200-201 Cisco Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit.
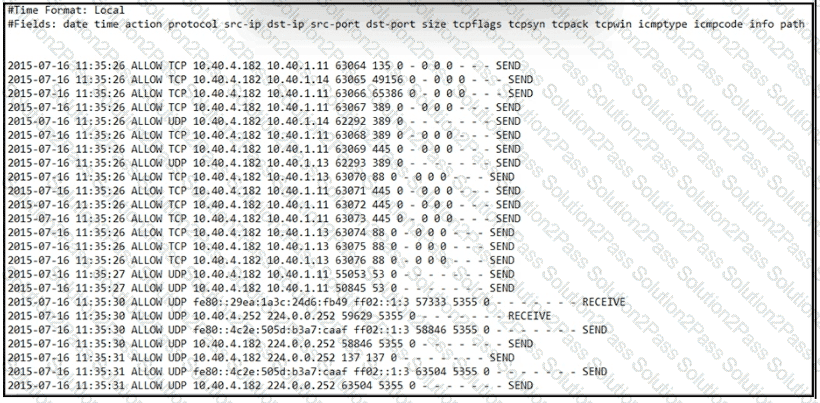
An engineer received an event log file to review. Which technology generated the log?
Refer to the exhibit.
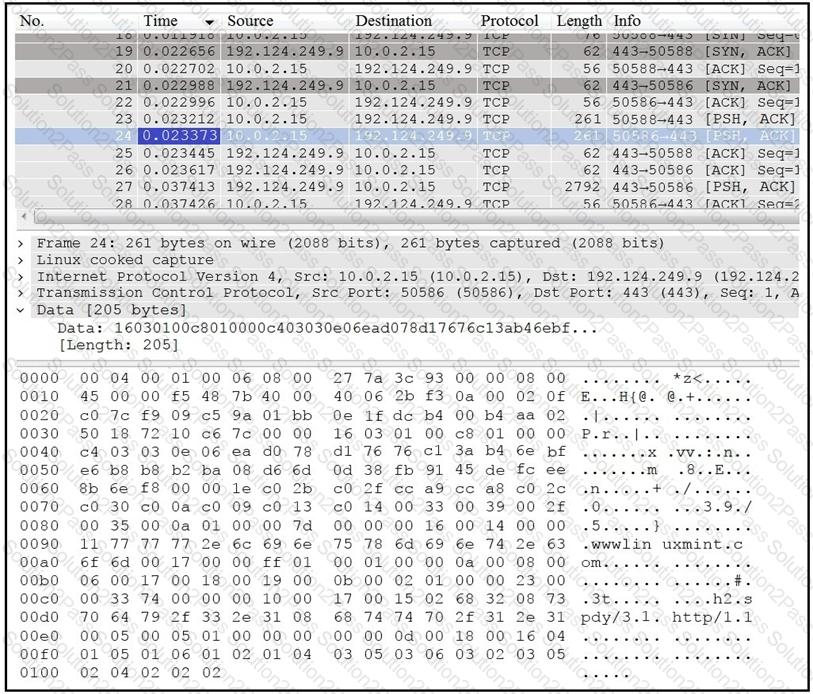
Which application protocol is in this PCAP file?
An engineer discovered a breach, identified the threat’s entry point, and removed access. The engineer was able to identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step the engineer should take according to the NIST SP 800-61 Incident handling guide?
Why should an engineer use a full packet capture to investigate a security breach?
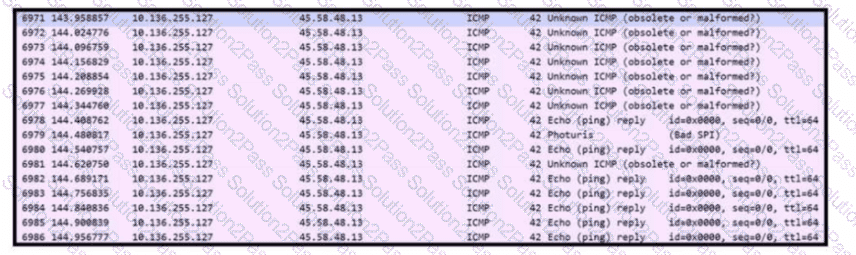
Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is occurring?
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group.
What is the initial event called in the NIST SP800-61?
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external penmeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified'? (Choose two.)
What does cyber attribution identify in an investigation?
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
Refer to the exhibit.
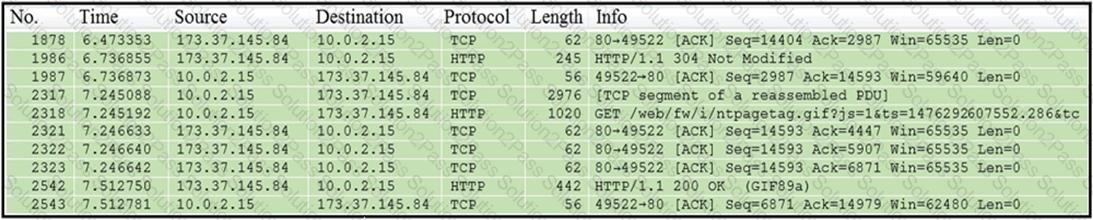
Which packet contains a file that is extractable within Wireshark?
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
What is the difference between indicator of attack (loA) and indicators of compromise (loC)?
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, "File: Clean." Which regex must the analyst import?
Refer to the exhibit.
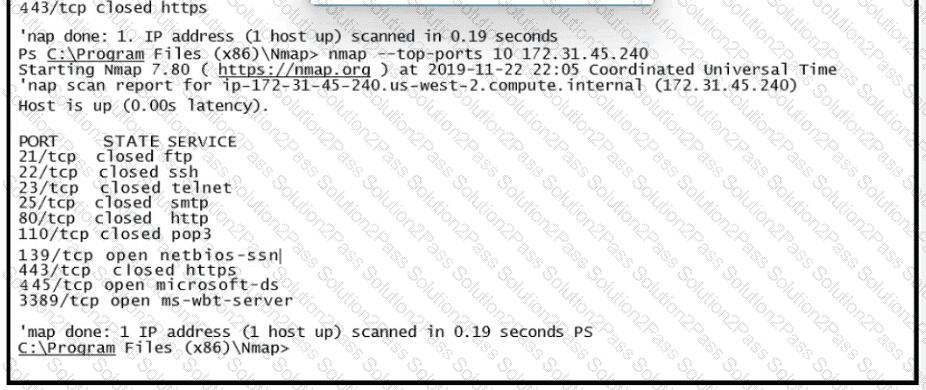
What does this output indicate?
Refer to the exhibit.
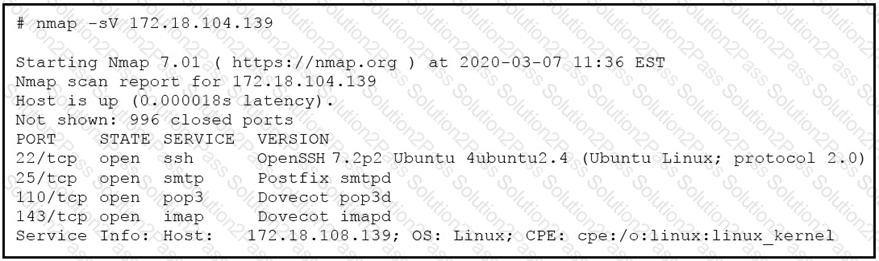
What does the output indicate about the server with the IP address 172.18.104.139?
A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and writes to a new PHP file on the webserver. Which event category is described?
What is the role of indicator of compromise in an investigation?
Refer to the exhibit.
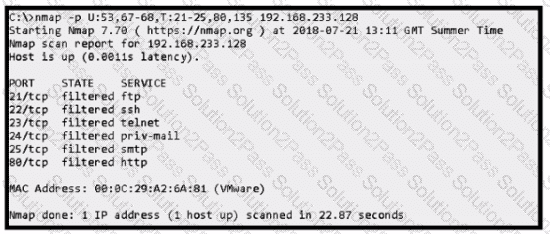
An attacker scanned the server using Nmap.
What did the attacker obtain from this scan?
According to CVSS, what is attack complexity?
What is a difference between authorization and authentication from an access control perspective?
