250-441 Symantec Administration of Symantec Advanced Threat Protection 3.0 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Symantec 250-441 Administration of Symantec Advanced Threat Protection 3.0 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What are the prerequisite products needed when deploying ATP: Endpoint, Network, and Email?
Which two (2 non-Symantec method for restricting traffic are available to the Incident response team?
An organization has five (5) shops with a few endpoints and a large warehouse where 98% of all computers are located. The shops are connected to the warehouse using leased lines and access internet through the warehouse network.
How should the organization deploy the network scanners to observe all inbound and outbound traffic based on Symantec best practices for Inline mode?
What is a benefit of using Microsoft SQL as the Symantec Endpoint Protection Manager (SEPM) database in regard to ATP?
Which stage of an Advanced Persistent Threat (APT) attack do attackers break into an organization’s network
to deliver targeted malware?
What does a Quarantine Firewall policy enable an ATP Administrator to do?
An ATP administrator is setting up an Endpoint Detection and Response connection.
Which type of authentication is allowed?
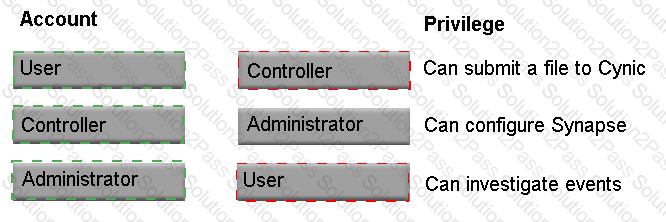
Which level of privilege corresponds to each ATP account type?
Match the correct account type to the corresponding privileges.
An Incident Responder notices traffic going from an endpoint to an IRC channel. The endpoint is listed in an
incident. ATP is configured in TAP mode.
What should the Incident Responder do to stop the traffic to the IRC channel?
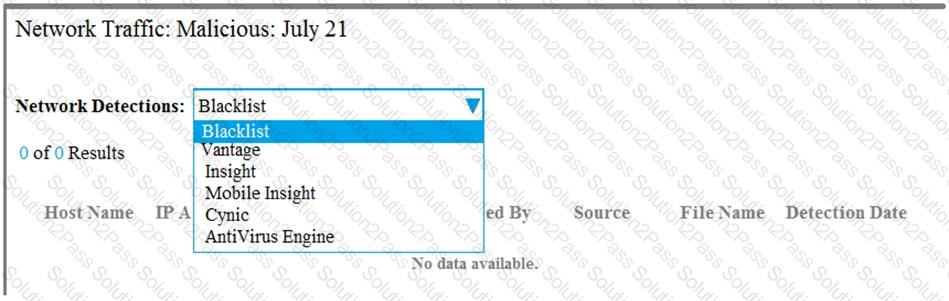
Refer to the exhibit. An Incident Responder wants to see what was detected on a specific day by the IPS engine.
Which item must the responder choose from the drop-down menu?
Which two ATP control points are able to report events that are detected using Vantage?
Enter the two control point names:
What occurs when an endpoint fails its Host Integrity check and is unable to remediate?
Which section of the ATP console should an ATP Administrator use to create blacklists and whitelists?
A customer has information about a malicious file that has NOT entered the network. The customer wants to know whether ATP is already aware of this threat without having to introduce a copy of the file to the infrastructure.
Which approach allows the customer to meet this need?
An ATP Administrator has deployed ATP: Network, Endpoint, and Email and now wants to ensure that all
connections are properly secured.
Which connections should the administrator secure with signed SSL certificates?
Which two user roles allow an Incident Responder to blacklist or whitelist files using the ATP manager?
(Choose two.)
An Incident Responder is going to run an indicators of compromise (IOC) search on the endpoints and wants
to use operators in the expression.
Which tokens accept one or more of the available operators when building an expression?
An organization is considering an ATP: Endpoint and Network deployment with multiple appliances.
Which form factor will be the most effective in terms of performance and costs?
An ATP administrator is setting up correlation with Email Security cloud.
What is the minimum Email Security cloud account privilege required?
An Incident Responder needs to remediate a group of endpoints but also wants to copy a potentially suspicious file to the ATP file store.
In which scenario should the Incident Responder copy a suspicious file to the ATP file store?