200-201 Cisco Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is a scareware attack?
Which HTTP header field is used in forensics to identify the type of browser used?
A SOC analyst detected connections to known C&C and port scanning activity to main HR database servers from one of the HR endpoints via Cisco StealthWatch. What are the two next steps of the SOC team according to the NISTSP800-61 incident handling process? (Choose two)
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
What is the benefit of processing statistical data for security systems?
What is a difference between signature-based and behavior-based detection?
Refer to the exhibit.
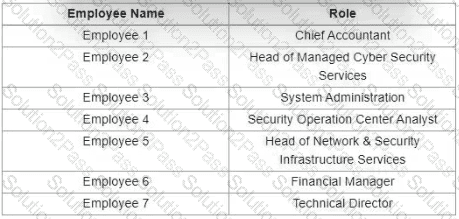
Which stakeholders must be involved when a company workstation is compromised?
Refer to the exhibit.
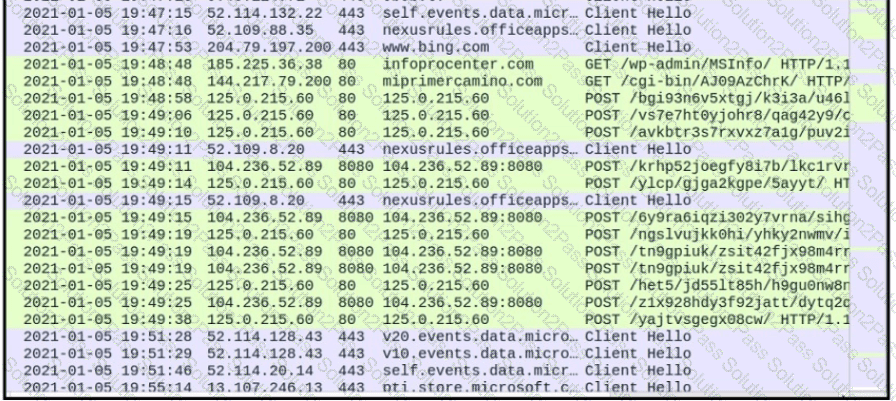
What is occurring?
Which risk approach eliminates activities posing a risk exposure?
Which type of data collection requires the largest amount of storage space?
A security analyst reviews the firewall and observes the large number of frequent events. The analyst starts the packet capture with the Wireshark and identifies that TCP port reuse was detected incorrectly as a TCP split-handshake attack by the firewall. How must an impact from this event be categorized?
A suspicious user opened a connection from a compromised host inside an organization. Traffic was going through a router and the network administrator was able to identify this flow. The admin was following 5-tuple to collect needed data. Which information was gathered based on this approach?
What describes the usage of a rootkit in endpoint based attacks?

Refer to the exhibit. The figure shows an X 509 certificate. Which field represents the digital cryptographic algorithm used by the issuer to sign the certificate?
What is a description of "phishing" as a social engineering attack"?
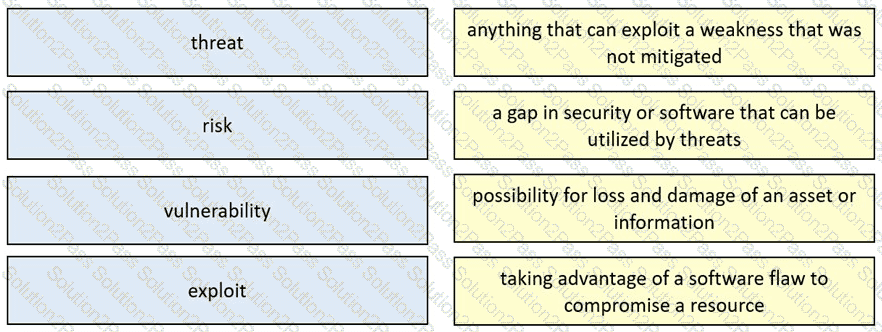
Drag and drop the security concept from the left onto the example of that concept on the right.
An organization's security team has detected network spikes coming from the internal network. An investigation has concluded that the spike in traffic was from intensive network scanning How should the analyst collect the traffic to isolate the suspicious host?
Refer to the exhibit.
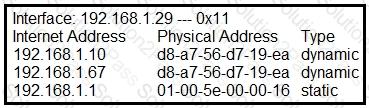
What is occurring in this network?
What is the purpose of a ransomware attack?
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?
 Table
Description automatically generated
Table
Description automatically generated