200-201 Cisco Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is a sandbox interprocess communication service?
What should an engineer use to aid the trusted exchange of public keys between user tom0411976943 and dan1968754032?
An engineer is working on the implementation of digital certificates for new cntical web applications One of the requirements is that the https connection must be validated and protected against malicious network impersonators The server will be exposed externally from the DMZ network Which certificate must be used?
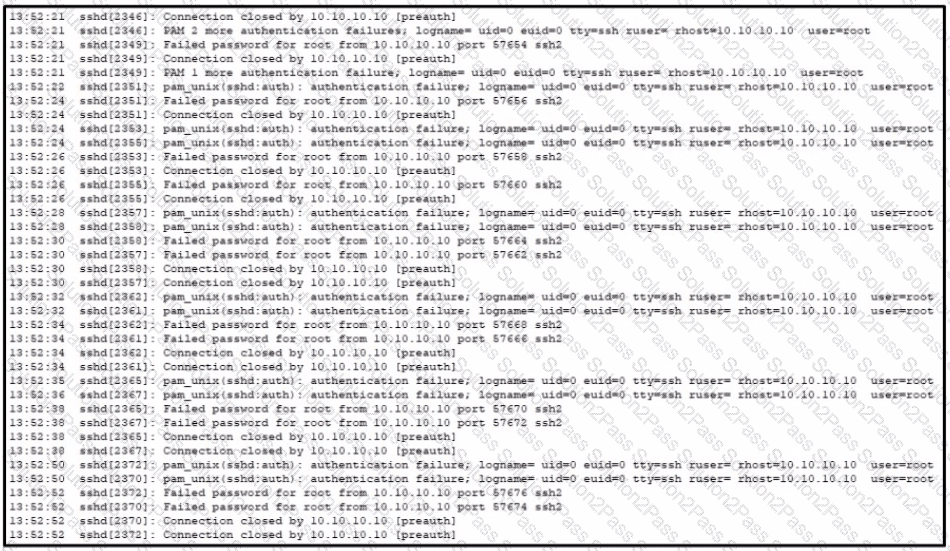
Refer to the exhibit A SOC analyst is examining the Auth.log file logs of one the breached systems What is the possible reason for this event log?
Which category relates to improper use or disclosure of PII data?
How does an attack surface differ from an attack vector?

Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
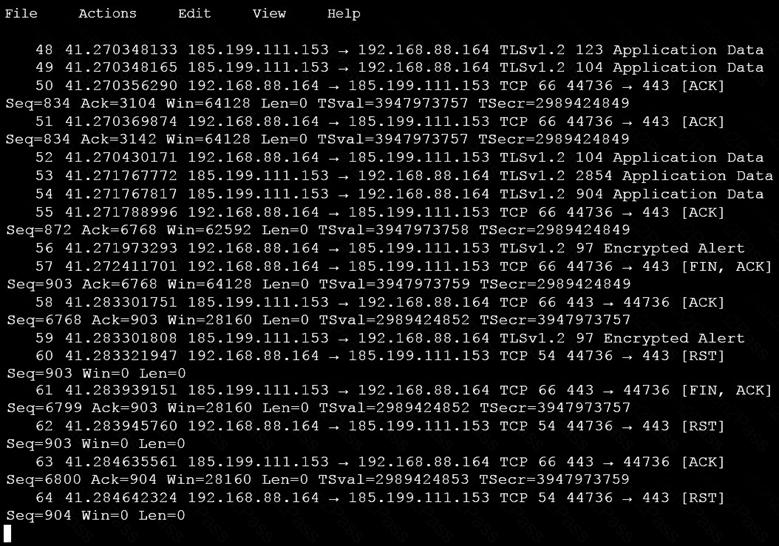
Which obfuscation technique is the attacker using?
What is the difference between the ACK flag and the RST flag?
How does agentless monitoring differ from agent-based monitoring?
What are the two characteristics of the full packet captures? (Choose two.)
The SOC team detected an ongoing port scan. After investigation, the team concluded that the scan was targeting the company servers. According to the Cyber Kill Chain model, which step must be assigned to this type of event?
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving an SYN-ACK while establishing a session by sending the first SYN. What is causing this issue?
What describes the concept of data consistently and readily being accessible for legitimate users?
Refer to the exhibit.
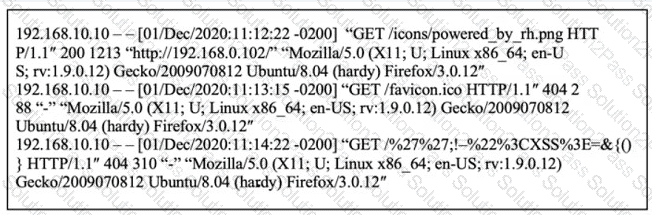
What is occurring within the exhibit?
What is a benefit of agent-based protection when compared to agentless protection?
In digital communications, which method is recommended for securely exchanging public keys between users T0n2262144790 and D4n4126220794?
What is the functionality of an IDS'?
Which are two denial-of-service attacks? (Choose two.)
A CMS plugin creates two files that are accessible from the Internet myplugin html and exploitable php A newly discovered exploit takes advantage of an injection vulnerability m exploitable php To exploit the vulnerability an HTTP POST must be sent with specific variables to exploitable php A security engineer notices traffic to the webserver that consists of only HTTP GET requests to myplugin html Which category does this activity fall under?
