PCCET Paloalto Networks Palo Alto Networks Certified Cybersecurity Entry-level Technician Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?
How does adopting a serverless model impact application development?
Which of the following is a service that allows you to control permissions assigned to users in order for them to access and utilize cloud resources?
What is the key to “taking down” a botnet?
Which option describes the “selective network security virtualization” phase of incrementally transforming data centers?
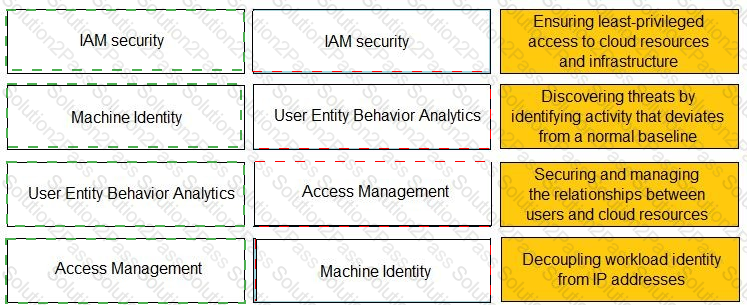
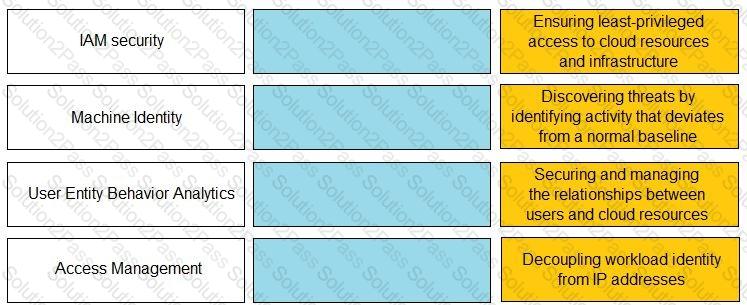
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Which VM-Series virtual firewall cloud deployment use case reduces your environment's attack surface?
A doctor receives an email about her upcoming holiday in France. When she clicks the URL website link in the email, the connection is blocked by her office firewall because it's a known malware website. Which type of attack includes a link to a malware website in an email?
Which method is used to exploit vulnerabilities, services, and applications?
Which two network resources does a directory service database contain? (Choose two.)
In which phase of the cyberattack lifecycle do attackers establish encrypted communication channels back to servers across the internet so that they can modify their attack objectives and methods?
A user is provided access over the internet to an application running on a cloud infrastructure. The servers, databases, and code of that application are hosted and maintained by the vendor.
Which NIST cloud service model is this?
What are the two most prominent characteristics of the malware type rootkit? (Choose two.)
Which network firewall operates up to Layer 4 (Transport layer) of the OSI model and maintains information about the communication sessions which have been established between hosts on trusted and untrusted networks?
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
Which technique uses file sharing or an instant messenger client such as Meebo running over Hypertext Transfer Protocol (HTTP)?
Which characteristic of serverless computing enables developers to quickly deploy application code?
On which security principle does virtualization have positive effects?
Which three services are part of Prisma SaaS? (Choose three.)
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost and is infinitely scalable?