300-215 Cisco Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-215 Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit.
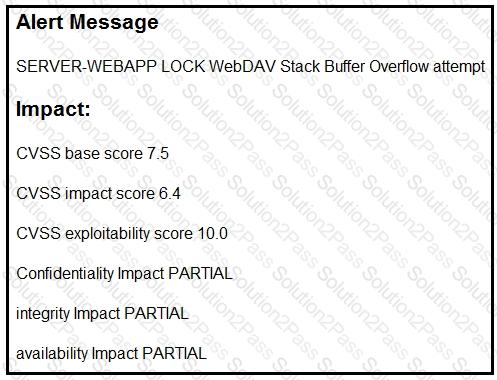
After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business-critical, web-based application and violated its availability. Which two mitigation techniques should the engineer recommend? (Choose two.)
An attacker embedded a macro within a word processing file opened by a user in an organization’s legal department. The attacker used this technique to gain access to confidential financial data. Which two recommendations should a security expert make to mitigate this type of attack? (Choose two.)
An organization fell victim to a ransomware attack that successfully infected 256 hosts within its network. In the aftermath of this incident, the organization's cybersecurity team must prepare a thorough root cause analysis report. This report aims to identify the primary factor or factors that led to the successful ransomware attack and to develop strategies for preventing similar incidents in the future. In this context, what should the cybersecurity engineer include in the root cause analysis report to demonstrate the underlying cause of the incident?
Over the last year, an organization’s HR department has accessed data from its legal department on the last day of each month to create a monthly activity report. An engineer is analyzing suspicious activity alerted by a threat intelligence platform that an authorized user in the HR department has accessed legal data daily for the last week. The engineer pulled the network data from the legal department’s shared folders and discovered above average-size data dumps. Which threat actor is implied from these artifacts?
Which magic byte indicates that an analyzed file is a pdf file?
During a recent incident response investigation, several suspicious network connections originating from a specific host were identified. The host was quickly isolated and the machine was rebuilt During the post mortem, it became clear that there was unpreparedness regarding network artifacts necessitating adjustments to the playbooks to address this data from multiple sources must be correlated. Which two sources should be prioritized for data gathering? (Choose two.)
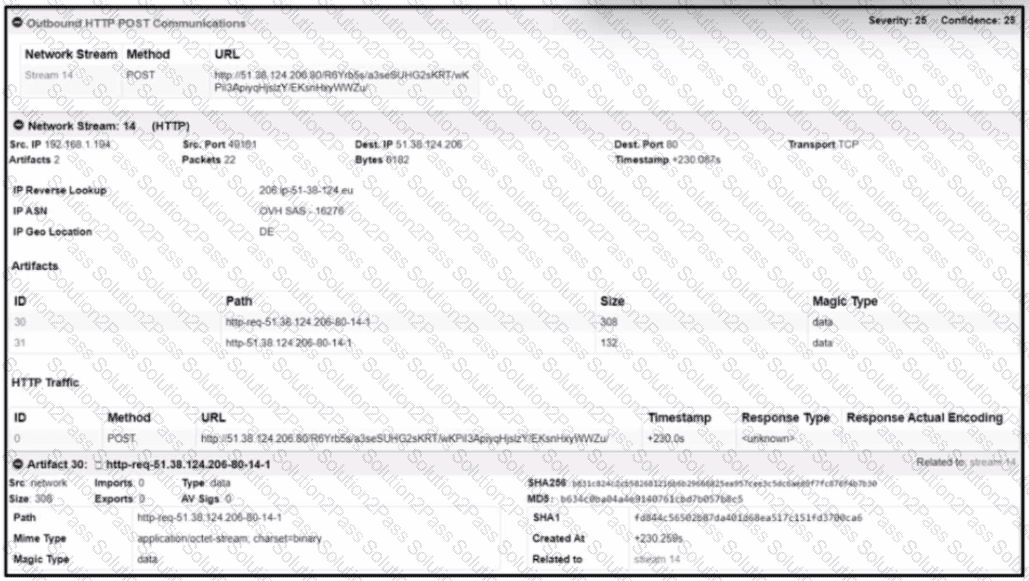
Refer to the exhibit.
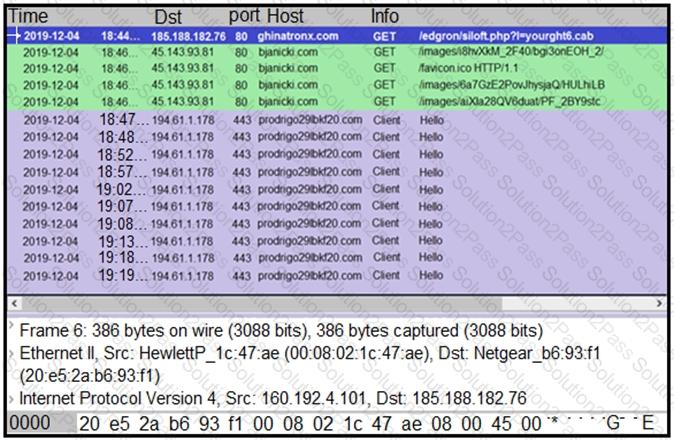
A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the Wireshark traffic logs?
A company had a recent data leak incident. A security engineer investigating the incident discovered that a malicious link was accessed by multiple employees. Further investigation revealed targeted phishing attack attempts on macOS systems, which led to backdoor installations and data compromise. Which two security solutions should a security engineer recommend to mitigate similar attacks in the future? (Choose two.)
The Linux system administrator of a company suspects that physical unauthorized access was granted to a local Linux terminal. The administrator wants to examine the suspected machine for potential unauthorized use and to get information about even/ account in this terminal including when the password last changed The administrator logs in as a root user Which file should be examined to get the information?
An incident response analyst is preparing to scan memory using a YARA rule. How is this task completed?
A workstation uploads encrypted traffic to a known clean domain over TCP port 80. What type of attack is occurring, according to the MITRE ATT&CK matrix?
A threat actor has successfully attacked an organization and gained access to confidential files on a laptop. What plan should the organization initiate to contain the attack and prevent it from spreading to other network devices?
A security team is notified from a Cisco ESA solution that an employee received an advertising email with an attached .pdf extension file. The employee opened the attachment, which appeared to be an empty document. The security analyst cannot identify clear signs of compromise but reviews running processes and determines that PowerShell.exe was spawned by CMD.exe with a grandparent AcroRd32.exe process. Which two actions should be taken to resolve this issue? (Choose two.)
What can the blue team achieve by using Hex Fiend against a piece of malware?
Refer to the exhibit.

The application x-dosexec with hash 691c65e4fb1d19f82465df1d34ad51aaeceba14a78167262dc7b2840a6a6aa87 is reported as malicious and labeled as "Trojan.Generic" by the threat intelligence tool. What is considered an indicator of compromise?
What is the steganography anti-forensics technique?
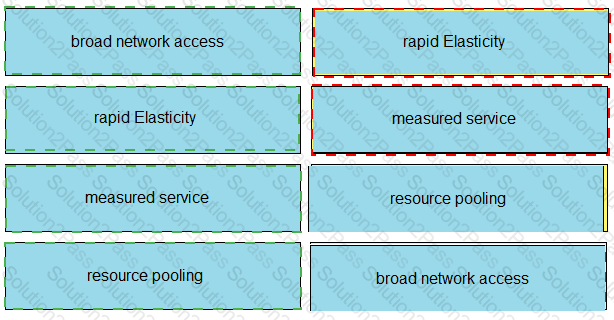
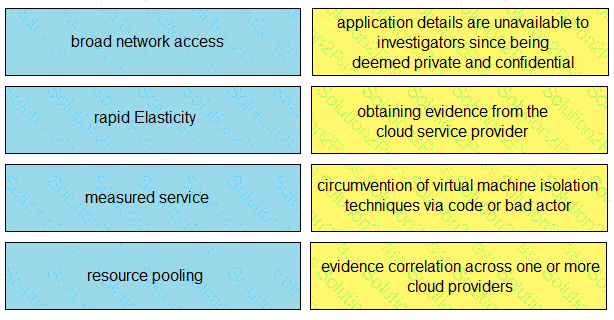
Drag and drop the cloud characteristic from the left onto the challenges presented for gathering evidence on the right.
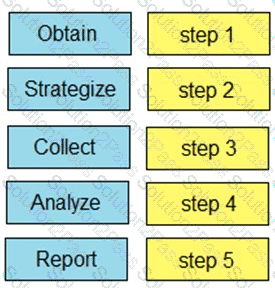
Drag and drop the steps from the left into the order to perform forensics analysis of infrastructure networks on the right.