SPLK-1003 Splunk Enterprise Certified Admin Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Splunk SPLK-1003 Splunk Enterprise Certified Admin certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which layers are involved in Splunk configuration file layering? (select all that apply)
When would the following command be used?
Which setting allows the configuration of Splunk to allow events to span over more than one line?
Which of the following are methods for adding inputs in Splunk? (select all that apply)
What is the correct order of index time precedence?
(For each of the following, highest precedence is shown at the top and lowest precedence is shown at the bottom)
Which of the following is accurate regarding the input phase?
Which forwarder is recommended by Splunk to use in a production environment?
What is the importance of modifying Transparent Huge Pages (THP) and ulimit settings when installing Splunk Enterprise?
Which of the following types of data count against the license daily quota?
What happens when there are conflicting settings within two or more configuration files?
A Splunk administrator has been tasked with developing a retention strategy to have frequently accessed data sets on SSD storage and to have older, less frequently accessed data on slower NAS storage. They have set a mount point for the NAS. Which parameter do they need to modify to set the path for the older, less frequently accessed data in indexes.conf?
Where are license files stored?
Which of the following is a benefit of distributed search?
Which of the following accurately describes HTTP Event Collector indexer acknowledgement?
What is the default character encoding used by Splunk during the input phase?
In a customer managed Splunk Enterprise environment, what is the endpoint URI used to collect data?
There is a file with a vast amount of old data. Which of the following inputs.conf attributes would allow an admin to monitor the file for updates without indexing the pre-existing data?
Which of the following statements describes how distributed search works?
Which is a valid stanza for a network input?
Which of the following is valid distribute search group?
A)
B)
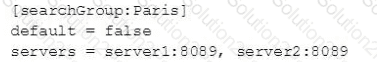
C)
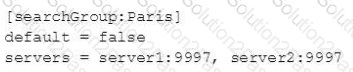
D)
