200-201 Cisco Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit.

Which application-level protocol is being targeted?
What is the communication channel established from a compromised machine back to the attacker?
A cyberattacker notices a security flaw in a software that a company is using They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software To which category of the Cyber Kill Cham model does this event belong?
Which of these describes volatile evidence?
An engineer received an alert affecting the degraded performance of a critical server. Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
An engineer received a flood of phishing emails from HR with the source address HRjacobm@companycom. What is the threat actor in this scenario?
What are two differences of deep packet inspection compared to stateful firewall inspection? (Choose two.)
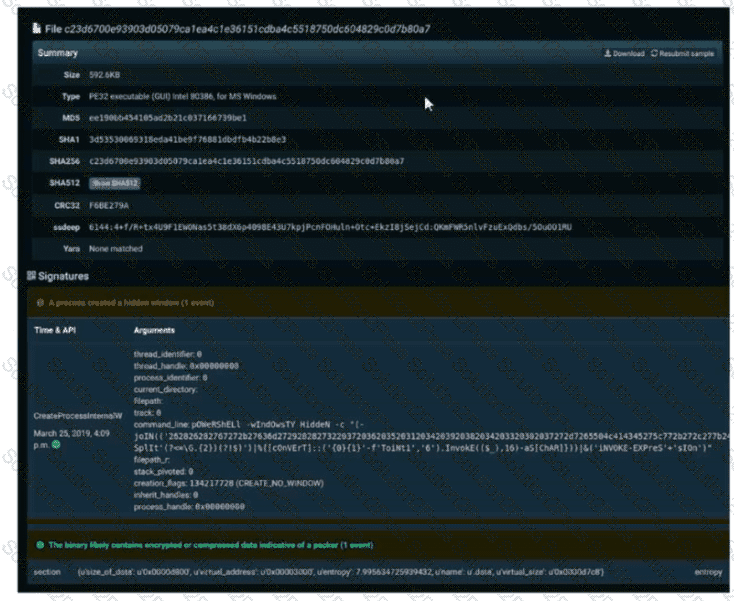
Refer to the exhibit. A SOC engineer is analyzing Cuckoo Sandbox report for a file that has been identified as suspicious by the endpoint security system. What is the state of the file?
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
An analyst discovers that a legitimate security alert has been dismissed. Which signature caused this impact on network traffic?
Which evasion method involves performing actions slower than normal to prevent detection?
What are the two differences between vulnerability and exploit? (Choose two.)
Developers must implement tasks on remote Windows environments. They decided to use scripts for enterprise applications through PowerShell. Why does the functionality not work?
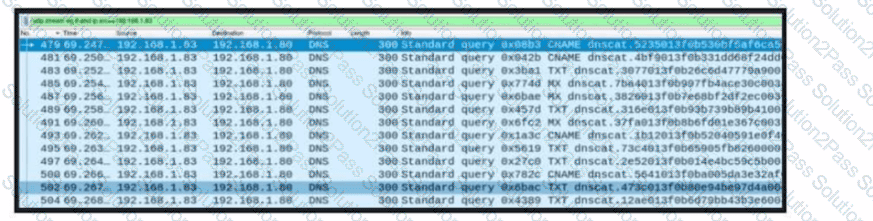
Refer to the exhibit. A network engineer received a report that a host is communicating with unknown domains on the internet. The network engineer collected packet capture but could not determine the technique or the payload used. What technique is the attacker using?
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
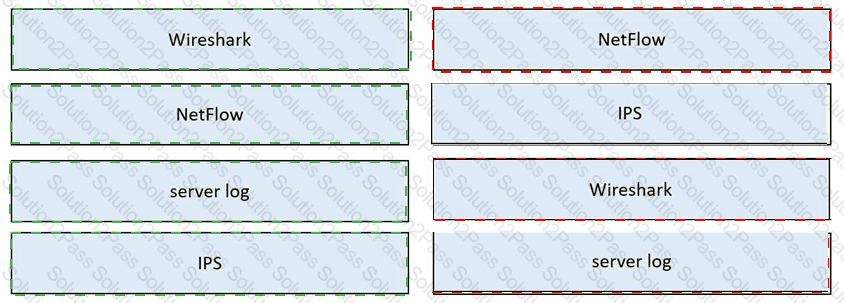
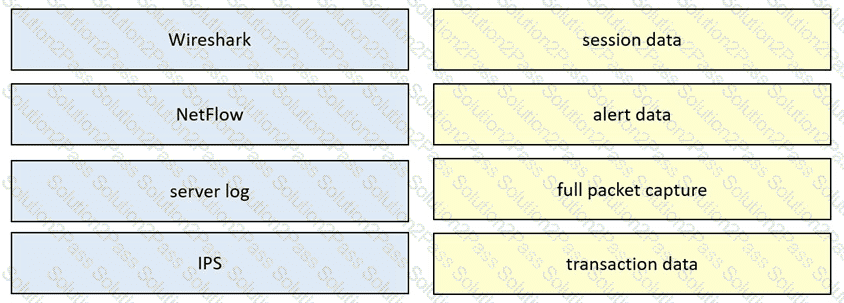
Drag and drop the data source from the left onto the data type on the right.
Which classification of cross-site scripting attack executes the payload without storing it for repeated use?
What is the difference between inline traffic interrogation and traffic mirroring?
Refer to the exhibit.
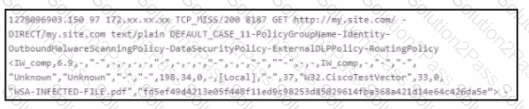
Which technology produced the log?
What is the virtual address space for a Windows process?