250-428 Symantec Administration of Symantec Endpoint Protection 14 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Symantec 250-428 Administration of Symantec Endpoint Protection 14 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two Symantec Endpoint Protection components are used to distribute content updates? (Select two.)
Which Symantec Endpoint Protection technology blocks a downloaded program from installing browser plugins?
What is the difference between a shared and non-shared policy?
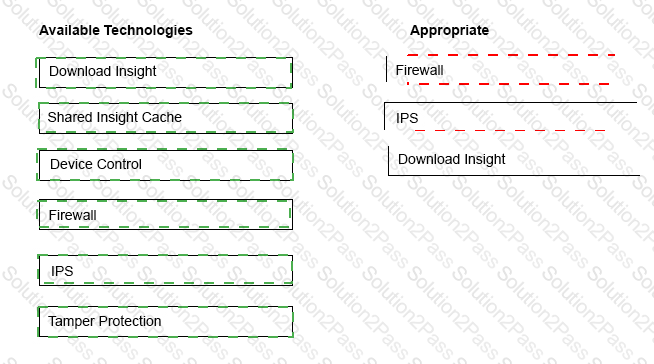
An administrator is unknowingly trying to connect to a malicious website and download a known threat within a .rar file. All Symantec Endpoint Protection technologies are installed on the client’s system.
Drag and drop the technologies to the right side of the screen in the sequence necessary to block or detect the malicious file.
An administrator is unable to delete a location.
What is the likely cause?
In which two areas can host groups be used? (Select two.)
An organization recently experienced an outbreak and is conducting a health check of their environment! What Protection Technology should the SEP team enable to prevent vulnerability attacks on software?
Which setting can an administrator configure in the LiveUpdate policy?
Which object in the Symantec Endpoint Protection Manager console describes the most granular level to which a policy can be assigned?
Which ports on the company firewall must an administrator open to avoid problems when connecting to Symantec Public LiveUpdate servers?
Refer to the exhibit.
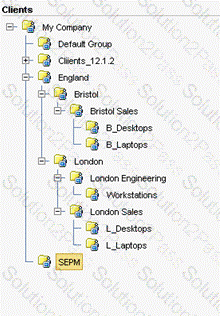
A manufacturing company runs three shifts at their Bristol Sales office. These employees currently share desktops in the B_Desktops group. The administrators need to apply different policies/configurations for each shift.
Which step should the administrator take in order to implement shift policies after switching the clients to user mode?
An administrator plans to implement a multi-site Symantec Endpoint Protection (SEP) deployment. The administrator needs to determine whether replication is viable without having to make network firewall changes or change defaults in SEP.
Which port should the administrator verify is open on the path of communication between the two proposed sites? (Type the port number.)
A large-scale virus attack is occurring and a notification condition is configured to send an email whenever viruses infect five computers on the network. A Symantec Endpoint Protection administrator has set a one hour damper period for that notification condition.
How many notifications does the administrator receive after 30 computers are infected in two hours?
An administrator needs to configure Secure Socket Layer (SSL) communication for clients. In the httpd.conf file, located on the Symantec Endpoint Protection Manager (SEPM), the administrator removes the hashmark (#) from the text string displayed below.
#Include conf/ssl/sslForcClients.conf<</p>
Which two tasks must the administrator perform to complete the SSL configuration? (Select two.)
In addition to performance improvements, which two benefits does Insight provide? (Select two.)
A company has 10,000 Symantec Endpoint Protection (SEP) clients deployed using two Symantec Endpoint Protection Managers (SEPMs).
Which configuration is recommended to ensure that each SEPM is able to effectively handle the communications load with the SEP clients?
A company has a small number of systems in their Symantec Endpoint Protection Manager (SEPM) group with federal mandates that AntiVirus definitions undergo a two week testing period. After being loaded on the client, the tested virus definitions must remain unchanged on the client systems until the next set of virus definitions have completed testing. All other clients must remain operational on the most recent definition sets. An internal LiveUpdate Server has been considered as too expensive to be a solution for this company.
What should be modified on the SEPM to meet this mandate?
Which task is unavailable for administrative accounts that authenticate using RSA SecurID Authentication?
A system running Symantec Endpoint Protection is assigned to a group with client user interface control settings set to mixed mode with Auto-Protect options set to Client. The user on the system is unable to turn off Auto-Protect.
What is the likely cause of this problem?
What report should a SEP administrator utilize to verify that Clients are connected to the management server?