250-440 Symantec Administration of Symantec PacketShaper 11.9.1 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Symantec 250-440 Administration of Symantec PacketShaper 11.9.1 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which steps will produce the data required to create an application-specific matching rule?
What is required on the network to allow classification of traffic flow by a specific user?
Which element is missing from this class lest statement?
# class test outbound 10.0.0.200:21 10.0.12.100:2000
Refer to the exhibit.
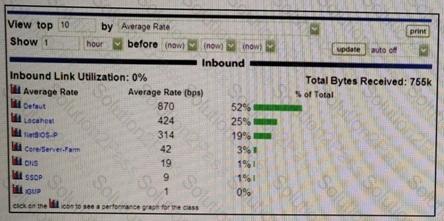
Which PacketShaper feature is shown here?
Which feature does PacketShaper use to control the rate lot User Datagram Protocol (UDP) traffic?
Traffic from a single internal server contains bandwidth peaking at 750K and averaging at 350K during sessions.
What information would anadministrate utilize to determine the rates to specify in a guaranteed rate policy for the traffic class?
What statement accurately describes Folder classes and Default classes?
Why is Layer 5 through 7 traffic grouped together in the PacketShaper?
Which three (3) criteria are to be specified in a matching rule? (Select three)
What statement accurately describes an ignore policy?
Which statement accurately describes rate policies and priority policies?
Which module allows an administrator to set bandwidth minimums and maximums, control bandwidth allocation, and ensure dear streams for voice and video?
An administratorsuspects that the primary BlueCoat Authentication and Authorization Agent (BCAAA) server has stopped functioning.When checking the status of UserAwarenesson the Setup > User Awareness page, the status message "In use" is displayed on the page.
What does the status "in use" mean?
After insulting a PacketShaper inline between a switch anda router, communications are slow.
Which command, executed repeatedly, can helpto determine it there ate errorson the PacketShaper interfaces?
What partitions could an administrator apply to a class in the Sky UI?
Which CLI command will display the current rate and connection information about active hosts?
Refer to the exhibit.
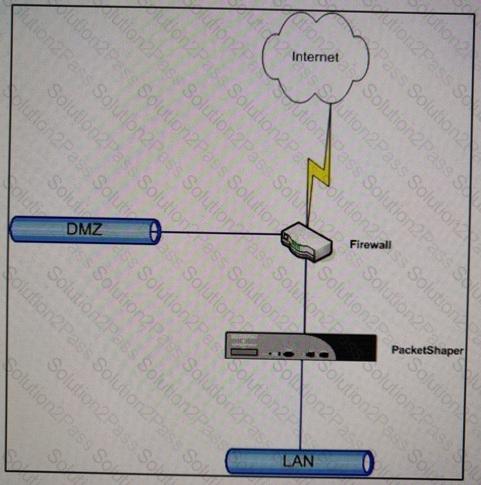
Which task must the administrator perform to make sure that traffic between (he IAN and DMZ is treated as pass-through PacketShaper installed as shown?
Which two (2) traffic types are ideal candidates for priority policies? (Select two)
What do instances of bold text in the PacfcetShapet Wffie lice represent?
Which statement accurately describes the PacketShaper measurement engine?
