250-438 Symantec Administration of Symantec Data Loss Prevention 15 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Symantec 250-438 Administration of Symantec Data Loss Prevention 15 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which tool must a DLP administrator run to certify the database prior to upgrading DLP?
A software company wants to protect its source code, including new source code created between scheduled indexing runs.
Which detection method should the company use to meet this requirement?
A DLP administrator created a new agent configuration for an Endpoint server. However, the endpoint agents fail to receive the new configuration.
What is one possible reason that the agent fails to receive the new configuration?
What is the correct order for data in motion when a customer has integrated their CloudSOC and DLP solutions?
Which statement accurately describes where Optical Character Recognition (OCR) components must be installed?
A customer needs to integrate information from DLP incidents into external Governance, Risk and Compliance dashboards.
Which feature should a third party component integrate with to provide dynamic reporting, create custom incident remediation processes, or support business processes?
What is the Symantec recommended order for stopping Symantec DLP services on a Windows Enforce server?
What detection technology supports partial contents matching?
A compliance officer needs to understand how the company is complying with its data security policies over time.
Which report should be compliance officer generate to obtain the compliance information?
A DLP administrator is checking the System Overview in the Enforce management console, and all of the detection servers are showing as “unknown”. The Vontu services are up and running on the detection servers. Thousands of .IDC files are building up in the Incidents directory on the detection servers. There is good network connectivity between the detection servers and the Enforce server when testing with the telnet command.
How should the administrator bring the detection servers to a running state in the Enforce management console?
Which two Infrastructure-as-a-Service providers are supported for hosting Cloud Prevent for Office 365? (Choose two.)
Which two Network Discover/Cloud Storage targets apply Information Centric Encryption as policy response rules?
A DLP administrator needs to stop the PacketCapture process on a detection server. Upon inspection of the Server Detail page, the administrator discovers that all processes are missing from the display.
What are the processes missing from the Server Detail page display?
Which two locations can Symantec DLP scan and perform Information Centric Encryption (ICE) actions on? (Choose two.)
A company needs to secure the content of all mergers and Acquisitions Agreements/ However, the standard text included in all company literature needs to be excluded.
How should the company ensure that this standard text is excluded from detection?
A DLP administrator needs to remove an agent its associated events from an Endpoint server.
Which Agent Task should the administrator perform to disable the agent’s visibility in the Enforce management console?
Which two factors are common sources of data leakage where the main actor is well-meaning insider? (Choose two.)
Which two detection technology options run on the DLP agent? (Choose two.)
How should a DLP administrator exclude a custom endpoint application named “custom_app.exe” from being monitoring by Application File Access Control?
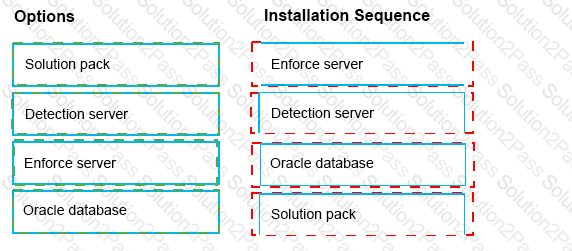
What is the correct installation sequence for the components shown here, according to the Symantec Installation Guide?
Place the options in the correct installation sequence.