300-215 Cisco Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-215 Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which technique exemplifies an antiforensic technique?
Refer to the exhibit.

Which encoding method is used to obfuscate the script?
During a routine security audit, an organization's security team detects an unusual spike in network traffic originating from one of their internal servers. Upon further investigation, the team discovered that the server was communicating with an external IP address known for hosting malicious content. The security team suspects that the server may have been compromised. As the incident response process begins, which two actions should be taken during the initial assessment phase of this incident? (Choose two.)
Refer to the exhibit.
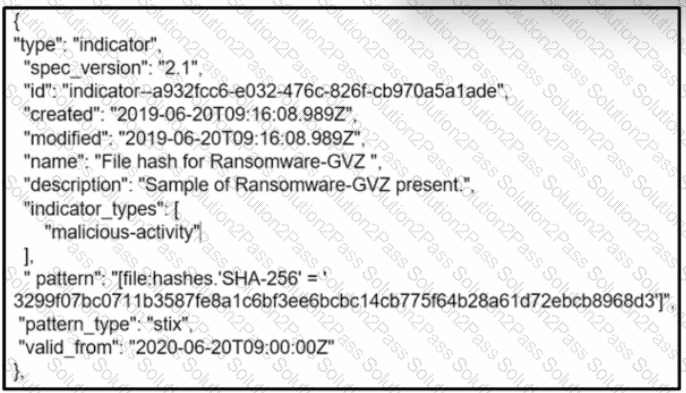
What is the indicator of compromise?
An organization experienced a ransomware attack that resulted in the successful infection of their workstations within their network. As part of the incident response process, the organization's cybersecurity team must prepare a comprehensive root cause analysis report. This report aims to identify the primary factor or factors responsible for the successful ransomware attack and to formulate effective strategies to prevent similar incidents in the future. In this context, what should the cybersecurity engineer emphasize in the root cause analysis report to demonstrate the underlying cause of the incident?
A cybersecurity analyst is analyzing a complex set of threat intelligence data from internal and external sources. Among the data, they discover a series of indicators, including patterns of unusual network traffic, a sudden increase in failed login attempts, and multiple instances of suspicious file access on the company's internal servers. Additionally, an external threat feed highlights that threat actors are actively targeting organizations in the same industry using ransomware. Which action should the analyst recommend?
Refer to the exhibit.
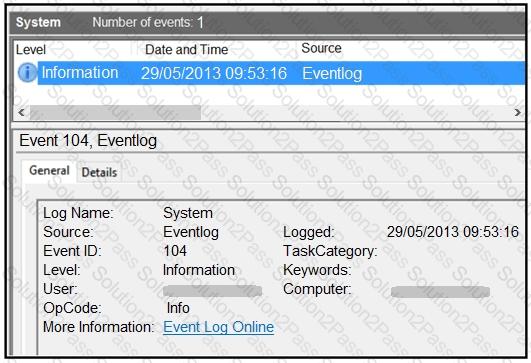
An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?
A cybersecurity analyst detects fileless malware activity on secure endpoints. What should be done next?
An engineer is analyzing a ticket for an unexpected server shutdown and discovers that the web-server ran out of useable memory and crashed.
Which data is needed for further investigation?
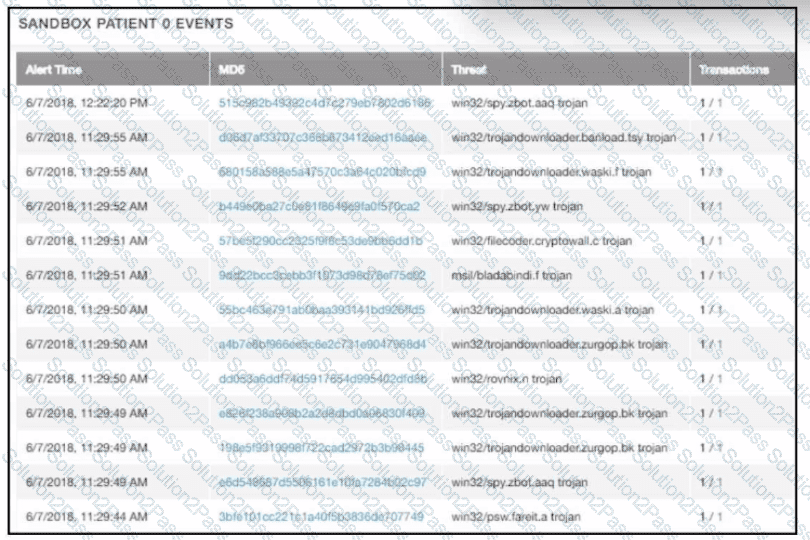
multiple machines behave abnormally. A sandbox analysis reveals malware. What must the administrator determine next?
What are two features of Cisco Secure Endpoint? (Choose two.)
A malware outbreak revealed that a firewall was misconfigured, allowing external access to the SharePoint server. What should the security team do next?
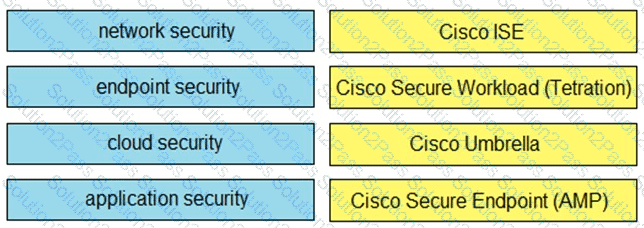
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
A security team receives reports of multiple files causing suspicious activity on users’ workstations. The file attempted to access highly confidential information in a centralized file server. Which two actions should be taken by a security analyst to evaluate the file in a sandbox? (Choose two.)
Refer to the exhibit.

What is occurring?
Refer to the exhibit.
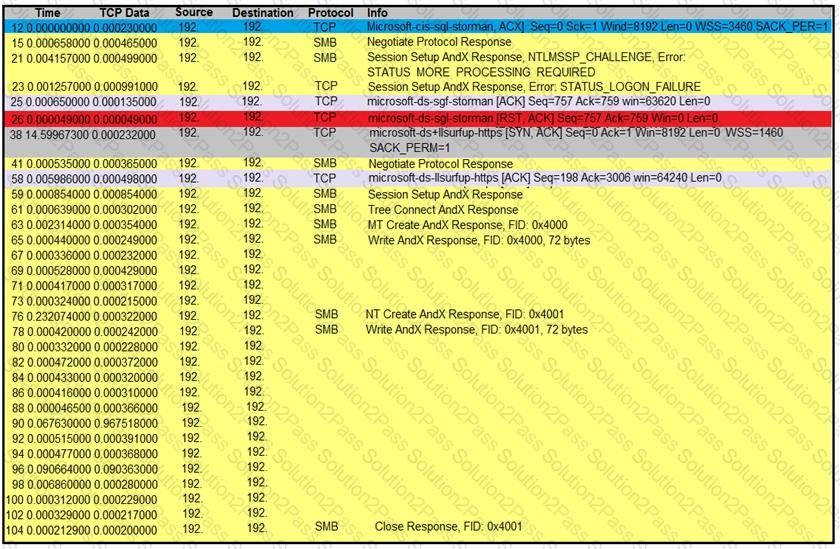
An engineer is analyzing a TCP stream in Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?
Refer to the exhibit.

A security analyst is reviewing alerts from the SIEM system that was just implemented and notices a possible indication of an attack because the SSHD system just went live and there should be nobody using it. Which action should the analyst take to respond to the alert?
An incident responder reviews a log entry that shows a Microsoft Word process initiating an outbound network connection followed by PowerShell execution with obfuscated commands. Considering the machine's role in a sensitive data department, what is the most critical action for the responder to take next to analyze this output for potential indicators of compromise?
An “unknown error code” is appearing on an ESXi host during authentication. An engineer checks the authentication logs but is unable to identify the issue. Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?
A cybersecurity analyst must evaluate files from an endpoint in an enterprise network. The antivirus software on the endpoint flagged a suspicious file during a routine scan On initial evaluation the file did not match any known signatures in the antivirus database, but exhibited unusual network behavior during dynamic analysis Which step should the analyst take next?

