9L0-415 Apple OS X Support Essentials 10.9 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Apple 9L0-415 OS X Support Essentials 10.9 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
When a user logs in, which task is NOT performed by the user's loginwindow or launchd processes?
Review the screenshots of a Mac computer's Network pane, and then answer the question below.
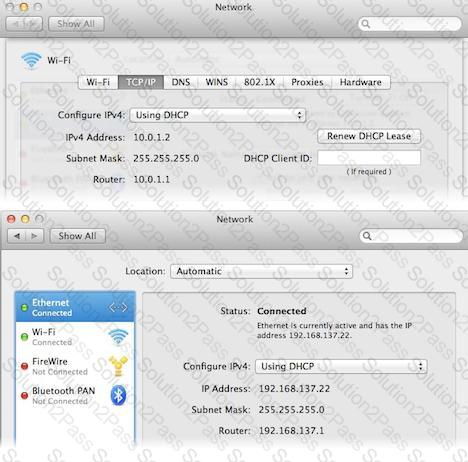
If a Mac with the network configuration shown above needs to initiate a connection to a server at address 17.20.8.9, which interface will it use to do so?
You want to delete several applications by dragging them to the Trash. What fact should you be aware of?
In OS X, Disk Utility can create file archives in which format?
In a default OS X configuration, you want to change the way that Finder handles ZIP archives. Where can you make that change?
In what order do these three OS X components load at startup?
On your OS X Mountain Lion computer, you want the Finder to display filename extensions by default. How can you configure this setting from the Finder?
When a user opens an application, in what order does OS X Mountain Lion search the three Library folders in the local file system for resources that the application needs to access, such as fonts?
You are logged into a MacBook Pro as a standard user. How can you display the OS X Mountain Lion build number?
What is a valid reason to start up a Mac in verbose mode?
How do you start up an OS X Mountain Lion computer in single-user mode?
Review the screenshot and answer the question below.
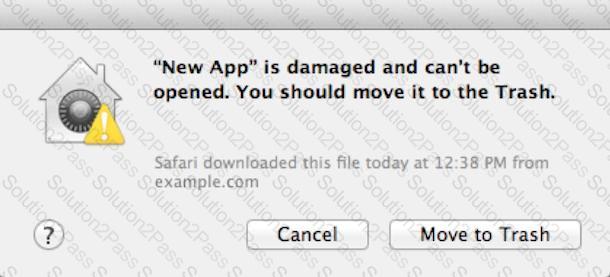
You downloaded an app using Safari. When you try to open the app, you see the message shown above. What is a possible explanation?
The function of journaling in the Mac OS Extended (Journaled) file system is to ________.
Why would you want to open an application in 32-bit mode?
How can an OS X system automatically connect to a Wi-Fi network?
All Apple software updates are handled via the Mac App Store.
How does the OS X built-in firewall work?
You can choose to ignore ownership on any non system volume. This will ignore any ownership rules and grant any logged-on user unlimited access to the contents of the volume. It's a potential security risk because it will allow any local user account to have full access to the volume, even if that user didn't originally mount the volume.
How can you encrypt a disk without losing its contents?
If an issue disappears when a Safe Boot is successful, you must find and remove the third-party startup resource that caused the issue. The best way to isolate the problem is to start up the Mac in Verbose mode and then observe where the startup process fails. Verbose mode is initiated by holding down Command-V during system startup.
