200-201 Cisco Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is the difference between inline traffic interrogation (TAPS) and traffic mirroring (SPAN)?
Which technique is a low-bandwidth attack?
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
What are two denial-of-service (DoS) attacks? (Choose two)
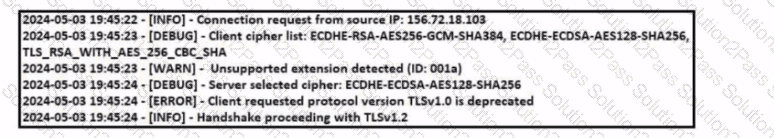
Refer to the exhibit Which TLS version does this client support?
Refer to the exhibit.
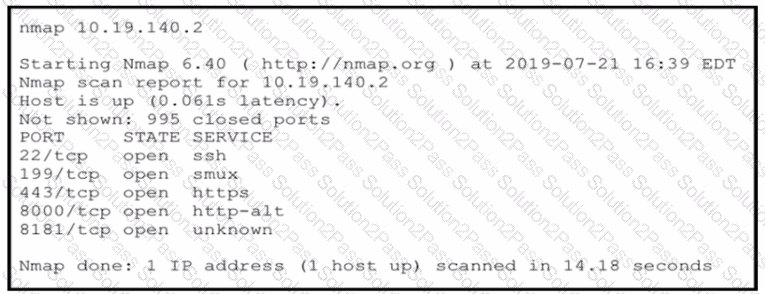
An attacker gained initial access to the company s network and ran an Nmap scan to advance with the lateral movement technique and to search the sensitive data Which two elements can an attacker identify from the scan? (Choose two.)
Refer to exhibit.
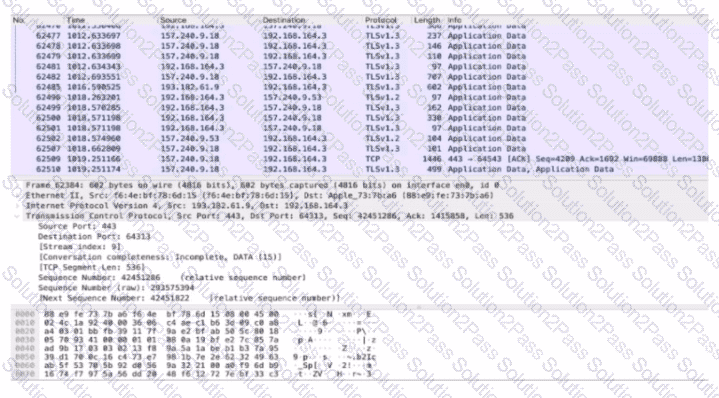
An analyst performs the analysis of the pcap file to detect the suspicious activity. What challenges did the analyst face in terms of data visibility?
Why is encryption challenging to security monitoring?
What is a difference between tampered and untampered disk images?
What are indicators of attack?
Which data type is necessary to get information about source/destination ports?
Which type of evidence supports a theory or an assumption that results from initial evidence?
Refer to the exhibit.

An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?
What is data encapsulation?
An analyst performs traffic analysis to detect data exfiltration and identifies a high frequency of DNS requests in a small period of time Which technology makes this behavior feasible?
Refer to the exhibit.

In which Linux log file is this output found?
Exhibit.
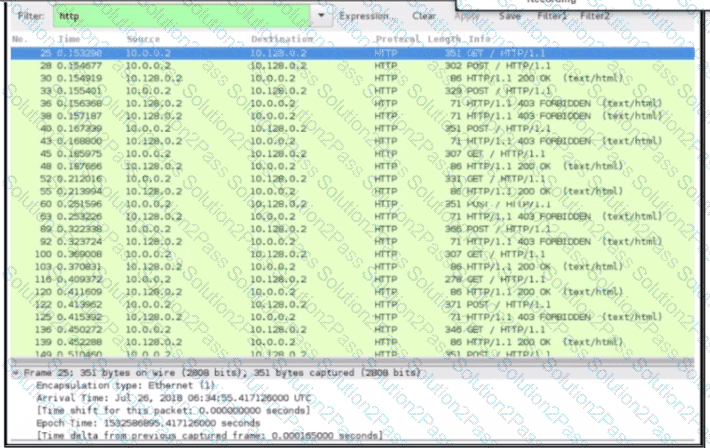
An engineer received a ticket about a slowdown of a web application, Drug analysis of traffic, the engineer suspects a possible attack on a web server. How should the engineer interpret the Wiresharat traffic capture?
What is threat hunting?
After a large influx of network traffic to externally facing devices, a security engineer begins investigating what appears to be a denial of service attack When the packet capture data is reviewed, the engineer notices that the traffic is a single SYN packet to each port Which type of attack is occurring?
At a company party a guest asks questions about the company’s user account format and password complexity. How is this type of conversation classified?
