200-901 Cisco DevNet Associate (DEVASC) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 200-901 DevNet Associate (DEVASC) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
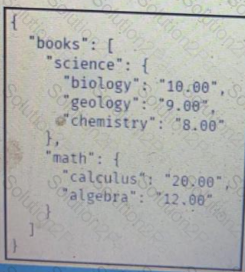
Refer to Exhibit.
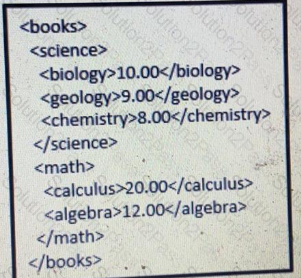
Which JSON is equivalent to the XML-encoded data.
A)

B)
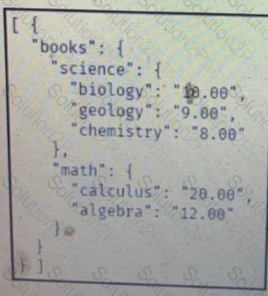
C)
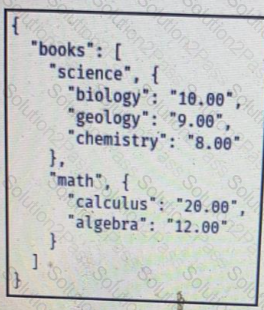
D)
Refer to the exhibit.
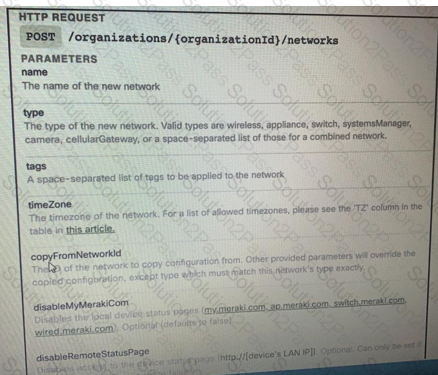
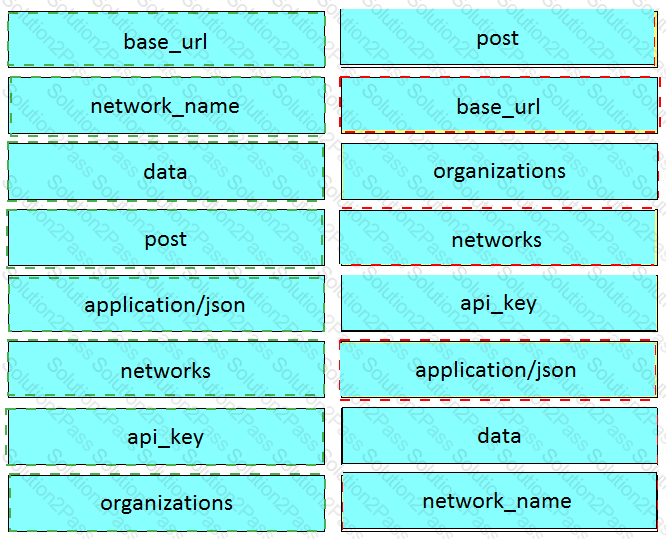
Drag and Drop the code from the bottom onto the box where the code is missing on the Meraki Python script to create a new network
Refer to the exhibit.
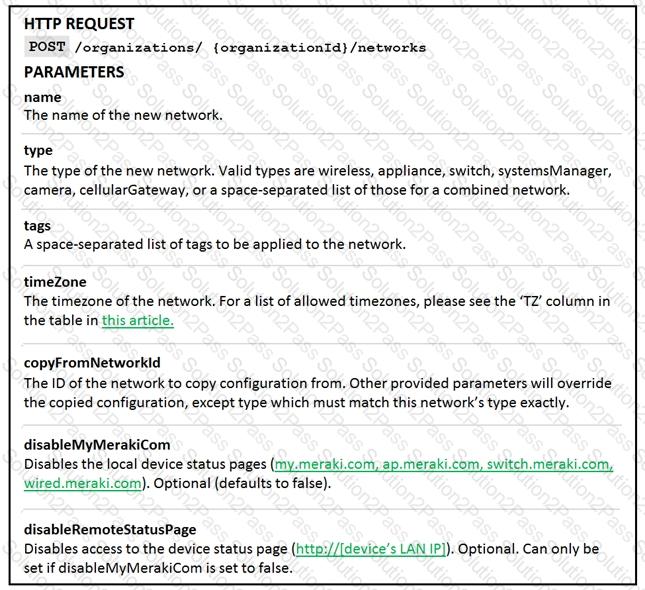
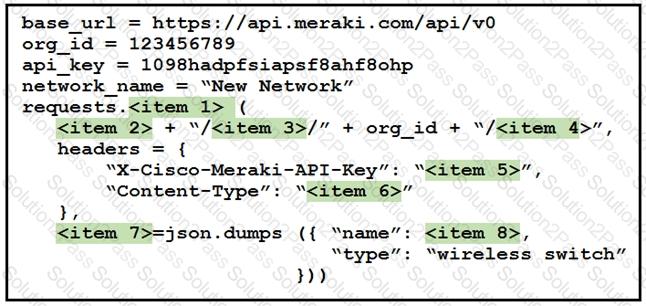
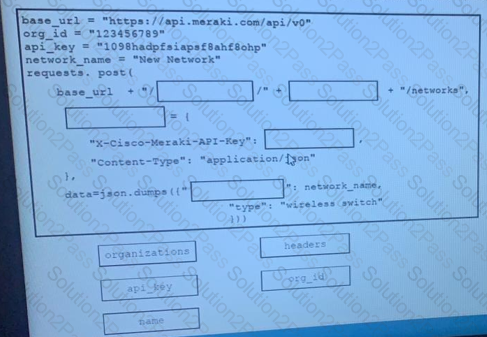
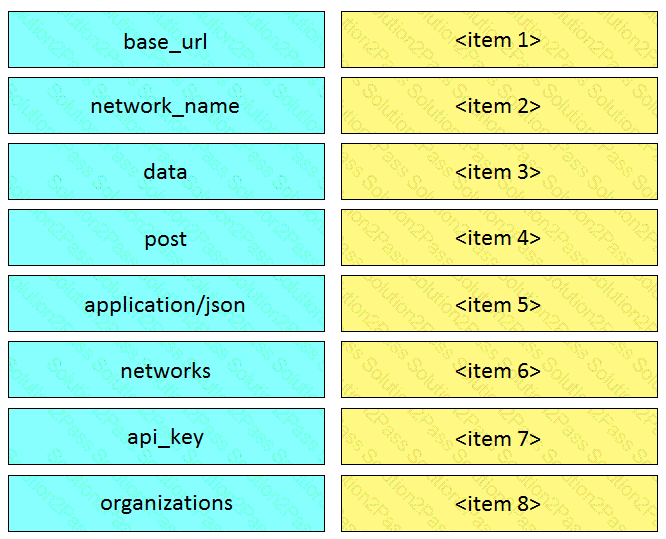
Drag and drop the code from the left onto the item numbers on the right to complete to Meraki python script shown in the exhibit.
How does requesting a synchronous API operation differ from requesting an asynchronous API operation?
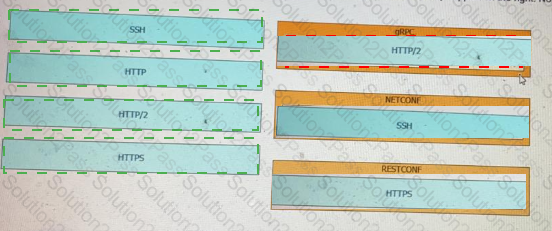
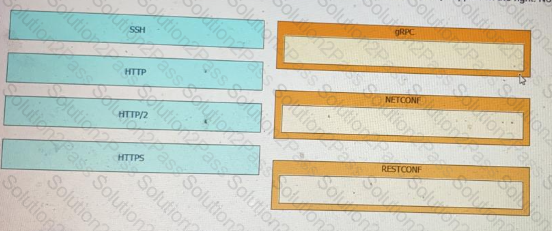
Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right. Not all options are used.
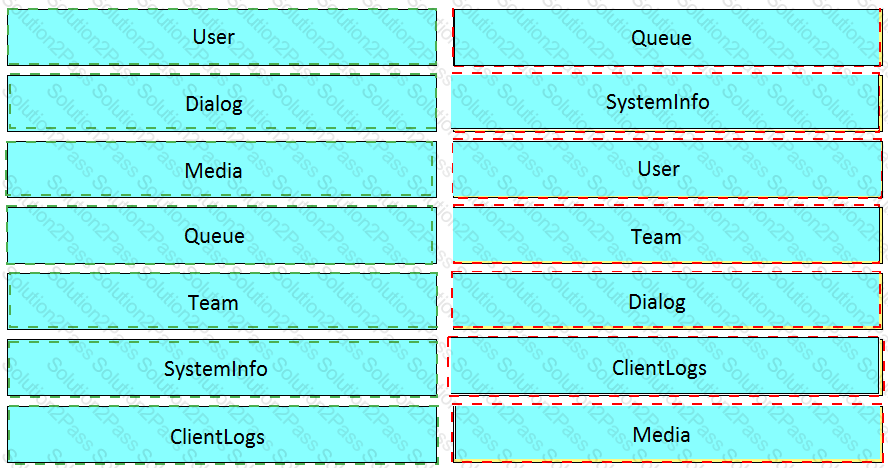
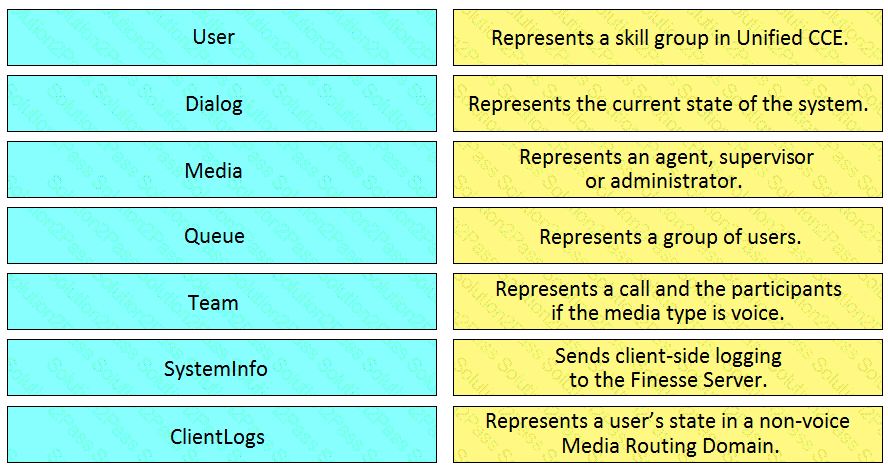
Drag and drop the element of the Finesse API on the left onto the description of its functionally on the right.
Refer to the exhibit.
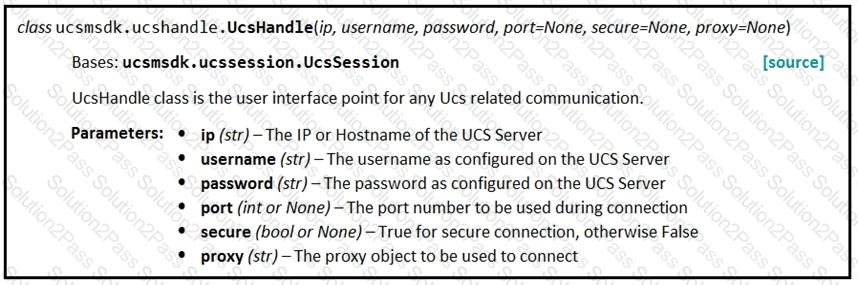
Given the API documentation for the UCS SDK python class, UcsHandle, which code snippet creates a handle instance?
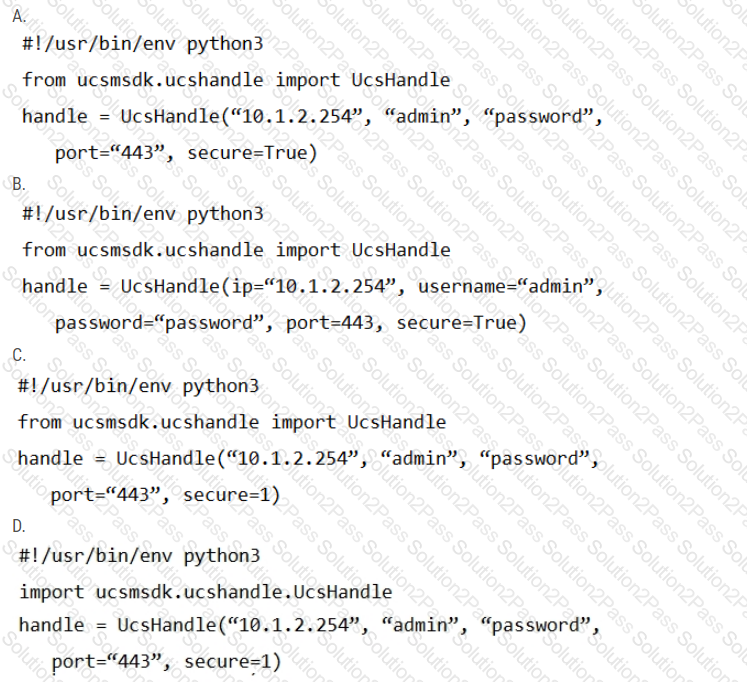
What are two security benefits of a Docker-based application?
Which two encoding formats do YANG interfaces support?
Which product provides network controller-level management features?
What is an example of a network interface hardware address?
On which port does NETCONF operate by default?
A REST API service requires authentication based on the username and password. The user “john” has the password “384279060” and the Base64 encoding of those credentials is “am9objowMTIzNDU2Nzg=”. Which method completes an authentication request?
Before which process is code review performed when version control is used?
Refer to the exhibit.
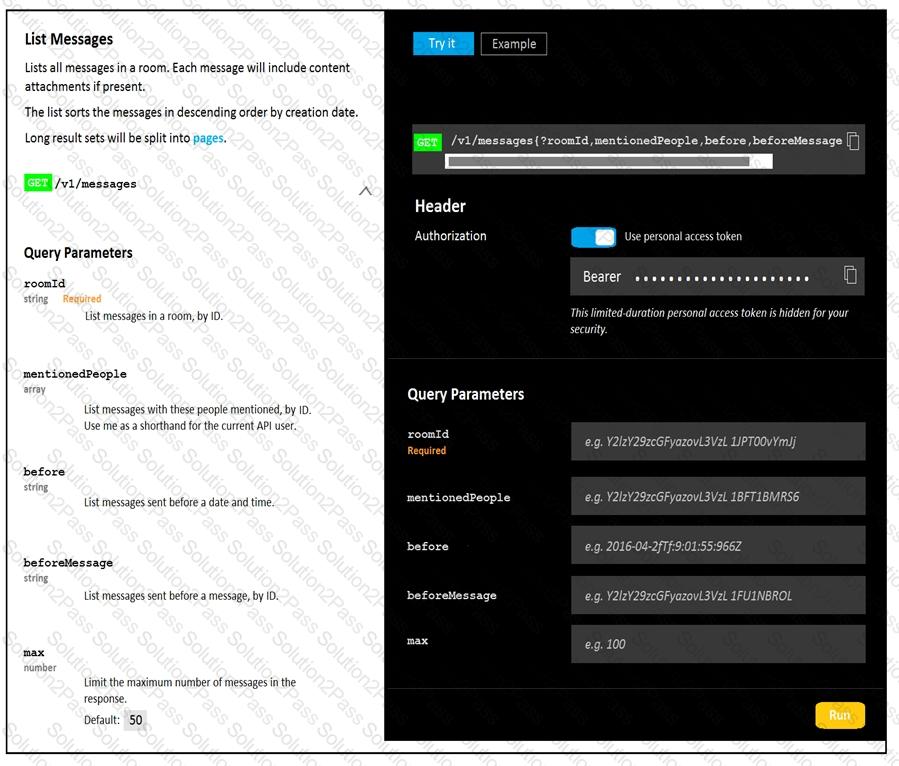
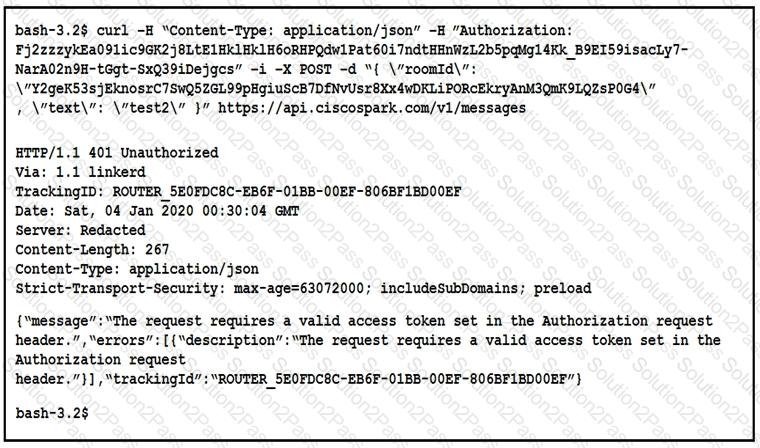
A developer is troubleshooting an API with the given API with the given API documentation and cURL command. What is the cause of this problem?
What is the benefit of edge computing?
What should a CI/CD pipeline aim to achieve?
How is a branch called "my-bug-fix" started to develop a fix needed in a product?
Refer to the exhibit.
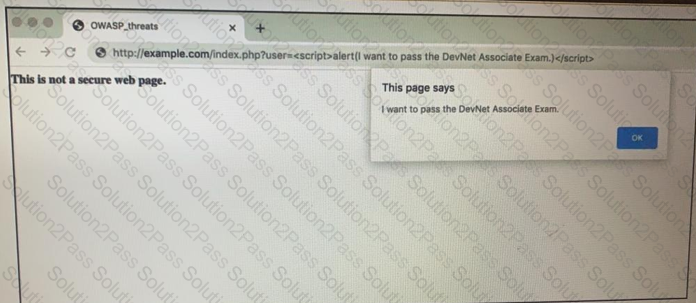
Which OWASP threat does this example demonstrate?
Which two statements describe the advantages of using a version control system? (Choose two.)