Practitioner Paloalto Networks Palo Alto Networks Cybersecurity Practitioner (PCCP) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks Practitioner Palo Alto Networks Cybersecurity Practitioner (PCCP) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Total 227 questions
Which two services does a managed detection and response (MDR) solution provide? (Choose two.)
Which activities do local organization security policies cover for a SaaS application?
Which technology secures software-as-a-service (SaaS) applications and network data, and also enforces compliance policies for application access?
What is a function of SSL/TLS decryption?
What does “forensics” refer to in a Security Operations process?
Which methodology does Identity Threat Detection and Response (ITDR) use?
With regard to cloud-native security in layers, what is the correct order of the four C's from the top (surface) layer to the bottom (base) layer?
Which scenario highlights how a malicious Portable Executable (PE) file is leveraged as an attack?
Which Palo Alto Networks solution has replaced legacy IPS solutions?
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
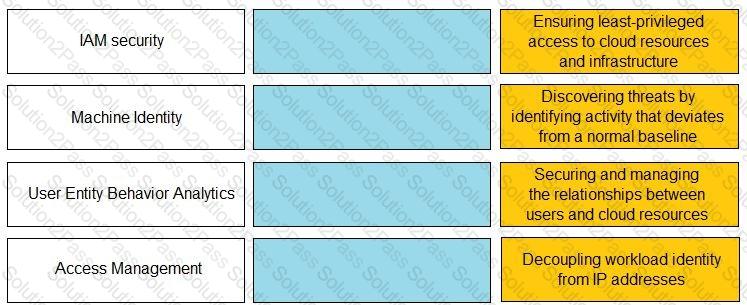
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Which three services are part of Prisma SaaS? (Choose three.)
What is an operation of an Attack Surface Management (ASM) platform?
What does SOAR technology use to automate and coordinate workflows?
Which of the Cloud-Delivered Security Services (CDSS) will detect zero-day malware by using inline cloud machine learning (ML) and sandboxing?
Which activity is a technique in the MITRE ATT&CK framework?
Which element of the security operations process is concerned with using external functions to help achieve goals?
What are two characteristics of an advanced persistent threat (APT)? (Choose two.)
What would allow a security team to inspect TLS encapsulated traffic?
What are two capabilities of identity threat detection and response (ITDR)? (Choose two.)
Total 227 questions

