WCNA Protocol Analysis Wireshark Certified Network Analyst Practice Exam Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Protocol Analysis WCNA Wireshark Certified Network Analyst Practice Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which transport is used for multicast and broadcast traffic?
The capture and displayfilter syntax for TCP communications is tcp.
Promiscuous mode and monitor mode offer the same functionality.
You can identify compromised hosts that are communicating with Command and Control (C&C) servers by capturing traffic close to the network egress point and filtering on the IP addresses of the suspect C&C servers.
With a few exceptions, display filters use the same syntax as capture filters.
Which protocol is used to locate the hardware address of a local target or local router?
Both the capture and display filter syntax for ARP requests and replies is arp.
Port resolution can use the TCP/IP stack services file to determine the correct destination port to use in the TCP or UDP header.
Wireshark's Export feature can be used to identify HTTP objects and reassemble them into their original format.
Which statement about packet timestamps is correct?
Applications may override the default port value defined in the TCP/IP stack services file.
Which protocol acts as the routable network layer protocol used to get packets from end-to-end on a TCP/IP network?
RTP provides transport functions for real-time data such as audio, video or simul-ation data overmulticast or unicast network services.
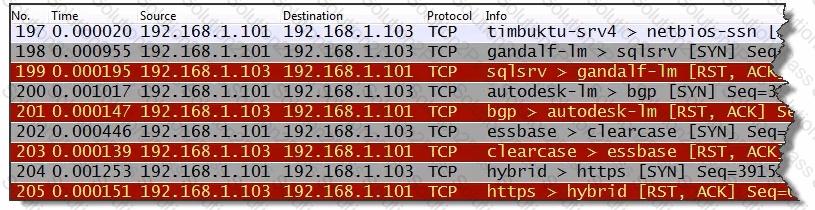
Which statement about this traffic is correct?
The capture filterport 67 would capture all DHCP traffic seen by Wireshark.
Network analysis is oftenconsidered 'electronic surveillance' or 'wiretapping* and may be illegal.
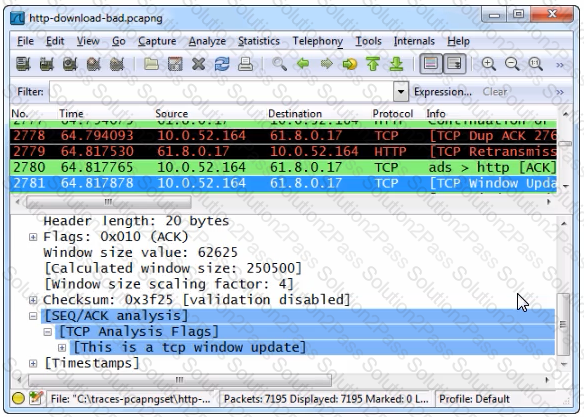
This image shows frame 2781which is a Window Update packet. This packet indicates that 10.0.52.164's TCP Window Size field value has increased since the last packet sent by that host.
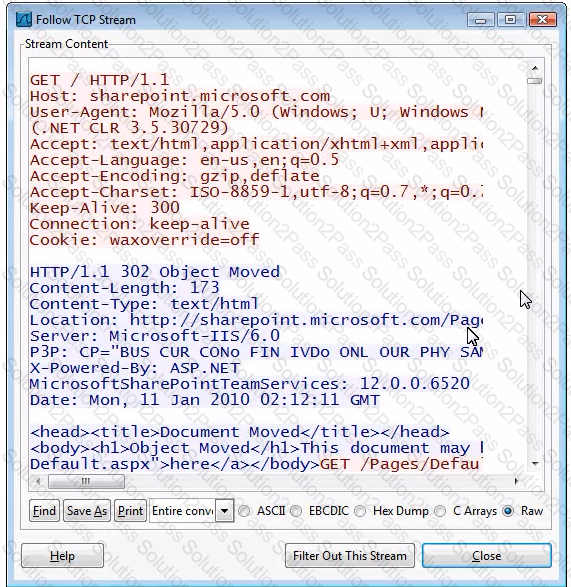
Which statement about this TCPstream is correct?
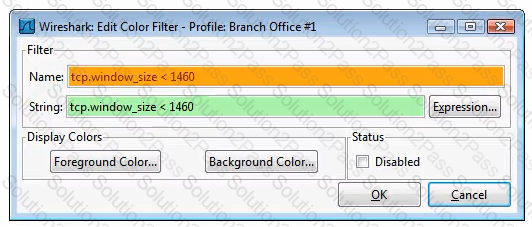
Which statement aboutthis color rule is correct?
Null scans use legal TCP packet formats, but listen for illegally-formed TCP response packets.
