Practitioner Paloalto Networks Palo Alto Networks Cybersecurity Practitioner (PCCP) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks Practitioner Palo Alto Networks Cybersecurity Practitioner (PCCP) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What protocol requires all routers in the same domain to maintain a map of the network?
Which Palo Alto Networks tool is used to prevent endpoint systems from running malware executables such as viruses, trojans, and rootkits?
Which option is an example of a North-South traffic flow?
On an endpoint, which method is used to protect proprietary data stored on a laptop that has been stolen?
Which two workflows are improved by integrating SIEMs with other security solutions? (Choose two.)
What are two disadvantages of Static Rout ng? (Choose two.)
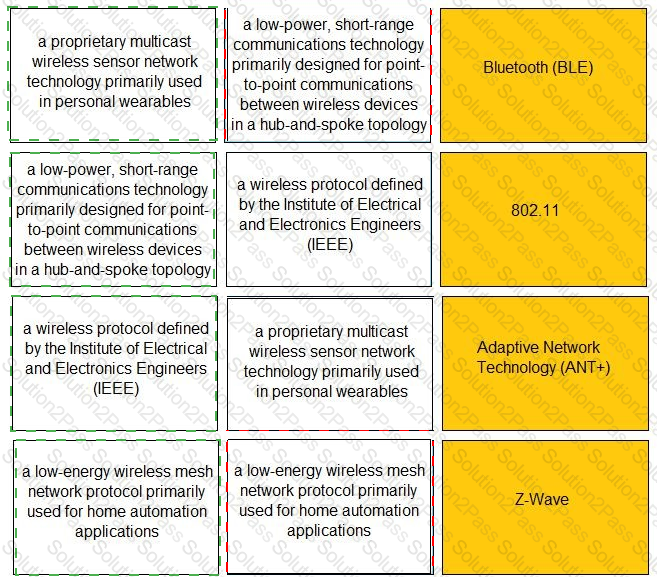
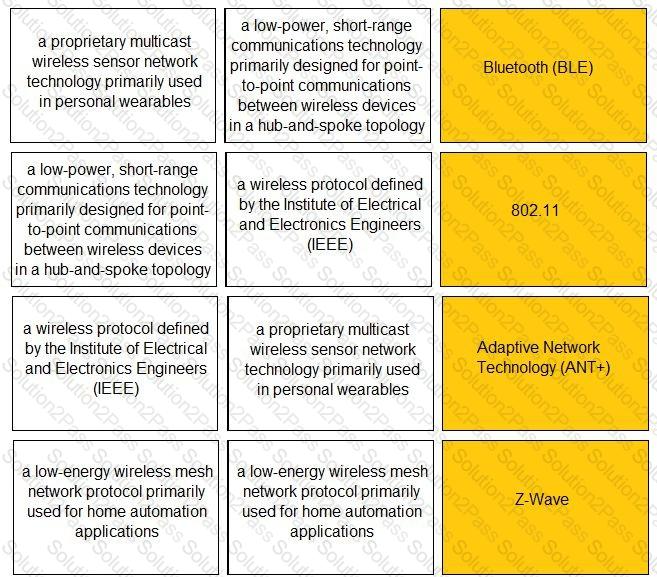
Match the IoT connectivity description with the technology.
Which attacker profile uses the internet to recruit members to an ideology, to train them, and to spread fear and include panic?