2V0-41.23 VMware NSX 4.x Professional Free Practice Exam Questions (2026 Updated)
Prepare effectively for your VMware 2V0-41.23 VMware NSX 4.x Professional certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which choice is a valid insertion point for North-South network introspection?
A security administrator needs to configure a firewall rule based on the domain name of a specific application.
Which field in a distributed firewall rule does the administrator configure?
An administrator wants to validate the BGP connection status between the Tier-O Gateway and the upstream physical router.
What sequence of commands could be used to check this status on NSX Edge node?
Which three DHCP Services are supported by NSX? (Choose three.)
What are two valid BGP Attributes that can be used to influence the route path traffic will take? (Choose two.)
Which command on ESXI is used to verify the Local Control Plane connectivity with Central Control Plane?
A)
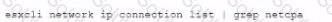
B)
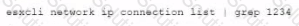
C)
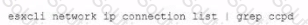
D)

When deploying an NSX Edge Transport Node, what two valid IP address assignment options should be specified for the TEP IP addresses? (Choose two.)
Which CLI command does an NSX administrator run on the NSX Manager to generate support bundle logs if the NSX UI Is inaccessible?
What can the administrator use to identify overlay segments in an NSX environment if troubleshooting is required?
Which steps are required to activate Malware Prevention on the NSX Application Platform?
Which two BGP configuration parameters can be configured in the VRF Lite gateways? (Choose two.)
When running nsxcli on an ESXi host, which command will show the Replication mode?
Which of the two following characteristics about NAT64 are true? (Choose two.)
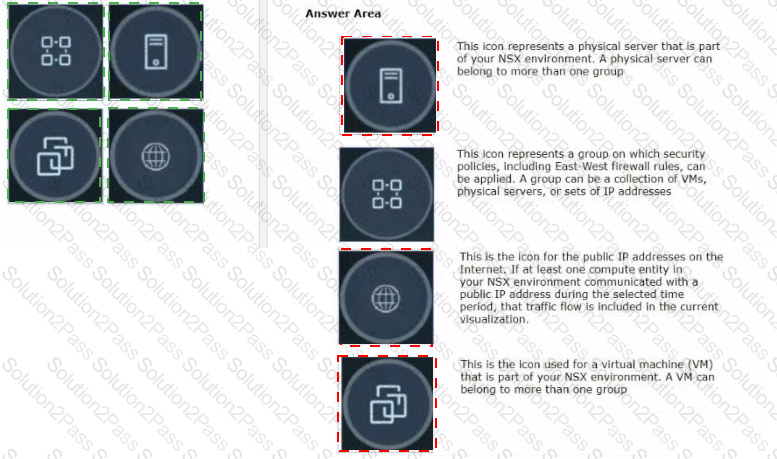
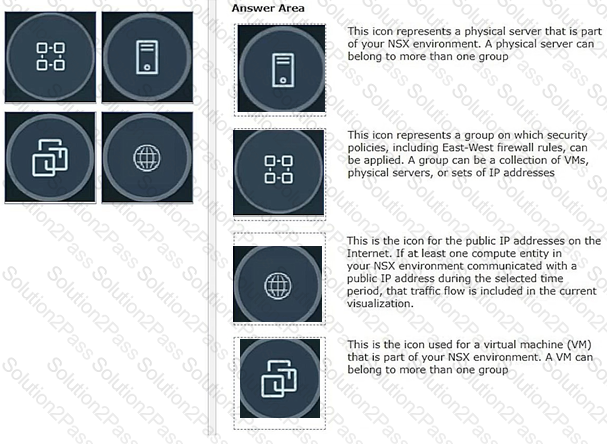
Refer to the exhibits.
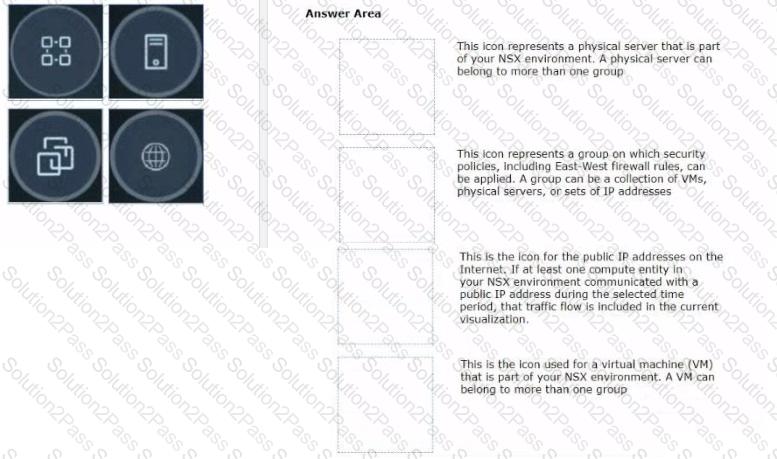
Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.
Which three data collection sources are used by NSX Network Detection and Response to create correlations/Intrusion campaigns? (Choose three.)
Which two are requirements for FQDN Analysis? (Choose two.)
Which NSX feature can be leveraged to achieve consistent policy configuration and simplicity across sites?
The security administrator turns on logging for a firewall rule.
Where is the log stored on an ESXi transport node?
NSX improves the security of today's modern workloads by preventing lateral movement, which feature of NSX can be used to achieve this?
An NSX administrator Is treating a NAT rule on a Tler-0 Gateway configured In active-standby high availability mode. Which two NAT rule types are supported for this configuration? (Choose two.)