PSE-Cortex-Pro-24 Paloalto Networks Palo Alto Networks Systems Engineer Professional - Cortex Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks PSE-Cortex-Pro-24 Palo Alto Networks Systems Engineer Professional - Cortex certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Total 168 questions
Which four types of Traps logs are stored within Cortex Data Lake?
A Cortex XSOAR customer wants to ingest emails from a single mailbox. The mailbox brings in reported phishing emails and email requests from human resources (HR) to onboard new users. The customer wants to run two separate workflows from this mailbox, one for phishing and one for onboarding.
What will allow Cortex XSOAR to accomplish this in the most efficient way?
What are the key capabilities of the ASM for Remote Workers module?
What is the requirement for enablement of endpoint and network analytics in Cortex XDR?
When initiated, which Cortex XDR capability allows immediate termination of the process-or entire process tree-on an anomalous process discovered during investigation of a security event?
What should be configured for a Cortex XSIAM customer who wants to automate the response to certain alerts?
Which CLI query would bring back Notable Events from Splunk?
A)
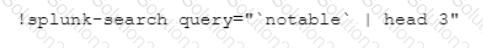
B)
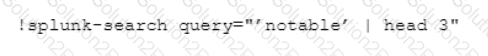
C)
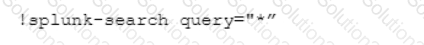
D)
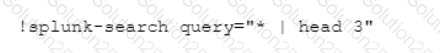
What allows the use of predetermined Palo Alto Networks roles to assign access rights to Cortex XDR users?
Which two types of lOCs are available for creation in Cortex XDR? (Choose two.)
An adversary is attempting to communicate with malware running on your network for the purpose of controlling malware activities or for ex filtrating data from your network. Which Cortex XDR Analytics alert is this activity most likely to trigger'?
Which two entities can be created as a behavioral indicator of compromise (BIOC)? (Choose two.)
When integrating with Splunk, what will allow you to push alerts into Cortex XSOAR via the REST API?
Which process in the causality chain does the Cortex XDR agent identify as triggering an event sequence?
If an anomalous process is discovered while investigating the cause of a security event, you can take immediate action to terminate the process or the whole process tree, and block processes from running by initiating which Cortex XDR capability?
Which task setting allows context output to a specific key?
Which product enables the discovery, exchange, and contribution of security automation playbooks, built into Cortex XSOAR?
Why is it important to document notes from the Proof of Value (POV) for post-sales hand off?
Which two filter operators are available in Cortex XDR? (Choose two.)
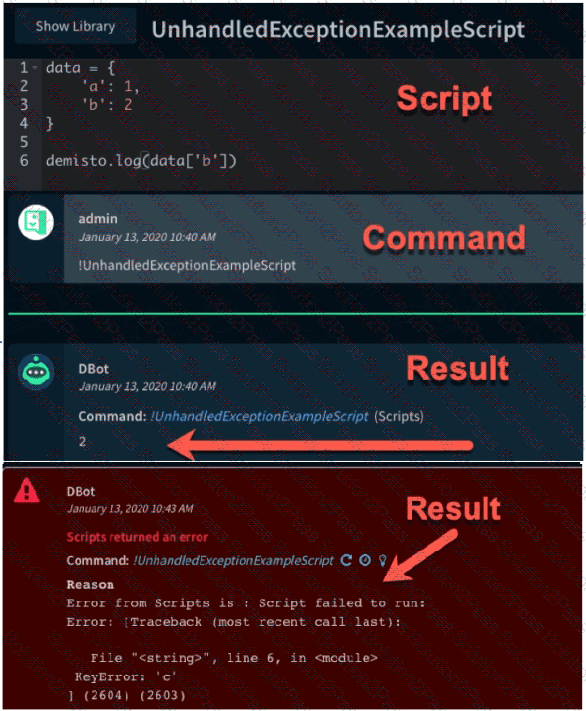
The images show two versions of the same automation script and the results they produce when executed in Demisto. What are two possible causes of the exception thrown in the second Image? (Choose two.)
SUCCESS
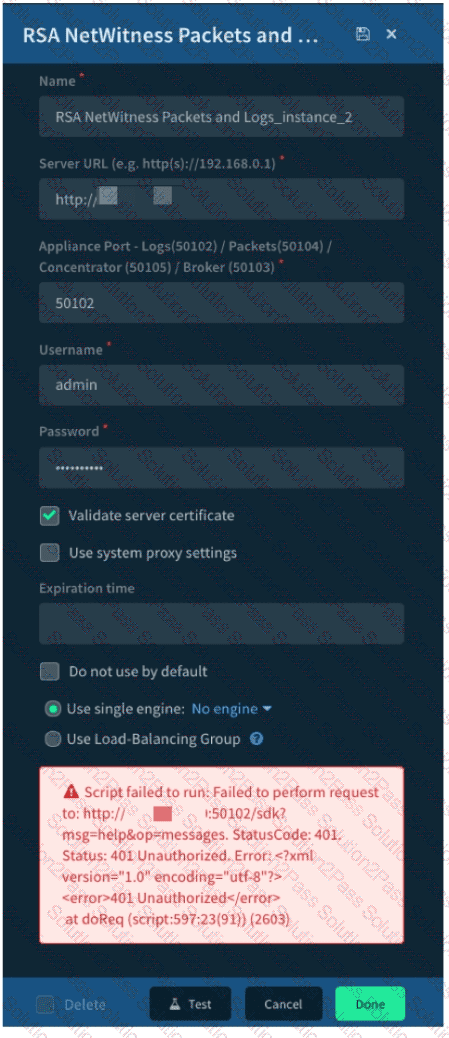
Given the integration configuration and error in the screenshot what is the cause of the problem?
Total 168 questions
