200-301 Cisco Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 200-301 Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is the purpose of using First Hop Redundancy Protocol in a specific subnet?
Refer to the exhibit.
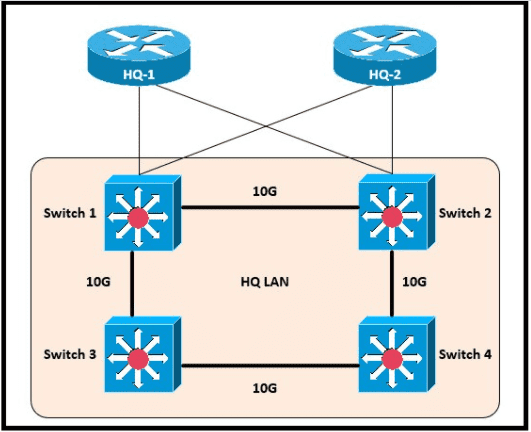
Which switch becomes the root of the spanning tree for VLAN 110?
What mechanism carries multicast traffic between remote sites and supports encryption?
What is a benefit of using a Cisco Wireless LAN Controller?
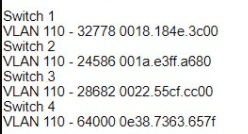
Refer to the exhibit.
A network engineer must configured communication between PC A and the File Server. To prevent interruption for any other communications, which command must be configured?
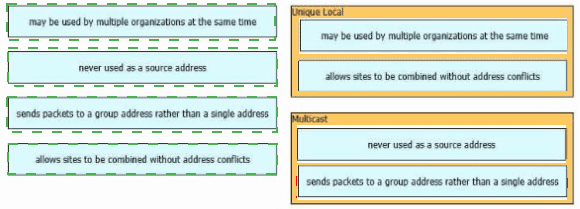
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
What is a similarity between global and unique local IPv6 addresses?
Which technology allows for logical Layer 3 separation on physical network equipment?
What are two behaviors of a point-to-point WAN topology? (Choose two.)
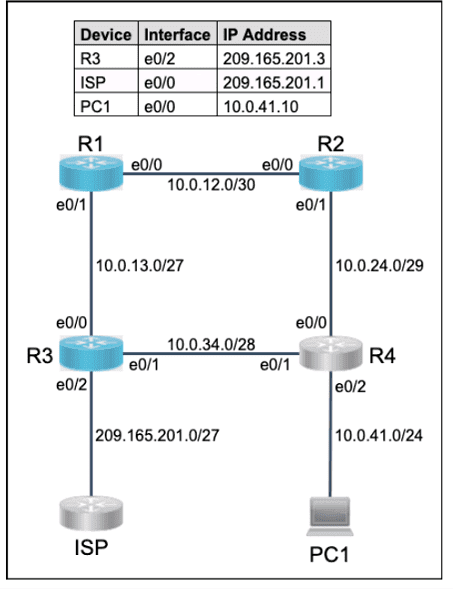
All physical cabling is in place. Router R4 and PCI are fully configured and
inaccessible. R4's WAN interfaces use .4 in the last octet for each subnet.
Configurations should ensure that connectivity is established end-to-end.
1 . Configure static routing to ensure RI prefers the path through R2 to
reach only PCI on R4's LAN
2. Configure static routing that ensures traffic sourced from RI will take
an alternate path through R3 to PCI in the event of an outage along
the primary path
3. Configure default routes on RI and R3 to the Internet using the least number of hops
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Which technology allows multiple operating systems lo run a single physical server?
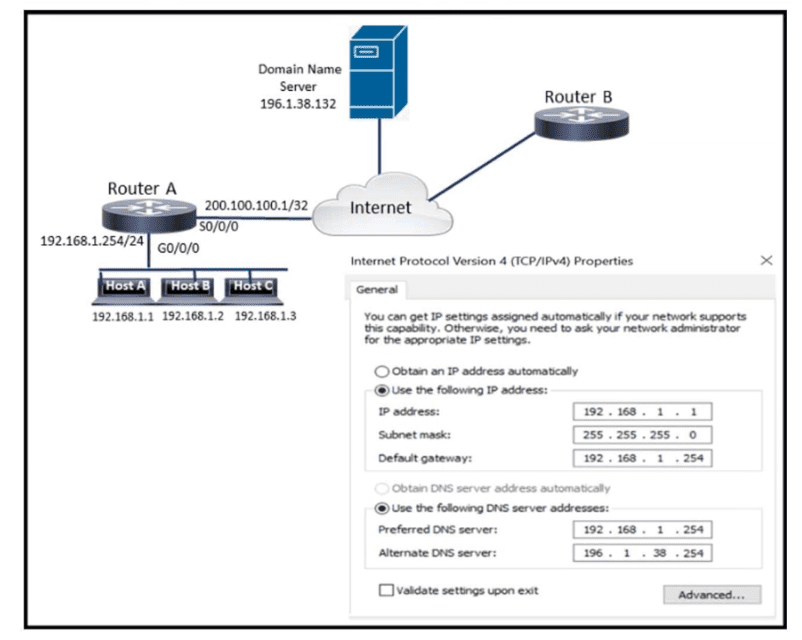
Refer to the exhibit. What is preventing host A from reaching the internet?
An organization developed new security policies and decided to print the policies and distribute them to all personnel so that employees review and apply the policies. Which element of a security program is the organization implementing?
How do TCP and UDP differ in the way they guarantee packet delivery?
Which command on a port enters the forwarding state immediately when a PC is connected to it?
Which implementation provides the strongest encryption combination for the wireless environment?
How does Cisco DNA Center gather data from the network?
What is a characteristic of a SOHO network?
When a floating static route is configured, which action ensures that the backup route is used when the primary route fails?
Which switch port configuration must be configured when connected to an AP running in FlexConnect mode, and the WLANs use flex local switching?
Which device performs stateful inspection of traffic?
Which statement identifies the functionality of virtual machines?
Refer to the exhibit.
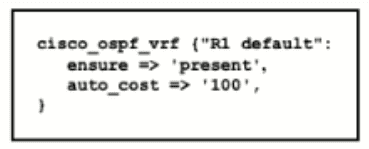
Which type of configuration is represented in the output?
Refer to the exhibit.
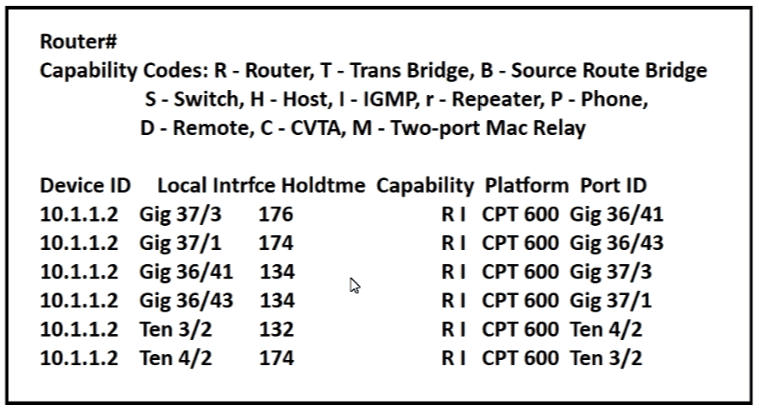
Which command provides this output?
Which two minimum parameters must be configured on an active interface to enable OSPFv2 to operate? (Choose two)
Which feature on the Cisco Wireless LAN Controller when enabled restricts management access from specific networks?
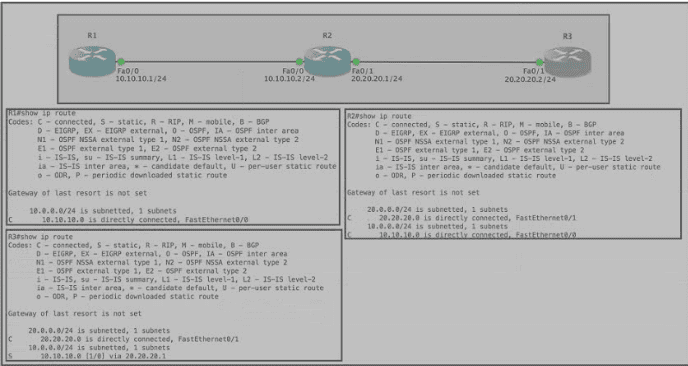
Refer to the exhibit Router R1 Fa0/0 is unable to ping router R3 Fa0'1. Which action must be taken in router R1 to help resolve the configuration issue?
When DHCP is configured on a router, which command must be entered so the default gateway is automatically distributed?
Which level of severity must be set to get informational syslogs?
Where does the configuration reside when a helper address Is configured lo support DHCP?
Which device controls the forwarding of authentication requests for users when connecting to the network using a lightweight access point?
A network administrator must enable DHCP services between two sites. What must be configured for the router to pass DHCPDISCOVER messages on to the server?
What does physical access control regulate?
What is recommended for the wireless infrastructure design of an organization?
Refer to Exhibit.
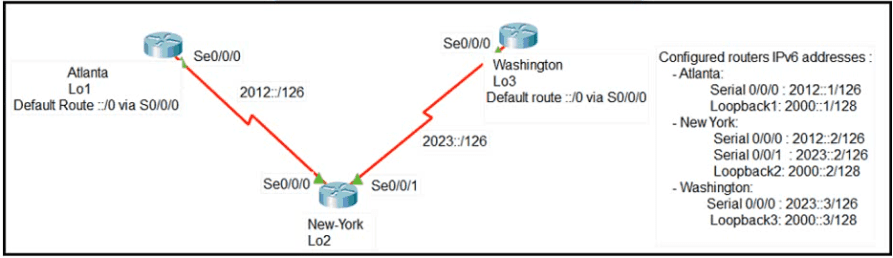
The loopback1 interface of the Atlanta router must reach the loopback3 interface of the Washington router. Which two static host routes must be configured on the NEW York router? (Choose two)
Which fact must the engineer consider when implementing syslog on a new network?
Refer to the exhibit.
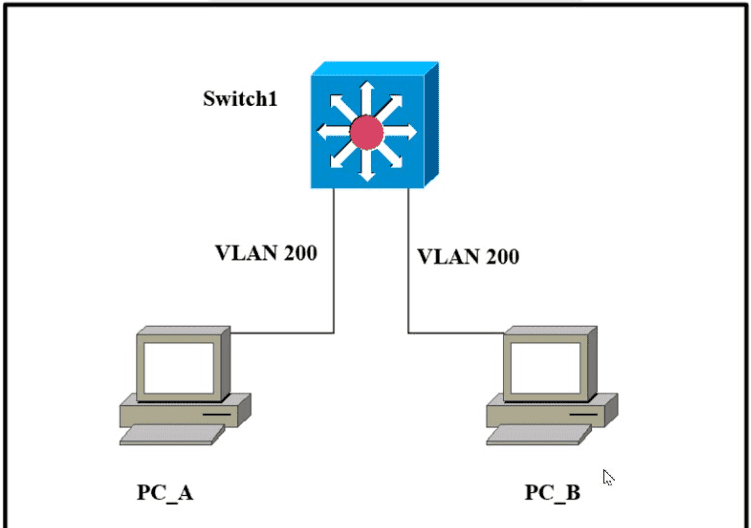
Which outcome is expected when PC_A sends data to PC_B?
Which switch technology establishes a network connection immediately when it is plugged in?
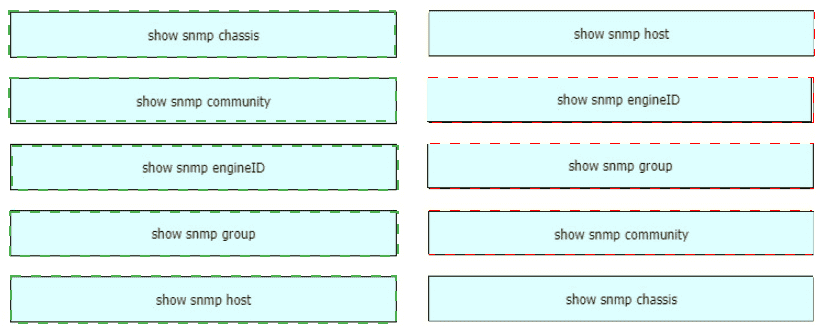
Drag and drop the SNMP manager and agent identifier commands from the left onto the functions on the right
Refer to the Exhibit.
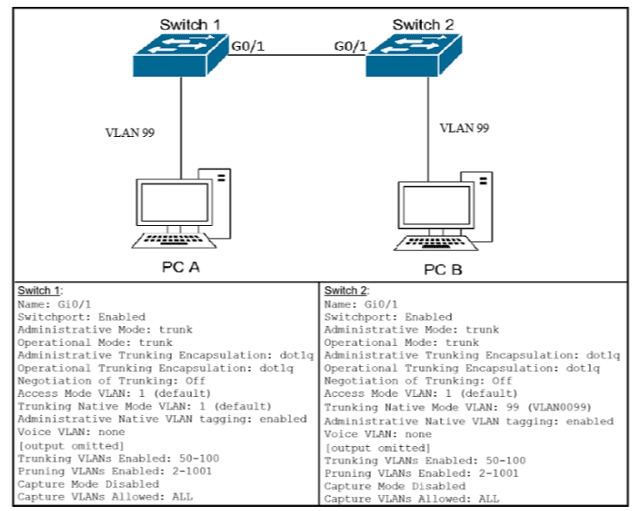
After the switch configuration the ping test fails between PC A and PC B Based on the output for switch 1. which error must be corrected?
Which action does the router take as it forwards a packet through the network?
Two switches are connected and using Cisco Dynamic Trunking Protocol SW1 is set to Dynamic Desirable
What is the result of this configuration?
How are VLAN hopping attacks mitigated?
Which global command encrypt all passwords in the running configuration?
When using Rapid PVST+, which command guarantees the switch is always the root bridge for VLAN 200?
Which spanning-tree enhancement avoids the learning and listening states and immediately places ports in the forwarding state?
Which MAC address is recognized as a VRRP virtual address?
Several new coverage cells are required to improve the Wi-Fi network of an organization. Which two standard designs are recommended? (choose two.)
Which type of information resides on a DHCP server?
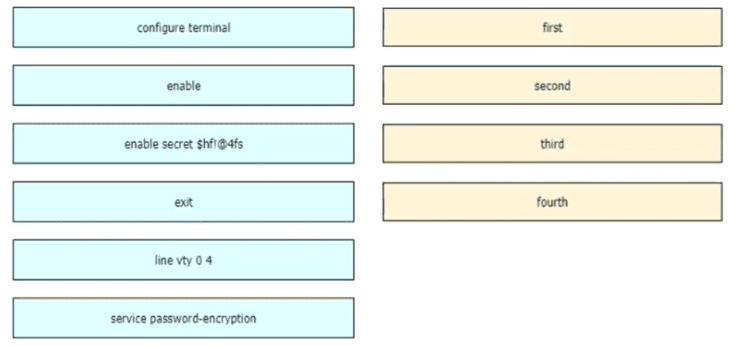
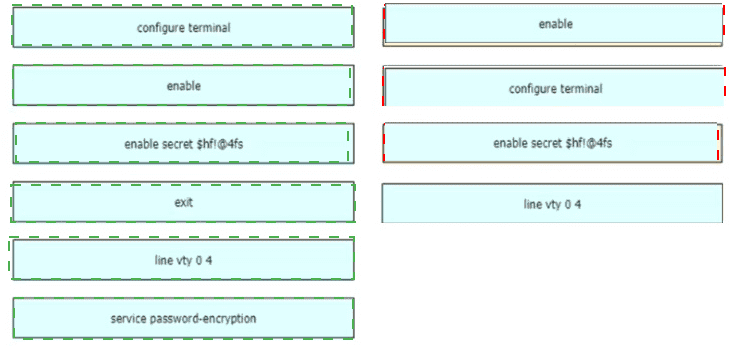
An engineer is configuring an encrypted password for the enable command on a router where the local user database has already been configured Drag and drop the configuration commands from the left into the correct sequence on the right Not all commands are used
What is the default behavior of a Layer 2 switch when a frame with an unknown destination MAC address is received?
What is a benefit of VRRP?
Router R1 must send all traffic without a matching routing-table entry to 192.168.1.1. Which configuration accomplishes this task?
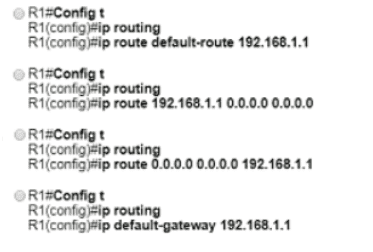
What is a DHCP client?
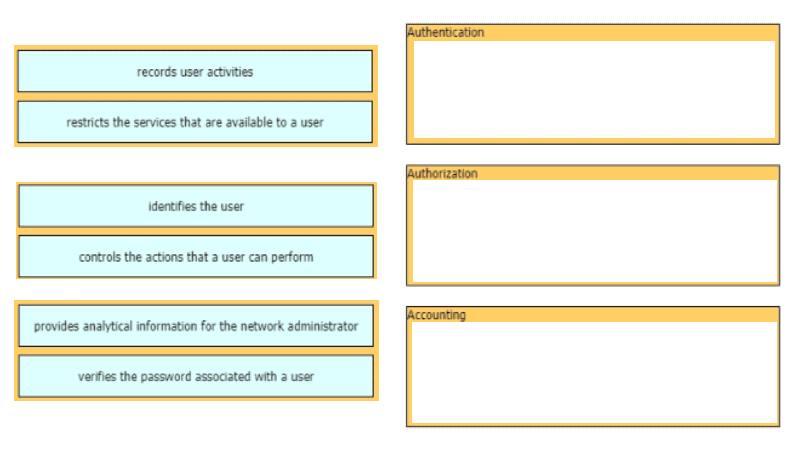
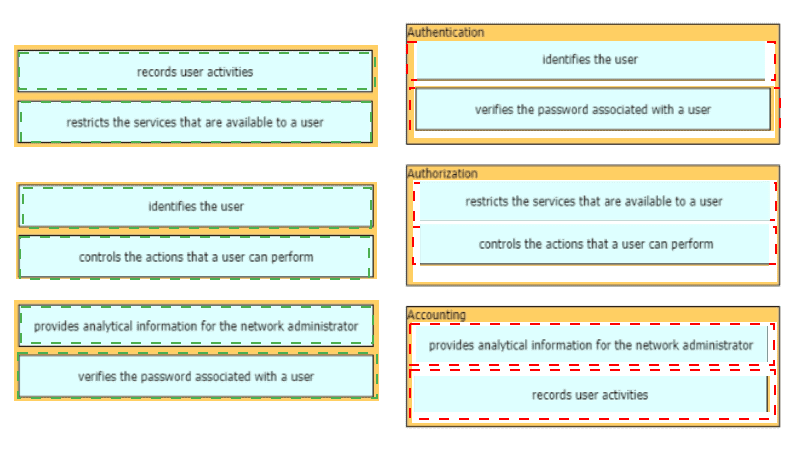
Drag and drop the AAA functions from the left onto the correct AAA services on the right
Refer to the exhibit.
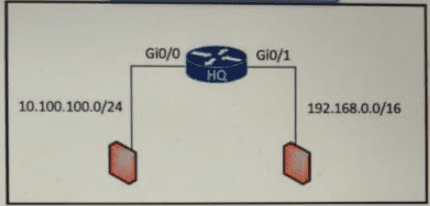
An access list is required to permit traffic from any host on interface G0/0 and deny traffic from interface G/0/1. Which access list must be applied?

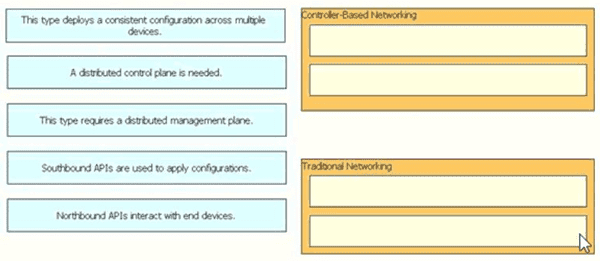
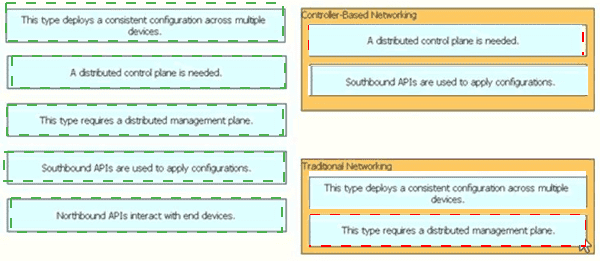
Drag and drop the statement about networking from the left into the Corresponding networking types on the right. Not all statements are used.
In software-defined architecture, which place handles switching for traffic through a Cisco router?
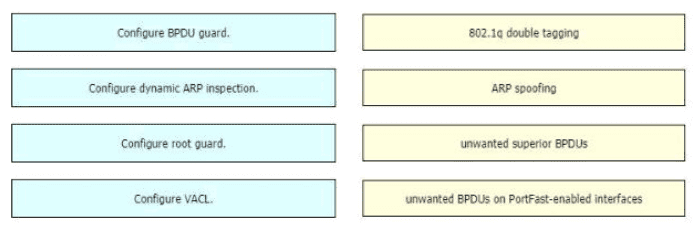
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
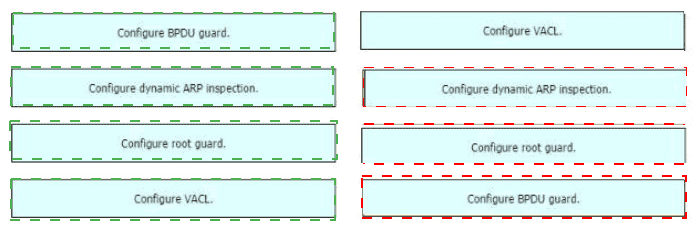
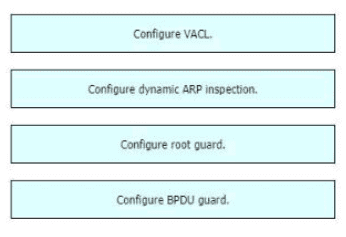
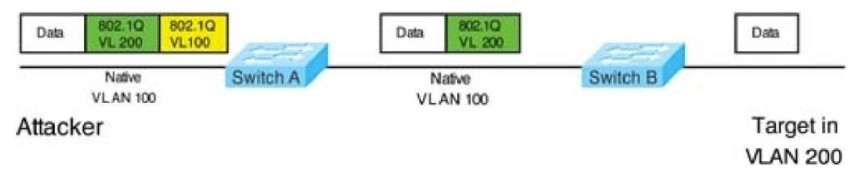 In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).