PCCET Paloalto Networks Palo Alto Networks Certified Cybersecurity Entry-level Technician Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
Which key component is used to configure a static route?
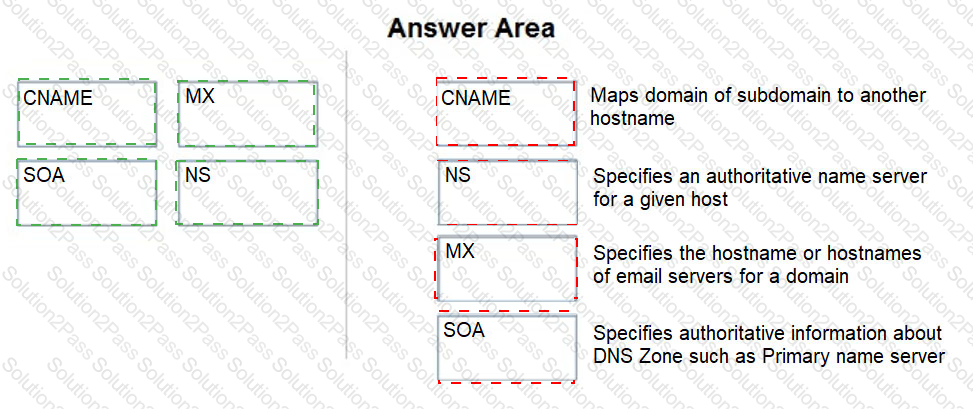
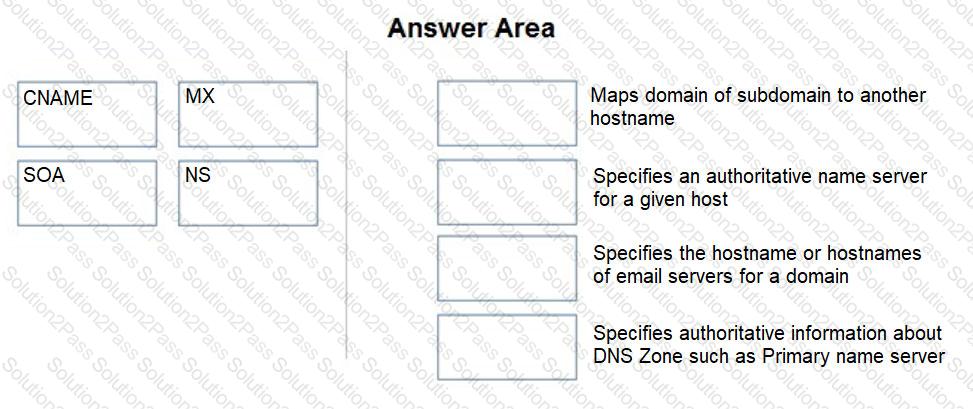
Match the DNS record type to its function within DNS.
What does SOAR technology use to automate and coordinate workflows?
If an endpoint does not know how to reach its destination, what path will it take to get there?
Which two pieces of information are considered personally identifiable information (PII)? (Choose two.)
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
Which of the following is a Routed Protocol?
Which feature of the VM-Series firewalls allows them to fully integrate into the DevOps workflows and CI/CD pipelines without slowing the pace of business?
How can local systems eliminate vulnerabilities?
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next- generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
What are three benefits of SD-WAN infrastructure? (Choose three.)
What is a characteristic of the National Institute Standards and Technology (NIST) defined cloud computing model?
Which of the following is a CI/CD platform?
Which of the following is an AWS serverless service?
Which not-for-profit organization maintains the common vulnerability exposure catalog that is available through their public website?
Which activities do local organization security policies cover for a SaaS application?
What is the ptrpose of automation in SOAR?
Which action must Secunty Operations take when dealing with a known attack?