Deep-Security-Professional Trend Micro Certified Professional for Deep Security Exam Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Trend Micro Deep-Security-Professional Trend Micro Certified Professional for Deep Security Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Total 73 questions
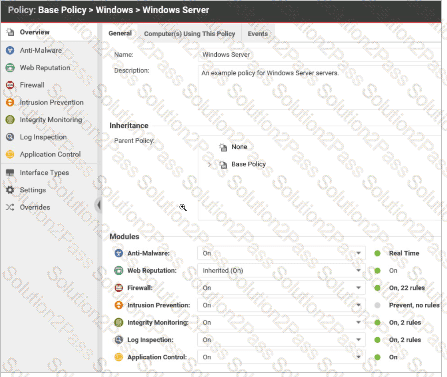
When viewing the details for a policy, as displayed in the exhibit, you notice that the Application Control Protection Module is not available. In this example, why would this Protection Modules not be available?
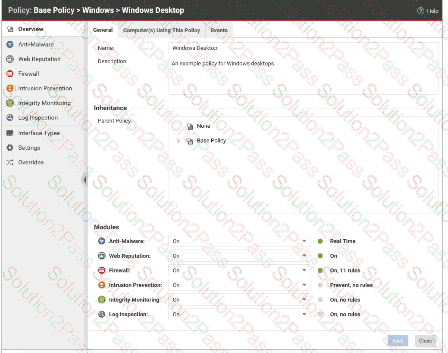
What is the result of performing a Reset operation on a Deep Security Agent?
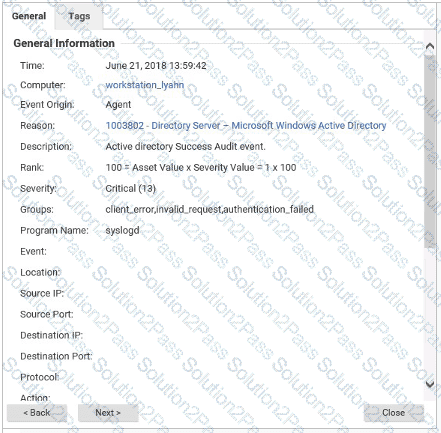
The details for an event are displayed in the exhibit. Based on these details, which Protection Module generated the event?
Which of the following statements is true regarding Deep Security Manager-todatabase com-munication?
Which of the following VMware components is not required to enable agentless protection using Deep Security.
A Recommendation Scan is run to determine which Intrusion Prevention rules are appropriate for a Server. The scan is configured to apply the suggested rules automatically and ongoing scans are enabled. Some time later, an operating system patch is applied. How can you determine which Intrusion Prevention rules are no longer needed on this Server?
Which of the following statements correctly describes Smart Folders?
Recommendation scans can detect applications and/or vulnerabilities on servers on the network. Which of the following Protection Modules make use of Recommendation scans?
What is the purpose of the override.properties file?
The Intrusion Prevention Protection Module is enabled, its Behavior is set to Prevent and rules are assigned. When viewing the events, you notice that one of Intrusion Prevention rules is being triggered and an event is being logged but the traffic is not being blocked. What is a possible reason for this?
Your organization stores PDF and Microsoft Office files within the SAP Netweaver platform and requires these documents to be scanned for malware. Which Deep Security component is required to satisfy this requirement?
The maximum disk space limit for the Identified Files folder is reached. What is the expected Deep Security Agent behavior in this scenario?
In the policy displayed in the exhibit, the state of the Web Reputation Protection Module is set to "Inherited (On)", while the state for the other Protection Module is set to "On". Why is the Web Reputation Protection Module displayed differently than the other Protection Modules.
Where does Deep Security Manager store the credentials it uses to access the database?
How is scan caching used in agentless implementations of Deep Security?
Which of the following statements is true regarding the Log Inspection Protection Module?
New servers are added to the Computers list in Deep Security Manager Web config by running a Discover operation. What behavior can you expect for newly discovered computers?
The Firewall Protection Module is enabled on a server through the computer details. What is default behavior of the Firewall if no rules are yet applied?
Which of the following statements correctly identifies the purpose of the Integrity Monitoring Protection Module?
Which of the following statements is true regarding Deep Security Relays?
Total 73 questions
