200-201 Cisco Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An engineer must investigate suspicious connections. Data has been gathered using a tcpdump command on a Linux device and saved as sandboxmatware2022-12-22.pcaps file.The engineer is trying to open the tcpdump in the Wireshark tool. What is the expected result?
Refer to the exhibit.
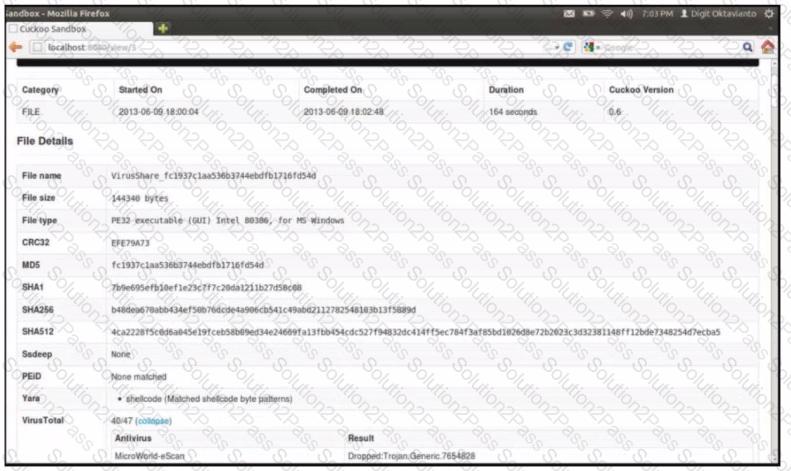
What does this Cuckoo sandbox report indicate?
Why is HTTPS traffic difficult to screen?
Which type of data consists of connection level, application-specific records generated from network traffic?
Refer to the exhibit.

Which type of attack is being executed?
Endpoint logs indicate that a machine has obtained an unusual gateway address and unusual DNS servers via DHCP Which type of attack is occurring?
Which two measures are used by the defense-m-depth strategy? (Choose two)
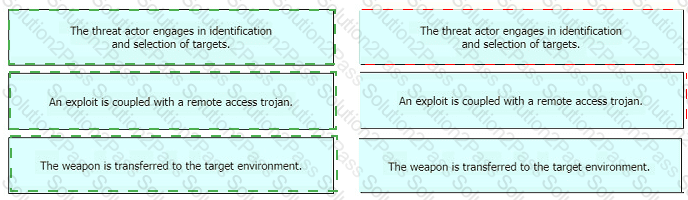
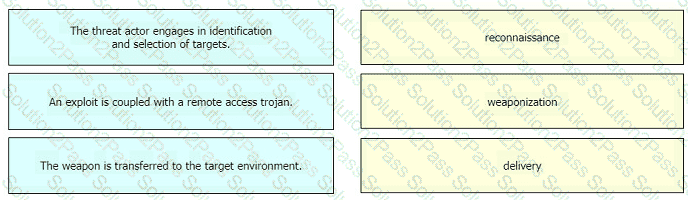
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
An engineer is working on a ticket for an incident from the incident management team A week ago. an external web application was targeted by a DDoS attack Server resources were exhausted and after two hours it crashed. An engineer was able to identify the attacker and technique used Three hours after the attack, the server was restored and the engineer recommended implementing mitigation by Blackhole filtering and transferred the incident ticket back to the IR team According to NIST SP800-61, at which phase of the incident response did the engineer finish work?
Refer to the exhibit.
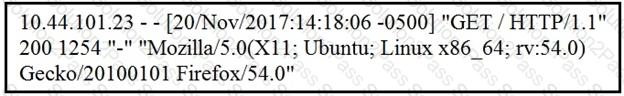
What does the message indicate?
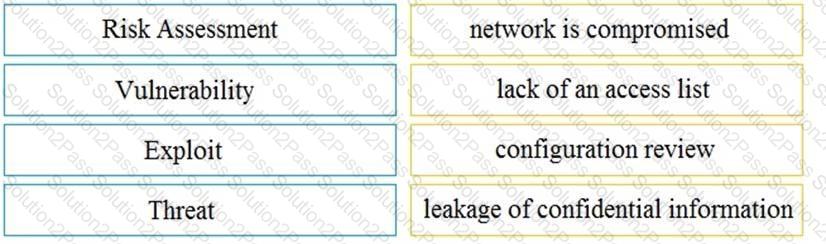
Drag and drop the security concept on the left onto the example of that concept on the right.
What is the difference between antimalware and antivirus solutions?
What is the difference between deep packet inspection and stateful inspection?
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
A security engineer must determine why a new core application does not work as desired The client can send requests toward the application server but receives no response One of the requirements is to gather all packets Data needs to be reliable without any delay or packet drops Which solution best meets this need?
Refer to the exhibit.
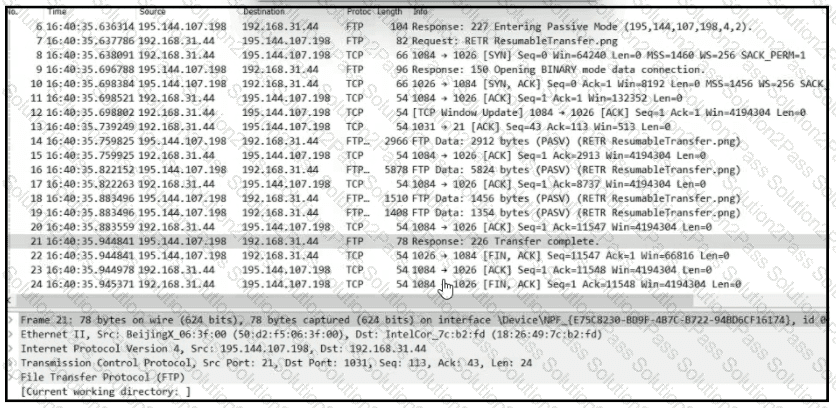
Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
An engineer configured regular expression “.”\.(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1 .[01]" on Cisco ASA firewall. What does this regular expression do?
What is the difference between deep packet inspection and stateful inspection?
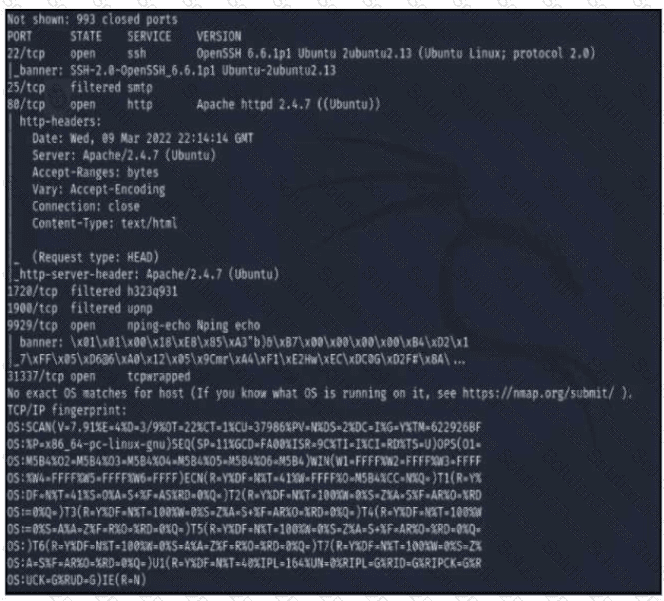
Refer to the exhibit A penetration tester runs the Nmap scan against the company server to uncover possible vulnerabilities and exploit them Which two elements can the penetration tester identity from the scan results? (Choose two.)
What is the impact of encapsulation on the network?