PSE-PrismaCloud Paloalto Networks PSE Palo Alto Networks System Engineer Professional - Prisma Cloud Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks PSE-PrismaCloud PSE Palo Alto Networks System Engineer Professional - Prisma Cloud certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An administrator deploys a VM-Series firewall into Amazon Web Services. Which attribute must be disabled on the data-plane elastic network interface for the instance to handle traffic that is not destined to its own IP address?
Which two items are required when a VM-100 BYOL instance is upgraded to a VM-300 BYOL instance? (Choose two.)
When protecting against attempts to exploit client-side and server-side vulnerabilities, what is the Palo Alto Networks best practice when using NGFW Vulnerability Protection Profiles?
What occurs with the command twistcli when scanning images?
A client has a sensitive internet-facing application server in Microsoft Azure and is concerned about resource exhaustion because of distributed denial-of-service attacks What can be configured on the VM-Series firewall to specifically protect this server against this type of attack?
Which two resources provide operational insight within the Prisma Cloud Asset Inventory? (Choose two.)
Which two templates are supported by Cloud Code Security scan service? (Choose two.)
Which two template formats are supported by the Prisma Cloud infrastructure as code (laC) scan service? (Choose two.)
Which framework in Prisma Public Cloud can be used to provide general best practices when no specific legal requirements or regulatory standards need to be met?
What are the two options to dynamically register tags used by Dynamic Address Groups that are referenced in policy? (Choose two.)
Which RQL string returns a list of all Azure virtual machines that are not currently running?
What does Prisma Cloud execute to change public cloud infrastructure when autoremediation is enabled?
Which RQL string searches for all EBS volumes that do not have a "DataClassification" tag?
Which Resource Query Language (RQL) query monitors all "delete" activities for the user "user1"?
What are two examples of Amazon Web Services logging services? (Choose two.)
Which Google Cloud Platform project shares its VPC networks with other projects?
What are two valid image identifiers to designate trust? (Choose two.)
What are two business values of Cloud Code Security? (Choose two.)
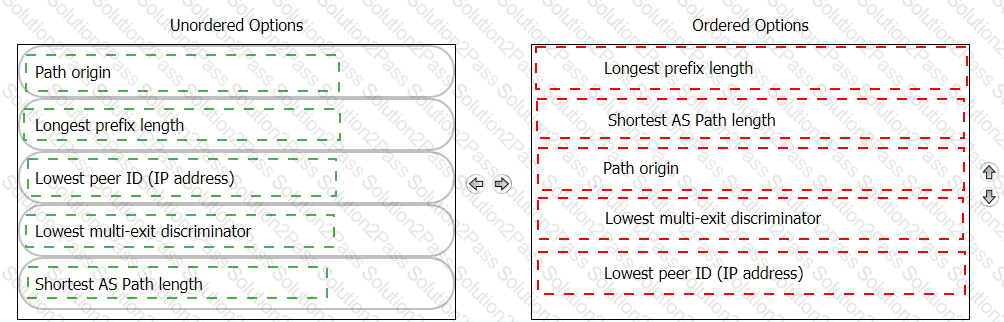
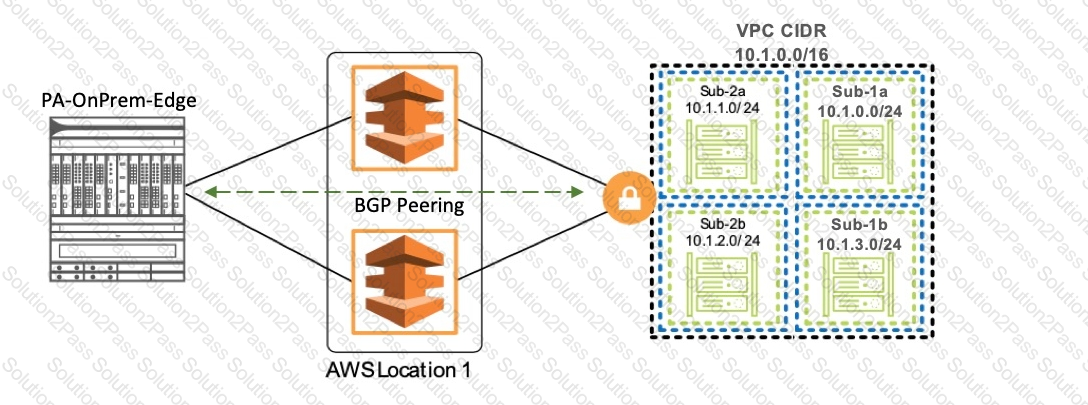
Based on the diagram, prioritize the order in which the Virtual Gateway evaluates the best route based on the deterministic B6P Path selection process.
What subcommand invokes the Prisma Cloud Compute (PCC) edition image scanner?