200-301 Cisco Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 200-301 Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which statement describes virtual machines?
Refer to the exhibit. A secondary route is required on router R1 to pass traffic to the LAN network on R2 if the primary link fails. Which command must be entered to configure the router?
Which role do predictive Al models play in network load balancing?
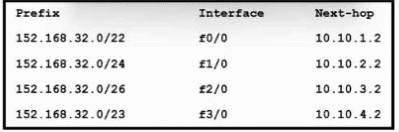
Refer to the exhibit. Which next hop is used to route packets to the application server at 152.168.32.85?
Which two northbound APIs are found in a software-defined network? (Choose two.)
Which interface is used to send traffic to the destination network?
10.249.210.56/25 [90/6144] via G0/15
10.249.210.56/25 [90/45053] via G0/13
10.249.210.56/25 [110/3693] via G0/16
10.249.210.56/25 [110/360] via G0/12
Which two QoS tools provide congestion management? (Choose two.)
Which interface is used to send traffic to the destination network?
O 10.18.75.113/27 [110/6906] via GO/6
O 10.18.75.113/27 [110/23018] via GO/3
R 10.18.75.113/27 [120/16] via GO/16
R 10.18.75.113/27 [120/14] via GO/23
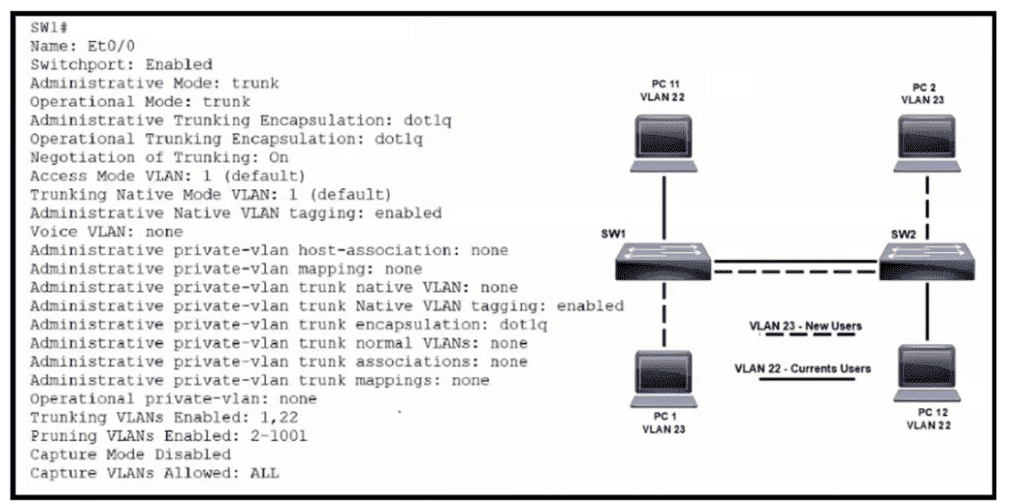
Refer to the exhibit. VLAN 23 is being implemented between SW1 and SW2. The command show interface ethernet0/0 switchport has been issued on SW1. Ethernet0/0 on SW1 is the uplink to SW2. Which command when entered on the uplink interface allows PC 1 and PC 2 to communicate without impact to the communication between PC 11 and PC 12?
What is the function of generative AI in network operations?
What is a characteristic of private IPv4 addressing?
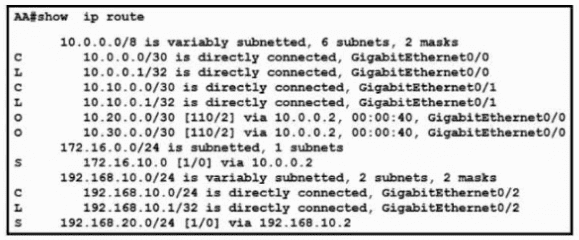
Refer to the exhibit. What is the administrative distance for the advertised prefix that includes the host IP address 10.30.0.1?
Which interface is used to send traffic to the destination network?
O 10.76.170 161/26 |110/102] via FO/17
O 10.76.170 161/26[110/27e31] via FO/20
R 10.76.170.161/261120/15] via FO/8
R 10.76.170.161/26 [120/10] via FO/12
What is an advantage of using SDN versus traditional networking when it comes to security?
In which way does generative AI aid network simulations?
How does MAC learning function?
What is a characteristic of private IPv4 addressing?
What is a characteristic of private IPv4 addressing?
Which IP address is used when an administrator must open a web-based management session with a lightweight AP?
Where are the real-time control functions processed in a split MAC architecture?
Which header must be included in a REST request from an application that requires JSON-formatted content?
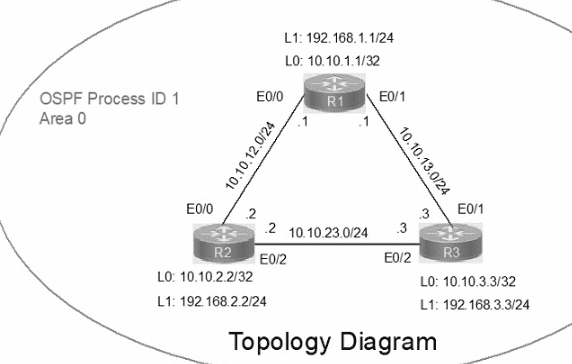
IP connectivity between the three routers is configured. OSPF adjacencies must be established.
1. Configure R1 and R2 Router IDs using the interface IP addresses from the link that is shared between them.
2. Configure the R2 links with a max value facing R1 and R3. R2 must become the DR. R1 and R3 links facing R2 must remain with the default OSPF configuration for DR election. Verify the configuration after clearing the OSPF process.
3. Using a host wildcard mask, configure all three routers to advertise their respective Loopback1 networks.
4. Configure the link between R1 and R3 to disable their ability to add other OSPF routers.
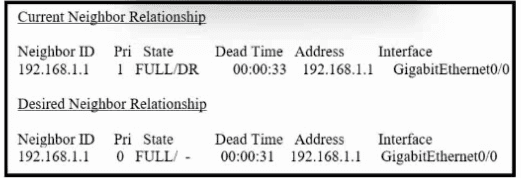
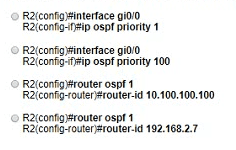
Refer to the exhibit. How must OSPF be configured on the GigabitEthernet0/0 interface of the neighbor device to achieve the desired neighbor relationship?
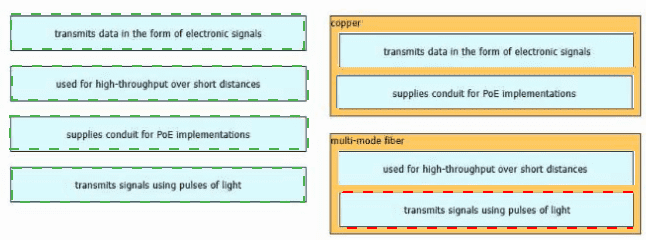
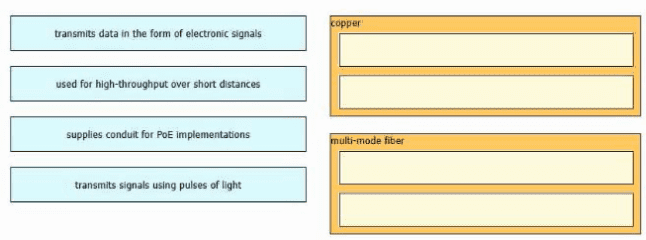
Drag and drop the characteristic from the left onto the cable type on the right.
Which action prevents debug messages from being sent via syslog while allowing other messages when an abnormally high number of syslog messages are generated by a device with the debug process turned on?
Which type of protocol is VRRP?
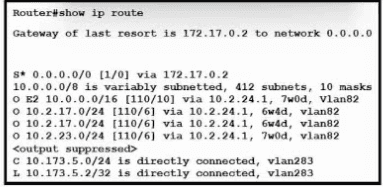
Refer to the exhibit. What is the value of the administrative distance for the default gateway?
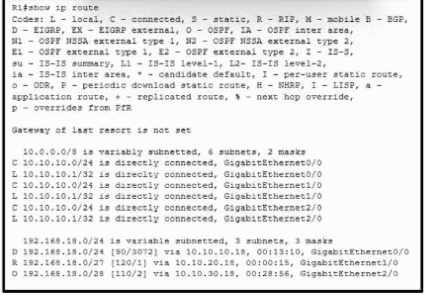
Refer to the exhibit. Which interface does a packet take to reach the host address of 192.168.18.16?
How does MAC learning function?
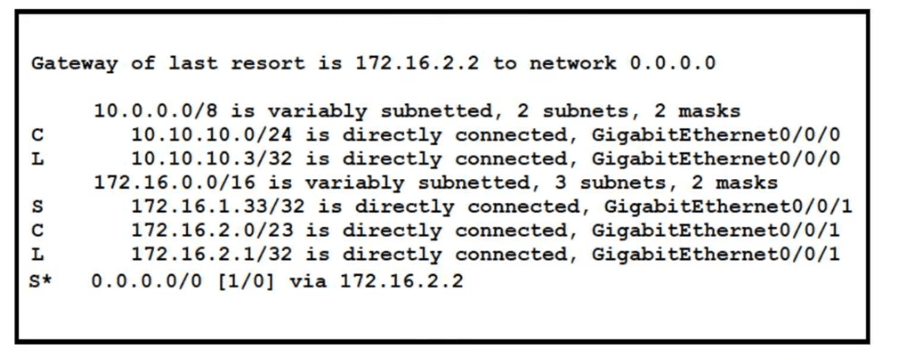
Refer to the exhibit. A packet sourced from 10.10.10.1 is destined for 172.16.3.254. What is the subnet mask of the destination route?
A default route must be configured to temporarily use a local broadband modem with the IP address of 192.168.1.1 until a WAN circuit is installed. The WAN circuit will use an external routing protocol that exchanges network prefixes between two separate autonomous systems on the Internet. Only a default route will be received by the ISP Which configuration must be applied to allow the new WAN circuit to take precedence when It Is In place?
What is the maximum length of characters used in an SSID?
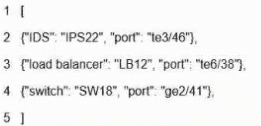
What is represented by the word "switch" within this JSON schema?
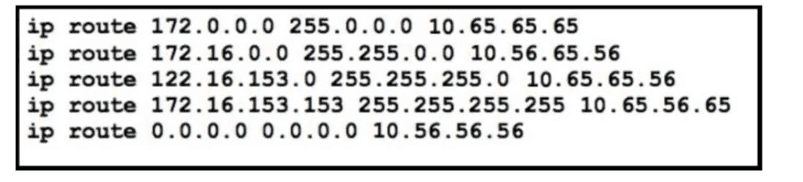
Refer to the exhibit. The static routes were implemented on the border router. What is the next hop IP address for a ping sent to 172.16.153.154 from the border router?
Refer to the exhibit.
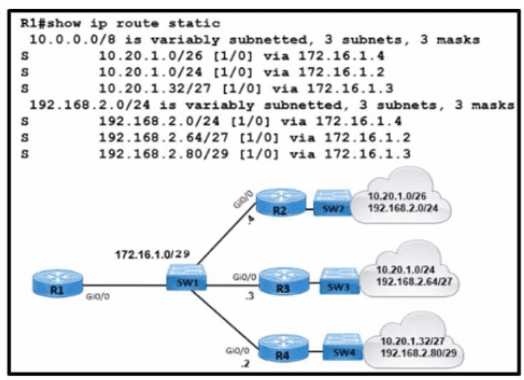
What is the correct next hop for router R1 to reach IP addresses 192.168.2.86 and 10.20.1.50?
What is the default interface for in-band wireless network management on a WLC?
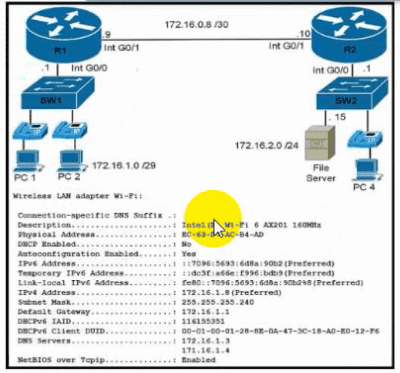
Refer to the exhibit. During initial configuration testing, the Windows workstation PC1 cannot connect with the 172.16.2.0/24 network.
Which set of actions corrects the configuration?
Which key function is provided by the data plane?
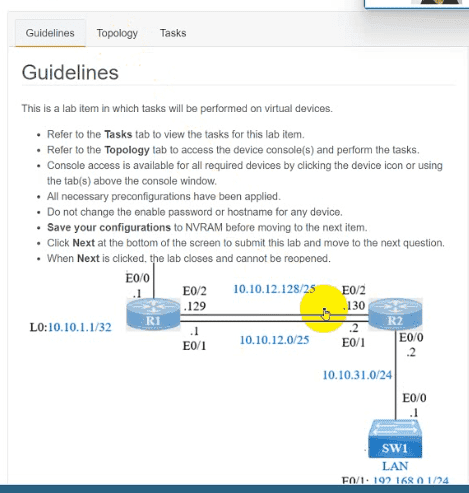
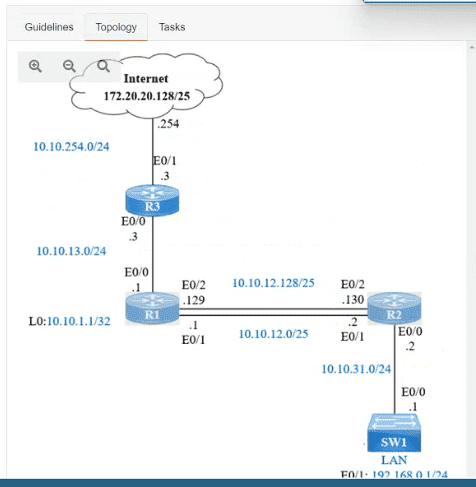
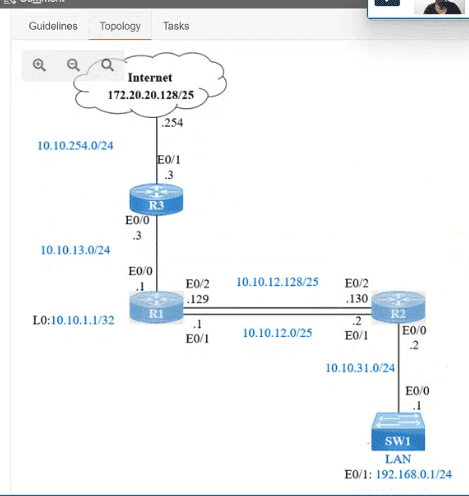
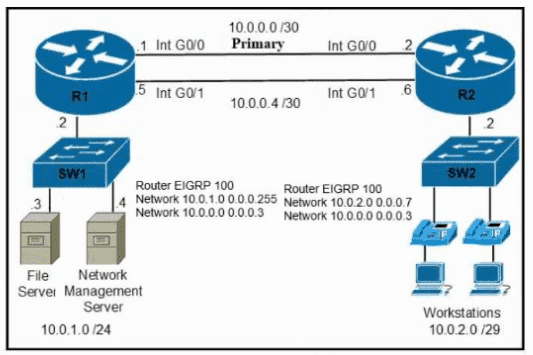
IP connectivity and OSPF are preconfigured on all devices where necessary. Do not make any changes to the IP addressing or OSPF. The company policy uses connected interfaces and next hops when configuring static routes except for load balancing or redundancy without floating static. Connectivity must be established between subnet 172.20.20.128/25 on the Internet and the LAN at 192.168.0.0/24 connected to SW1:
1. Configure reachability to the switch SW1 LAN subnet in router R2.
2. Configure default reachability to the Internet subnet in router R1.
3. Configure a single static route in router R2 to reach to the Internet subnet considering both redundant links between routers R1 and R2. A default route is NOT allowed in router R2.
4. Configure a static route in router R1 toward the switch SW1 LAN subnet where the primary link must be through Ethernet0/1. and the backup link must be through Ethernet0/2 using a floating route. Use the minimal administrative distance value when required.
How does MAC learning function?
Refer to the exhibit.
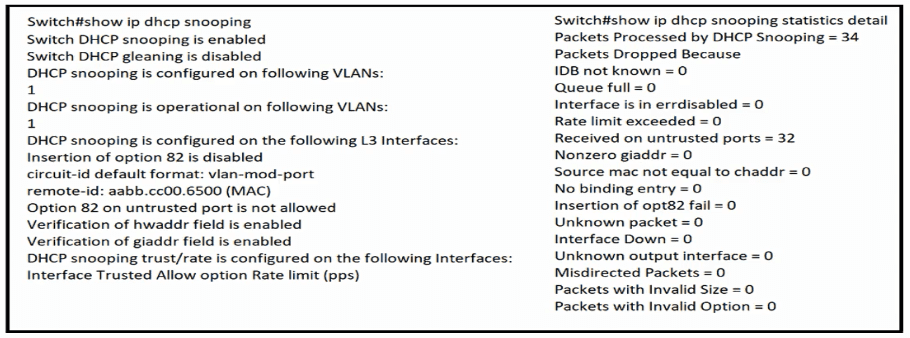
The DHCP server and clients are connected to the same switch. What is the next step to complete the DHCP configuration to allow clients on VLAN 1 to receive addresses from the DHCP server?
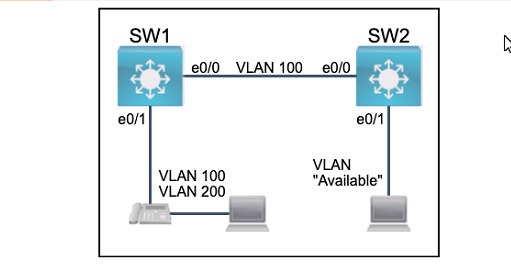
All physical cabling between the two switches is installed. Configure the network connectivity between the switches using the designated VLANs and interfaces.
1. Configure VLAN 100 named Compute and VLAN 200 named Telephony where required for each task.
2. Configure Ethernet0/1 on SW2 to use the existing VLAN named Available.
3. Configure the connection between the switches using access ports.
4. Configure Ethernet0/1 on SW1 using data and voice VLANs.
5. Configure Ethemet0/1 on SW2 so that the Cisco proprietary neighbor discovery protocol is turned off for the designated interface only.
Which statement describes virtualization on containers?
An engineer requires a switch interface to actively attempt to establish a trunk link with a neighbor switch. What command must be configured?
Which feature Is mandatory when configuring a new SSID for a wireless network running WPA3-Personal mode?
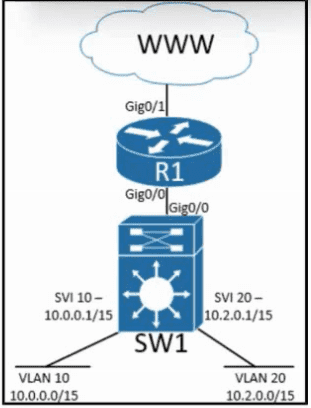
Refer to the exhibit. Inter-VLAN routing is configured on SW1. Client A is running Linux as an OS in VLAN 10 with a default gateway IP 10.0.0.1 but cannot ping client B in VLAN 20 running Windows. What action must be taken to verify that client A has the correct IP settings?
What is the main purpose of SSH management access?
What is a characteristic of an SSID in wireless networks?
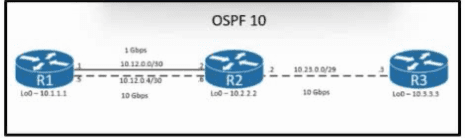
Refer to the exhibit. The loopback IP of R3 has been learned via the two interfaces on R1. R1 is configured with a reference bandwidth of 10 Gbps. Based on the metric calculations, which next hop IP would be used for outgoing routing?
Which default condition must be considered when an encrypted mobility tunnel is used between two Cisco WLCs?
What is a characteristic of a Layer 2 switch?
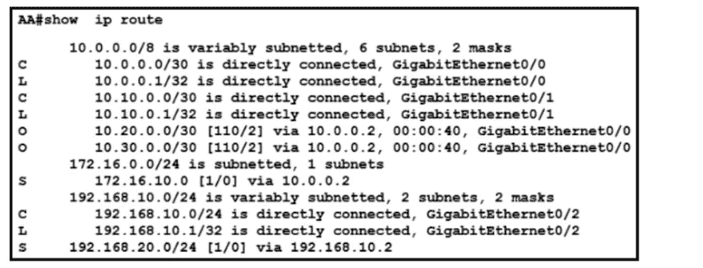
Refer to the exhibit. What is the administrative distance for the advertised prefix that includes the host IP address 192.168.20.1?
What is a characteristic of a Layer 2 switch?
Physical connectivity is implemented between the two Layer 2 switches, and the network connectivity between them must be configured
1. Configure an LACP EtherChannel and number it as 1; configure it between switches SW1 and SVV2 using interfaces Ethernet0/0 and Ethernet0/1 on both sides. The LACP mode must match on both ends
2 Configure the EtherChannel as a trunk link.
3. Configure the trunk link with 802.1 q tags.
4. Configure the native VLAN of the EtherChannel as VLAN 15.
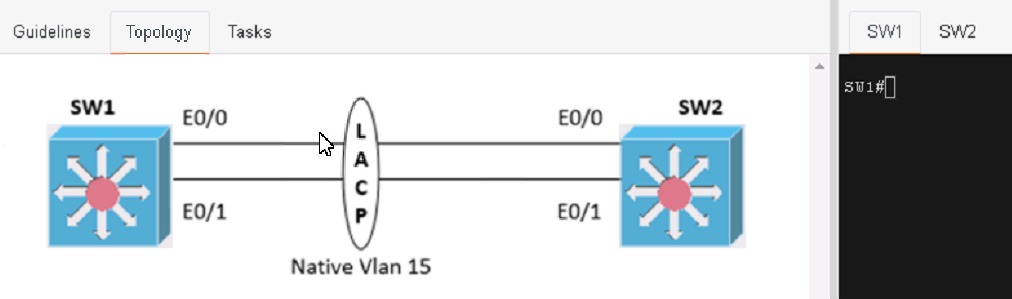
Physical connectivity is implemented between the two Layer 2 switches,
and the network connectivity between them must be configured.
I . Configure an LACP EtherChanneI and number it as 44; configure it
between switches SWI and SW2 using interfaces EthernetO/O and
Ethernet0/1 on both sides. The LACP mode must match on both ends.
2. Configure the EtherChanneI as a trunk link.
3. Configure the trunk link with 802. Iq tags.
4. Configure VLAN 'MONITORING' as the untagged VLAN of the
EtherChannel.
==================
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
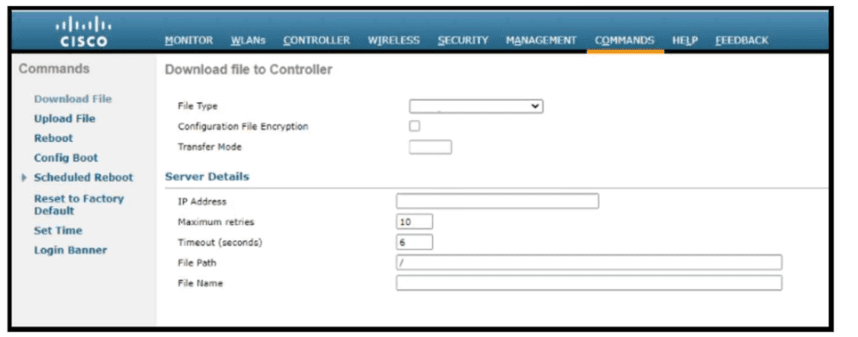
Refer to the exhibit. Which tasks must be performed on the Download File tab to install new software using TCP port 22?)
What facilitates a Telnet connection between devices by entering the device name?
What is the primary purpose of a First Hop Redundancy Protocol?
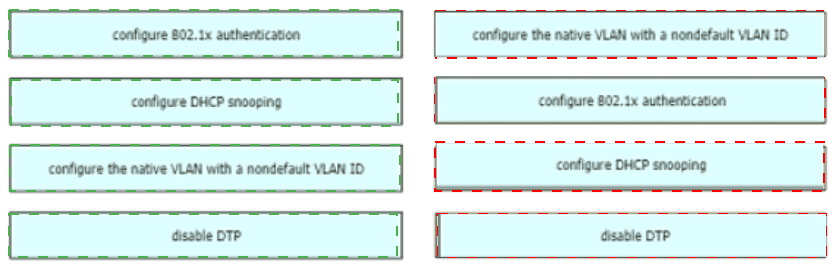
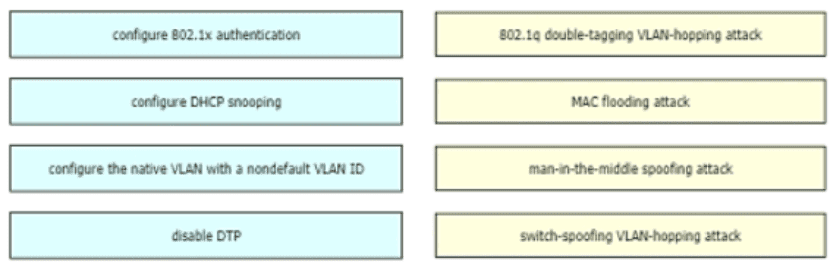
Drag and drop the attack-mitigation techniques from the left onto the Types of attack that they mitigate on the right.
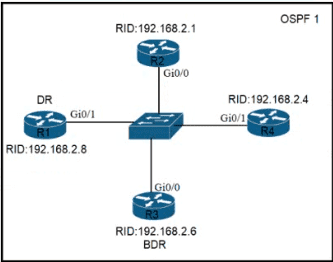
Refer to the exhibit. All routers in the network are configured R2 must be the DR. After the engineer connected the devices, R1 was elected as the DR. Which command sequence must be configure on R2 to Be elected as the DR in the network?