Practitioner Paloalto Networks Palo Alto Networks Cybersecurity Practitioner (PCCP) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks Practitioner Palo Alto Networks Cybersecurity Practitioner (PCCP) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is the function of an endpoint detection and response (EDR) tool?
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
Which aspect of a SaaS application requires compliance with local organizational security policies?
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
Which type of attack obscures its presence while attempting to spread to multiple hosts in a network?
What is used to orchestrate, coordinate, and control clusters of containers?
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?
What is a key advantage and key risk in using a public cloud environment?
What are two limitations of signature-based anti-malware software? (Choose two.)
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
Which VM-Series virtual firewall cloud deployment use case reduces your environment's attack surface?
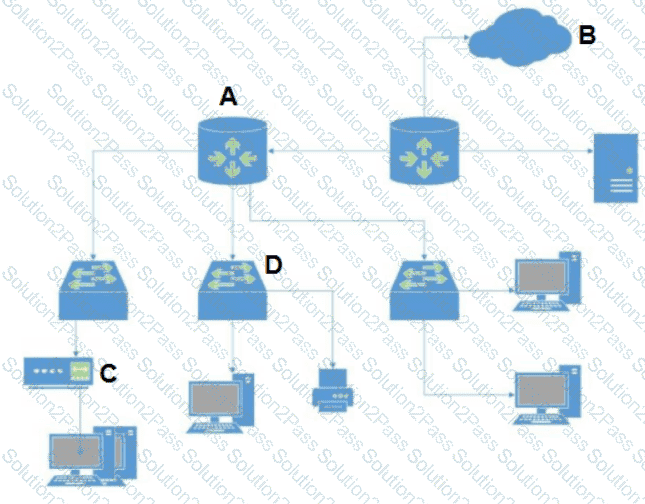
In the network diagram below, which device is the router?
A user is provided access over the internet to an application running on a cloud infrastructure. The servers, databases, and code of that application are hosted and maintained by the vendor.
Which NIST cloud service model is this?
How can local systems eliminate vulnerabilities?
Which two descriptions apply to an XDR solution? (Choose two.)
In addition to integrating the network and endpoint components, what other component does Cortex integrate to speed up IoC investigations?
Which service is encompassed by serverless architecture?
Which component of cloud security uses automated testing with static application security testing (SAST) to identify potential threats?
