S10-210 SNIA Storage Networking Management and Administration Free Practice Exam Questions (2025 Updated)
Prepare effectively for your SNIA S10-210 Storage Networking Management and Administration certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A customer has upgraded all switches in their redundant fabrics during a single maintenance window. Shortly after the upgrades are completed on the core switches, all servers lose access to all SAN attached storage.
What would have prevented this scenario?
You are using asynchronous storage replication to protect your critical database server. There are no replication agents installed on the database server. After a disaster, you are unable to bring up the database at the DR site.
What is the cause?
You are asked to set up a server to boot from a SAN.
Which setting on the HBA needs to be configured?
The CIO would like to segregate management device IP network traffic from server IP network traffic within the data center to limit potential security threats.
What would be used to accomplish this?
Click the Exhibit button.
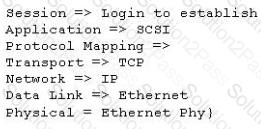
What is the protocol stack shown in the exhibit?
You are designing a security solution for a storage array which stores customer credit card information. Data on the storage array must be encrypted and if necessary, you want to be able to revoke access to data on demand.
In addition to encryption, which solution would allow you to do this in a secure and automated fashion?
Click the Exhibit button.
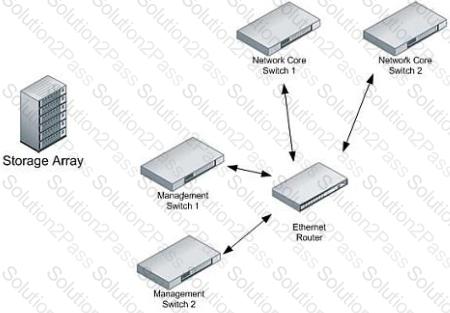
Your company has purchased a new storage array that has dual management access network ports. You need to connect the array and provide maximum redundancy without affecting production traffic.
Referring to the exhibit, where should the ports be attached?
Click the Exhibit button.
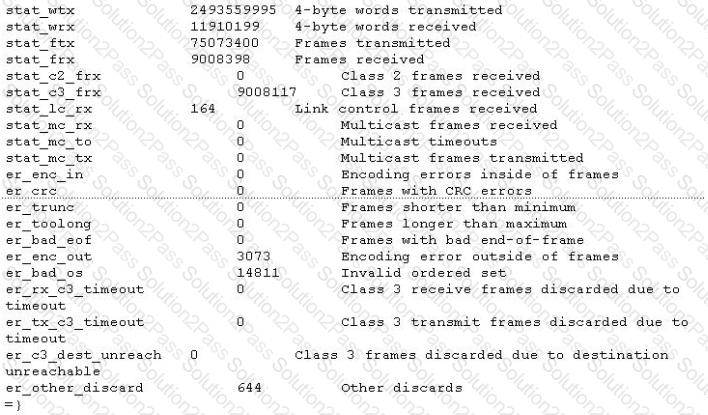
Referring to the exhibit, which three switch indicators will help you to determine the stability of a link? (Choose three.)
A number of servers are experiencing slower than expected performance. Analyzing the server, switch, and storage logs do not indicate any issues. You have been asked by the customer to address this issue.
What will improve performance?
You have a server which is booting from a SAN. After adding new SAN storage to a host, the host will not boot from the SAN.
What will resolve this problem?
You have completed installing your FC SAN. When everything is powered on, numerous devices are not available. You need to verify that the devices appear within the FC fabric by accessing the appropriate FC service that provides a list of devices and their respective function.
Which server within the Fibre Channel fabric would be used to do this?
Your company's Service Level Agreement (SLA) requires that no more then one hour's worth of data be lost in case of a system crash. The data must also be restored within 10 hours.
Which two RTO/RPO combinations meet the SLA? (Choose two.)
After the storage administrator merged two multi-vendor FC SANs, an error indicates that two ports have become isolated causing a segmentation to exist in the fabric.
Which two events would cause this? (Choose two.)
When troubleshooting an issue on a host, you discover that the existing file system partition has been corrupted after you provisioned a LUN to another host connected to the same FC fabric.
What is the cause of this problem?
A security audit reveals deficiencies in your company's FC zoning practices. Your manager asks you to make a recommendation to implement the most secure FC zoning possible. Your company is using switches from a single vendor.
What do you recommend?
A storage subsystems Web browser management interface reports that the subsystem has become degraded and remotely opens a service request with the vendor. Your vendors level three storage support engineer wants to remotely access your storage subsystem for troubleshooting.
What is a SNIA Storage Security Best Current Practices solution?
You need to add an iSCSI host and storage array to your environment. Your manager wants at least two options that allow all iSCSI initiators to query a central management server to locate the address of all iSCSI resources (e.g., iSCSI initiators, targets, switches, and management stations).
Which two protocol methods would be used? (Choose two.)
You have been hired to consult with storage administrators that are working with zoning and naming convention consistency issues. There are numerous types of zoning methods available using standards that also include aliasing. You want to use a method that guarantees unique global port identification.
What accomplishes this goal?
The latest storage utilization report shows that 80% of the current 500 TB of enterprise storage is allocated. The storage administrator must specify the amount of additional storage needed for local copies for approximately half of the active storage.
How much additional storage should the administrator request?
You are installing an OLTP application on a new server. The I/O profile of the application consists of 100% random read operations of 8 kilobyte transfers. You need to determine which HBA to use in your application to accommodate 50,000 IOPS.
What is the minimum FC link speed that will satisfy the application's requirements?
