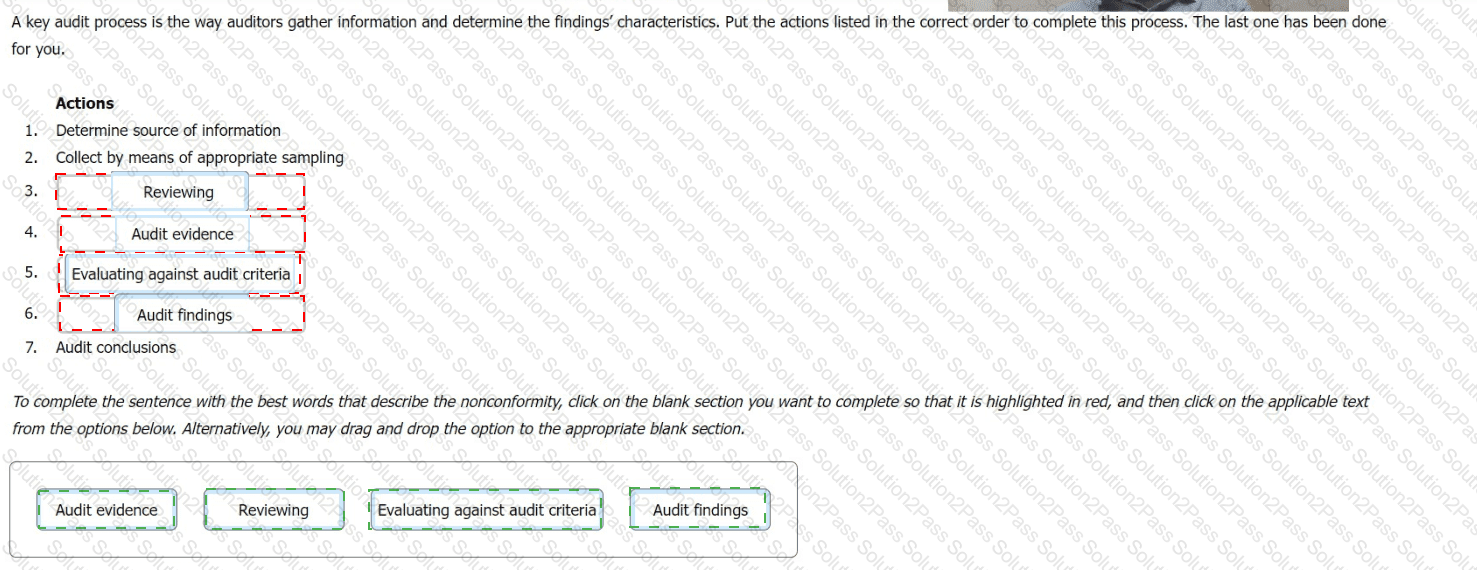
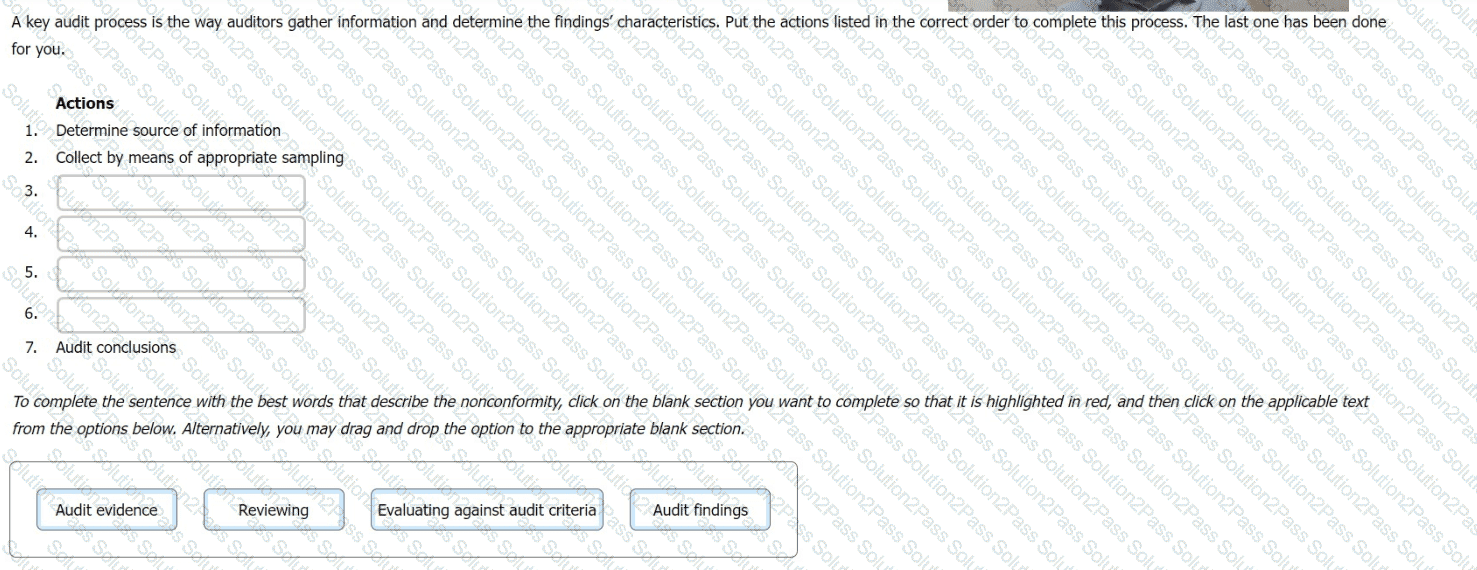
A key audit process is the way auditors gather information and determine the findings' characteristics. Put the actions listed in the correct order to complete this process. The last one has been done for you.
Scenario 1
Fintive is a distinguished security provider specializing in online payments and protection solutions. Founded in 1999 by Thomas Fin in San Jose, California, Fintive offers services to companies operating online that seek to improve their information security, prevent fraud, and protect user information such as personally identifiable information (PII).
Fintive bases its decision-making and operational processes on previous cases, gathering customer data, classifying them according to the case, and analyzing them.
Initially, Fintive required a large number of employees to be able to conduct such complex analyses. However, as technology advanced, the company recognized an opportunity to implement a modern tool — a chatbot — to achieve pattern analyses aimed at preventing fraud in real time. This tool would also assist in improving customer service.
The initial idea was communicated to the software development team, who supported the initiative and were assigned to work on the project. They began integrating the chatbot into the existing system and set an objective regarding the chatbot, which was to answer 85% of all chat queries.
After successfully integrating the chatbot, the company released it for customer use. However, the chatbot exhibited several issues. Due to insufficient testing and a lack of sample data provided during the training phase — when it was supposed to learn the query patterns — the chatbot failed to effectively address user queries. Additionally, it sent random files to users when it encountered invalid inputs, such as unusual patterns of dots and special characters.
Consequently, the chatbot could not effectively answer customer queries, overwhelming traditional customer support and preventing them from assisting customers with their requests.
Recognizing the potential risks, Fintive decided to implement a set of new controls. The measures included enabling comprehensive audit logging, configuring automated alert systems to flag unusual activities, performing periodic access reviews, and monitoring system behavior for anomalies. The objective was to identify unauthorized access, errors, or suspicious activities in a timely manner, ensuring that any potential issues could be quickly recognized and investigated before causing significant harm.
Question
Based on the scenario above, to ensure the protection of information privacy, Fintive decided to implement security controls. Is this acceptable?
Question:
When multiple offices of a certification body are involved, what must be ensured?
Why should materiality be considered during the initial contact?
CMM stands for?
Scenario 6
Sinvestment is an insurance provider that offers a wide range of coverage options, including home, commercial, and life insurance. Originally established in North California, the company has expanded its operations to other locations, including Europe and Africa. In addition to its growth, Sinvestment is committed to complying with laws and regulations applicable to its industry and preventing any information security incident. They have implemented an information security management system (ISMS) based on ISO/IEC 27001 and have applied for certification.
A team of auditors was assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment, they started the audit activities. For the activities of the stage 1 audit, it was decided that they would be performed on site, except the review of documented information, which took place remotely, as requested by Sinvestment.
The audit team started the stage 1 audit by reviewing the documentation required, including the declaration of the ISMS scope, information security policies, and internal audit reports. The evaluation of the documented information was based on the content and procedure for managing the documented information.
In addition, the auditors found out that the documentation related to information security training and awareness programs was incomplete and lacked essential details. When asked, Sinvestment’s top management stated that the company has provided information security training sessions to all employees.
The stage 2 audit was conducted three weeks after the stage 1 audit. The audit team observed that the marketing department (not included in the audit scope) had no procedures to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the company's information security policy, the issue was included in the audit report.
Question
Based on Scenario 6, when evaluating documented information, what action should the auditor have taken during the stage 1 audit?
Question:
Which of the following statements regarding threats and vulnerabilities in information security is NOT correct?
Which is not a requirement of HR prior to hiring?
Scenario 9: UpNet, a networking company, has been certified against ISO/IEC 27001. It provides network security, virtualization, cloud computing, network hardware, network management software, and networking technologies.
The company's recognition has increased drastically since gaining ISO/IEC 27001 certification. The certification confirmed the maturity of UpNefs operations and its compliance with a widely recognized and accepted standard.
But not everything ended after the certification. UpNet continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. The top management was not willing to employ a full-time team of internal auditors, so they decided to outsource the internal audit function. This form of internal audits ensured independence, objectivity, and that they had an advisory role about the continual improvement of the ISMS.
Not long after the initial certification audit, the company created a new department specialized in data and storage products. They offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. This caused changes to the operations of the other departments already covered in the ISMS certification scope.
Therefore. UpNet initiated a risk assessment process and an internal audit. Following the internal audit result, the company confirmed the effectiveness and efficiency of the existing and new processes and controls.
The top management decided to include the new department in the certification scope since it complies with ISO/IEC 27001 requirements. UpNet announced that it is ISO/IEC 27001 certified and the certification scope encompasses the whole company.
One year after the initial certification audit, the certification body conducted another audit of UpNefs ISMS. This audit aimed to determine the UpNefs ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS continues to fulfill
the requirements of the standard. Nonetheless, the new department caused a significant impact on governing the management system. Moreover, the certification body was not informed about any changes. Thus, the UpNefs certification was suspended.
Based on the scenario above, answer the following question:
Based on scenario 9, why was UpNefs certification suspended?
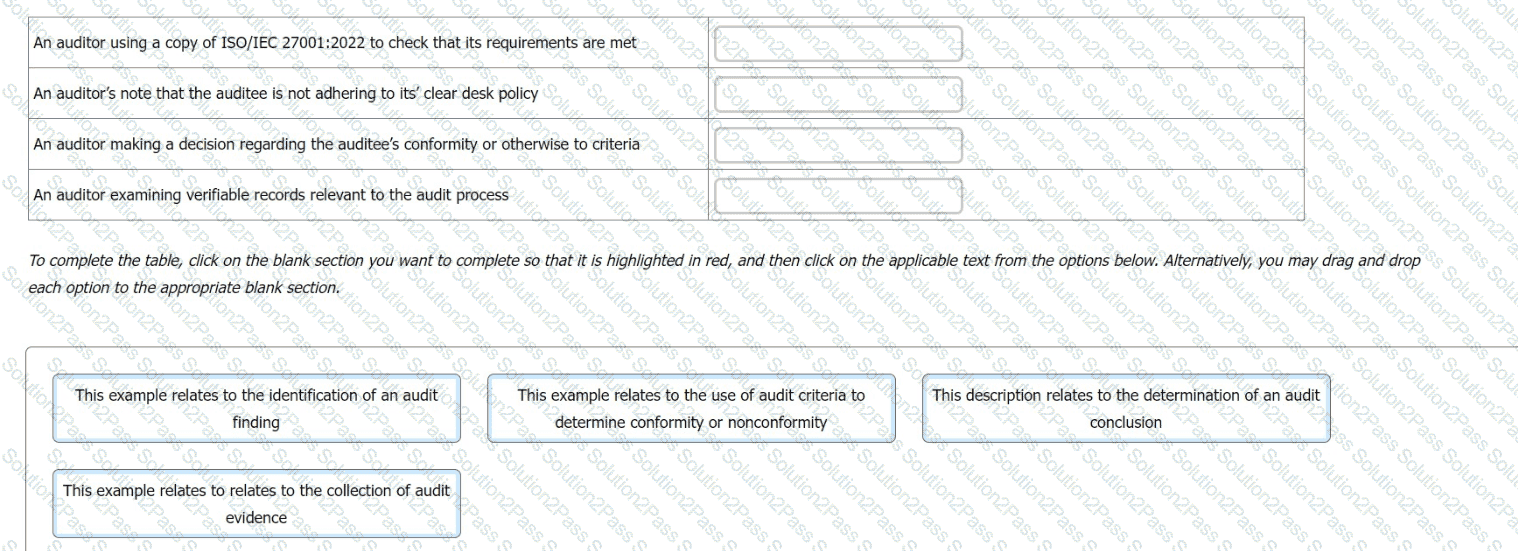
You are an experienced ISMS audit team leader, assisting an auditor in training to write their first audit report.
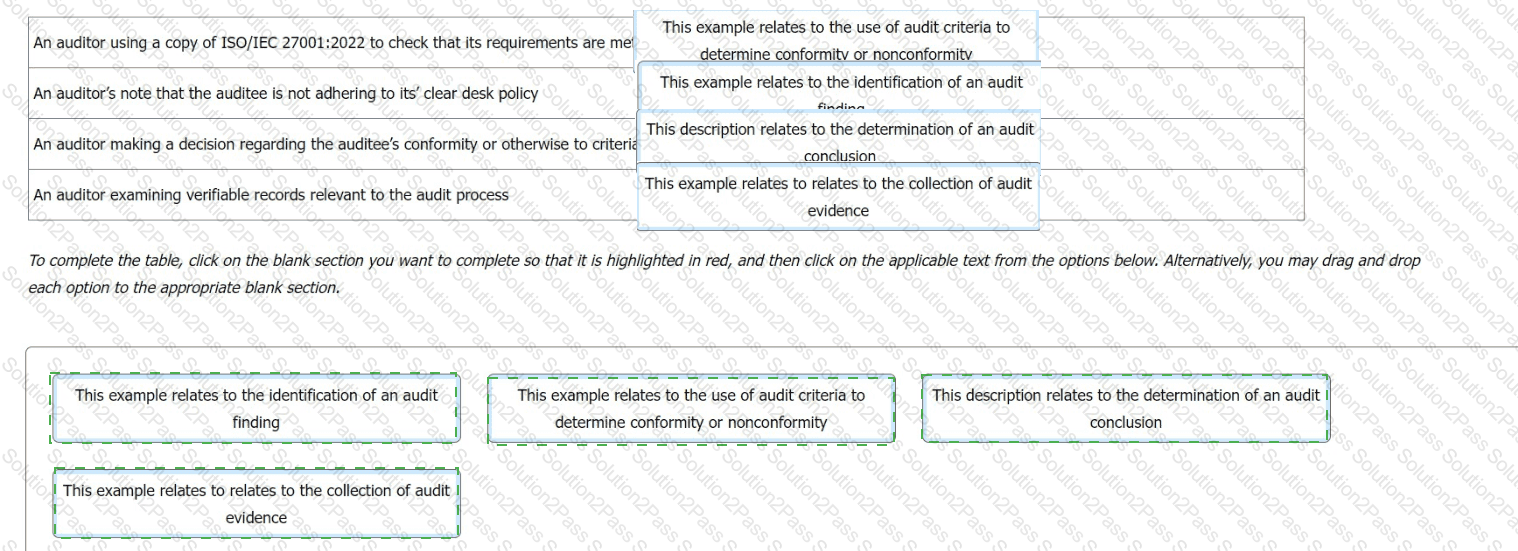
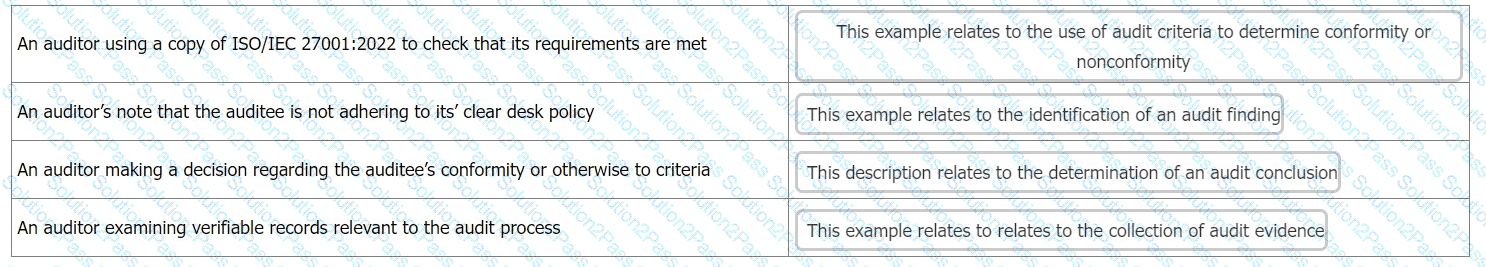
You want to check the auditor in training's understanding of terminology relating to the contents of an audit report and chose to do this by presenting the following examples.
For each example, you ask the auditor in training what the correct term is that describes the activity
Match the activity to the description.
Question:
Which of the following best defines managerial controls?
You are an experienced ISMS audit team leader conducting a third-party surveillance audit of an internet services provider. You are reviewing the organization's risk assessment processes for conformity with ISO/IEC 27001:2022.
Which three of the following audit findings would prompt you to raise a nonconformity report?
Scenario 4: Branding is a marketing company that works with some of the most famous companies in the US. To reduce internal costs. Branding has outsourced the software development and IT helpdesk operations to Techvology for over two years. Techvology. equipped with the necessary expertise, manages Branding's software, network, and hardware needs. Branding has implemented an information security management system (ISMS) and is certified against ISO/IEC 27001, demonstrating its commitment to maintaining high standards of information security. It actively conducts audits on Techvology to ensure that the security of its outsourced operations complies with ISO/IEC 27001 certification requirements.
During the last audit. Branding's audit team defined the processes to be audited and the audit schedule. They adopted an evidence based approach, particularly in light of two information security incidents reported by Techvology in the past year The focus was on evaluating how these incidents were addressed and ensuring compliance with the terms of the outsourcing agreement
The audit began with a comprehensive review of Techvology's methods for monitoring the quality of outsourced operations, assessing whether the services provided met Branding's expectations and agreed-upon standards The auditors also verified whether Techvology complied with the contractual requirements established between the two entities This involved thoroughly examining the terms and conditions in the outsourcing agreement to guarantee that all aspects, including information security measures, are being adhered to.
Furthermore, the audit included a critical evaluation of the governance processes Techvology uses to manage its outsourced operations and other organizations. This step is crucial for Branding to verify that proper controls and oversight mechanisms are in place to mitigate potential risks associated with the outsourcing arrangement.
The auditors conducted interviews with various levels of Techvology's personnel and analyzed the incident resolution records. In addition, Techvology provided the records that served as evidence that they conducted awareness sessions for the staff regarding incident management. Based on the information gathered, they predicted that both information security incidents were caused by incompetent personnel. Therefore, auditors requested to see the personnel files of the employees involved in the incidents to review evidence of their competence, such as relevant experience, certificates, and records of attended trainings.
Branding's auditors performed a critical evaluation of the validity of the evidence obtained and remained alert for evidence that could contradict or question the reliability of the documented information received. During the audit at Techvology, the auditors upheld this approach by critically assessing the incident resolution records and conducting thorough interviews with employees at different levels and functions. They did not merely take the word of Techvology's representatives for facts; instead, they sought concrete evidence to support the representatives' claims about the incident management processes.
Based on the scenario above, answer the following question:
Question:
According to Scenario 4, what type of audit evidence did the auditors collect to determine the source of the information security incidents?
Scenario 4: Branding is a marketing company that works with some of the most famous companies in the US. To reduce internal costs. Branding has outsourced the software development and IT helpdesk operations to Techvology for over two years. Techvology. equipped with the necessary expertise, manages Branding's software, network, and hardware needs. Branding has implemented an information security management system (ISMS) and is certified against ISO/IEC 27001, demonstrating its commitment to maintaining high standards of information security. It actively conducts audits on Techvology to ensure that the security of its outsourced operations complies with ISO/IEC 27001 certification requirements.
During the last audit. Branding's audit team defined the processes to be audited and the audit schedule. They adopted an evidence based approach, particularly in light of two information security incidents reported by Techvology in the past year The focus was on evaluating how these incidents were addressed and ensuring compliance with the terms of the outsourcing agreement
The audit began with a comprehensive review of Techvology's methods for monitoring the quality of outsourced operations, assessing whether the services provided met Branding's expectations and agreed-upon standards The auditors also verified whether Techvology complied with the contractual requirements established between the two entities This involved thoroughly examining the terms and conditions in the outsourcing agreement to guarantee that all aspects, including information security measures, are being adhered to.
Furthermore, the audit included a critical evaluation of the governance processes Techvology uses to manage its outsourced operations and other organizations. This step is crucial for Branding to verify that proper controls and oversight mechanisms are in place to mitigate potential risks associated with the outsourcing arrangement.
The auditors conducted interviews with various levels of Techvology's personnel and analyzed the incident resolution records. In addition, Techvology provided the records that served as evidence that they conducted awareness sessions for the staff regarding incident management. Based on the information gathered, they predicted that both information security incidents were caused by incompetent personnel. Therefore, auditors requested to see the personnel files of the employees involved in the incidents to review evidence of their competence, such as relevant experience, certificates, and records of attended trainings.
Branding's auditors performed a critical evaluation of the validity of the evidence obtained and remained alert for evidence that could contradict or question the reliability of the documented information received. During the audit at Techvology, the auditors upheld this approach by critically assessing the incident resolution records and conducting thorough interviews with employees at different levels and functions. They did not merely take the word of Techvology's representatives for facts; instead, they sought concrete evidence to support the representatives' claims about the incident management processes.
Based on the scenario above, answer the following question:
Question:
Based on Scenario 4, what type of audit did Branding conduct?
During a third-party certification audit, you are presented with a list of issues by an auditee. Which four of the following constitute 'internal' issues in the context of a management system to ISO 27001:2022?
Higher labour costs as a result of an aging population
You are performing an ISMS audit at a residential nursing home (ABC) that provides healthcare services. The next
step in your audit plan is to verify the information security of ABC's healthcare mobile app development, support,
and lifecycle process. During the audit, you learned the organization outsourced the mobile app development to a
professional software development company with CMMI Level 5, ITSM (ISO/IEC 20000-1), BCMS (ISO 22301) and
ISMS (ISO/IEC 27001) certified.
The IT Manager presented the software security management procedure and summarised the process as following:
The mobile app development shall adopt "security-by-design" and "security-by-default" principles, as a minimum.
The following security functions for personal data protection shall be available:
Access control.
Personal data encryption, i.e., Advanced Encryption Standard (AES) algorithm, key lengths: 256 bits; and
Personal data pseudonymization.
Vulnerability checked and no security backdoor
You sample the latest Mobile App Test report, details as follows:
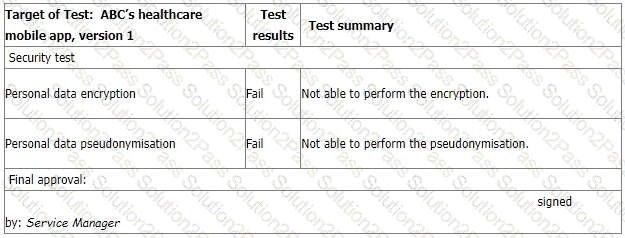
The IT Manager explains the test results should be approved by him according to the software security management procedure. The reason why the encryption and pseudonymisation functions failed is that these functions heavily slowed down the system and service performance. An extra 150% of resources are needed to cover this. The Service Manager agreed that access control is good enough and acceptable. That's why the Service Manager signed the approval.
You are preparing the audit findings. Select the correct option.
Scenario 4: SendPay is a financial company that provides its services through a network of agents and financial institutions. One of their main services is transferring money worldwide. SendPay, as a new company, seeks to offer top quality services to its clients. Since the company offers international transactions, it requires from their clients to provide personal information, such as their identity, the reason for the transactions, and other details that might be needed to complete the transaction. Therefore, SendPay has implemented security measures to protect their clients' information, including detecting, investigating, and responding to any information security threats that may emerge. Their commitment to offering secure services was also reflected during the ISMS implementation where the company invested a lot of time and resources.
Last year, SendPay unveiled their digital platform that allows money transactions through electronic devices, such as smartphones or laptops, without requiring an additional fee. Through this platform, SendPay's clients can send and receive money from anywhere and at any time. The digital platform helped SendPay to simplify the company's operations and further expand its business. At the time, SendPay was outsourcing its software operations, hence the project was completed by the software development team of the outsourced company. The same team was also responsible for maintaining the technology infrastructure of SendPay.
Recently, the company applied for ISO/IEC 27001 certification after having an ISMS in place for almost a year. They contracted a certification body that fit their criteria. Soon after, the certification body appointed a team of four auditors to audit SendPay's ISMS.
During the audit, among others, the following situations were observed:
1.The outsourced software company had terminated the contract with SendPay without prior notice. As a result, SendPay was unable to immediately bring the services back in-house and its operations were disrupted for five days. The auditors requested from SendPay's representatives to provide evidence that they have a plan to follow in cases of contract terminations. The representatives did not provide any documentary evidence but during an interview, they told the auditors that the top management of SendPay had identified two other software development companies that could provide services immediately if similar situations happen again.
2.There was no evidence available regarding the monitoring of the activities that were outsourced to the software development company. Once again, the representatives of SendPay told the auditors that they regularly communicate with the software development company and that they are appropriately informed for any possible change that might occur.
3.There was no nonconformity found during the firewall testing. The auditors tested the firewall configuration in order to determine the level of security provided by
these services. They used a packet analyzer to test the firewall policies which enabled them to check the packets sent or received in real-time.
Based on this scenario, answer the following question:
SendPay's representatives stated that the company did not have a plan to follow in case of a contract termination with the company that they outsource activities to. Instead, the top management had identified two other software development companies that could provide the same services. How do you describe this situation?
An auditor of organisation A performs an audit of supplier B. Which two of the following actions is likely to represent a breach of confidentiality by the auditor after having identified findings in B's information security management system?
Information or data that are classified as ______ do not require labeling.
A decent visitor is roaming around without visitor's ID. As an employee you should do the following, except:
Total 418 questions