5V0-41.21 VMware NSX-T Data Center 3.1 Security Free Practice Exam Questions (2026 Updated)
Prepare effectively for your VMware 5V0-41.21 VMware NSX-T Data Center 3.1 Security certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which dot color indicates an on-going attack of medium severity in the IDS/IPS events tab of NSX-T Data Center?
An NSX administrator has turned on logging for the distributed firewall rule. On an ESXi host, where will the logs be stored?
In a brownfield environment with NSX-T Data Center deployed and configured, a customer is interested in Endpoint Protection integrations. What recommendation should be provided to the customer when it comes to their existing virtual machines?
Which is the port number used by transport nodes to export firewall statistics to NSX Manager?
A security administrator has configured NSX Intelligence for discovery. They would like to get recommendations based on the changes in the scope of the input entities every hour.
What needs to be configured to achieve the requirement?
How does N5X Distributed IDS/IPS keep up to date with signatures?
At which two intervals are NSX-T IDS/IPS updates through VMware's cloud based internet service provided for threat signature files? (Choose two.)
What needs to be configured on each transport node prior to using NSX-T Data Center Distributed Firewall time-based rule publishing?
An administrator needs to configure their NSX-T logging to audit changes on firewall security policy. The administrator Is using the following command from NSX-T3.1 documentation :

Which Message ID from the following list will allow the administrator to track changes on firewall security rules?
An administrator wants to use Distributed Intrusion Detection. How is this implemented in an NSX-T Data Center?
Information Security Management (ISM) describes a set of controls that organizations employ to protect which properties?
A security administrator recently enabled Guest Introspection on NSX-T Data Center.
Which would be a reason none of the Microsoft Windows based VMs are reporting any information?
As part of an audit, an administrator is required to demonstrate that measures have been taken to prevent critical vulnerabilities from being exploited. Which Distributed IDS/IPS event filter can the administrator show as proof?
To which object can time based rules be applied?
A Security Administrator needs to update their NSX Distributed IDS/IPS policy to detect new attacks with critical CVSS scoring that leads to credential theft from targeted systems.
Which actions should you take?
A security administrator is required to protect East-West virtual machine traffic with the NSX Distributed Firewall. What must be completed with the virtual machine's vNIC before applying the rules?
Refer to the exhibit.
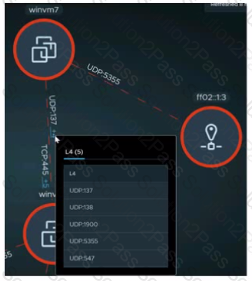
An administrator is reviewing NSX Intelligence information as shown in the exhibit.
What does the red dashed line for the UDP:137 flow represent?
An NSX administrator is trying to find the dvfilter name of the sa-web-01 virtual machine to capture the sa-web-01 VM traffic. What could be a reason the sa-web-01 VM dvfilter name is missing from the command output?
Which is an insertion point for East-West service insertion?
What is the default action of the Default Layer 3 distributed firewall rule?
