300-620 Cisco Implementing Cisco Application Centric Infrastructure (300-620 DCACI) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 300-620 Implementing Cisco Application Centric Infrastructure (300-620 DCACI) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A Solutions Architect is asked to design two data centers based on Cisco ACI technology that can extend L2/ L3, VXLAN, and network policy across locations. ACI Multi-Pod has been selected. Which two requirements must be considered in this design? (Choose two.)
Engineer resolves an underlying condition of a fault but notices that the fault was not deleted from the Faults view. Which two actions must be taken to remove the fault? (Choose two.)
Refer to the exhibit.
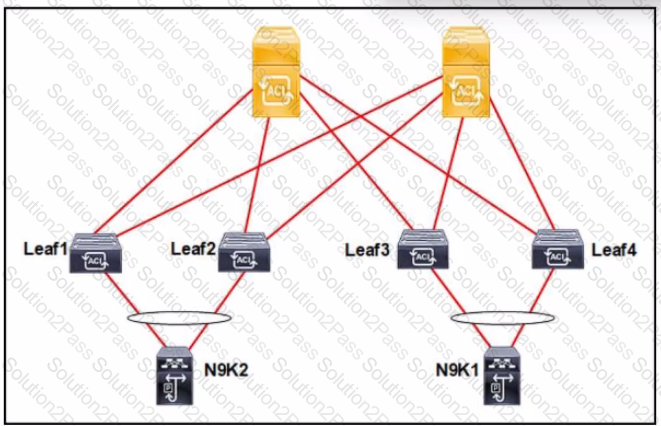
The Cisco ACI fabric is built with L20ut to the N9K1 and N9K2 switches. The switches run the RSTP protocol. The requirement is for the Cisco ACI fabric to detect 5 from the N9K and for the fabric to be protected against loops. Which set of actions must be taken to meet the requirements?
Which feature allows firewall ACLs to be configured automatically when new endpoints are attached to an EPG?
Which Cisco ACI setting corresponds to the VMware MAC pinning?
An organization has encountered many STP-related issues in the past due to failed hardware components. They are in the process of long-term migration to a newly deployed ACI fabric. Senior engineers are worried that spanning-tree loops in the existing network may be extended to the ACI fabric. Which feature must be enabled on the ACI leaf ports to protect the fabric from spanning-tree loops?
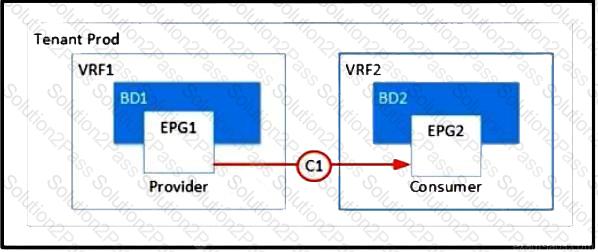
Refer to the exhibit. Which two configurations enable inter-VRF communication? (Choose two.)
An engineer configures port-12 on Leaf-101 and Leaf-102 to connect to a new server, SVR-12. The new server will belong to EPG-12 and use encap VLAN-1212. The engineer configured SVR-12 as a VPC member port and statically bound the VPC member port to EPG-12. Which additional step must the engineer take to configure connectivity?
In the context of ACI Multi-Site, when is the information of an endpoint (MAC/IP) that belongs to site 1 advertised to site 2 using the EVPN control plane?
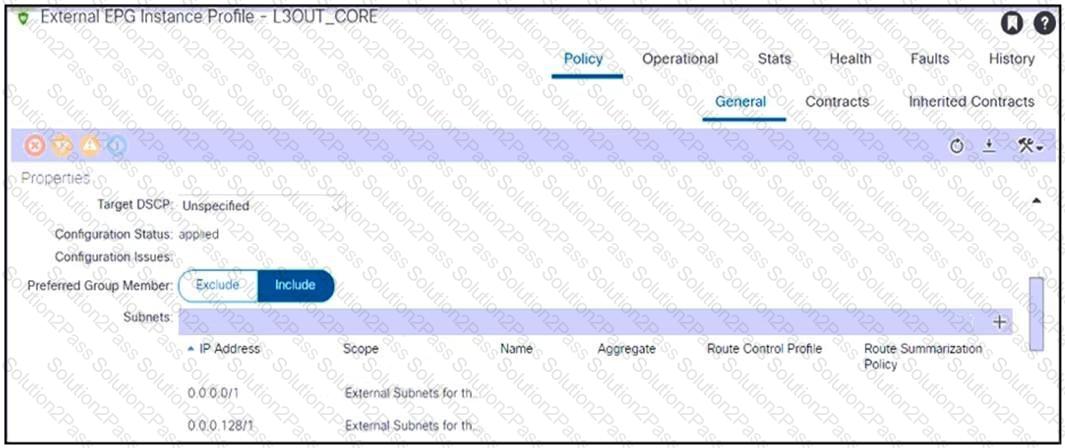
Refer to the exhibit. An engineer configured subnets on the external EPG called L3OUT_CORE. The external endpoints in the 10.1.0.0/24 subnet can reach internal endpoints, but the external endpoints in the 172.16.1.0/24 subnet are unreachable. Which set of actions enables the connectivity?
A network engineer must allow secure access to the Cisco ACl out-of-band (OOB) management only from external subnets 10 0 0024 and 192.168 20 G'25. Which configuration set accomplishes this goal?
Which statement about ACI syslog is true or Which statement describes the ACI syslog?
Network engineer configured a Cisco ACI fabric as follows:
• An EPG called EPG-A is created and associated with a VMM domain called North. •The EPG-A is associated with BD-A and is in an application profile called Apps-A.
• The BD-A is associated with VRF-1 in the Prod tenant.
Which port group must be selected to place VMs in EPG-A?
An engineer must add a group of 70 bare-metal ESXi servers to the Cisco ACI fabric, which is integrated with vCenter. These configuration steps are complete:
The configured pool of ESXi hosts is configured with an Attachable Access Entity Profile (AAEP) called AEP_VMM.
The new group uses the AAEP called AEP_BAREMETAL.
Which action extends functional VMM integration to the new nodes?
An engineer is implementing Cisco ACI at a large platform-as-a-service provider using APIC controllers, 9396PX leaf switches, and 9336PQ spine switches. The leaf switch ports are configured as IEEE 802.1p ports. Where does the traffic exit from the EPG in IEEE 802.1p mode in this configuration?
Refer to the exhibit.
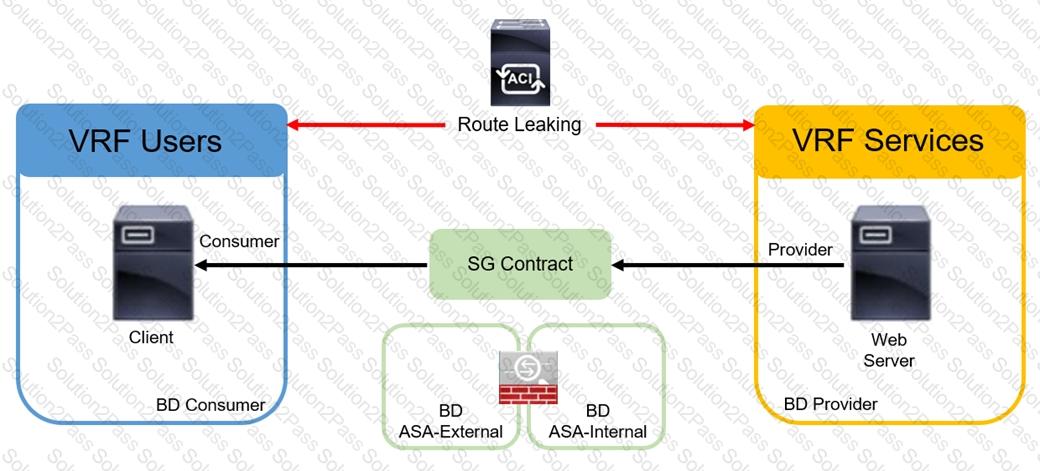
An engineer must implement the inter-tenant service graph. Which set of actions must be taken to accomplish this goal?
A customer creates Layer 3 connectivity to the outside network. However, only border leaf switches start receiving destination updates to other networks from the newly created L3Out. The updates must also be propagated to other Cisco ACI leaf switches. The L3Out is linked with the EPGs via a contract. Which action must be taken in the pod policy group to accomplish this goal?
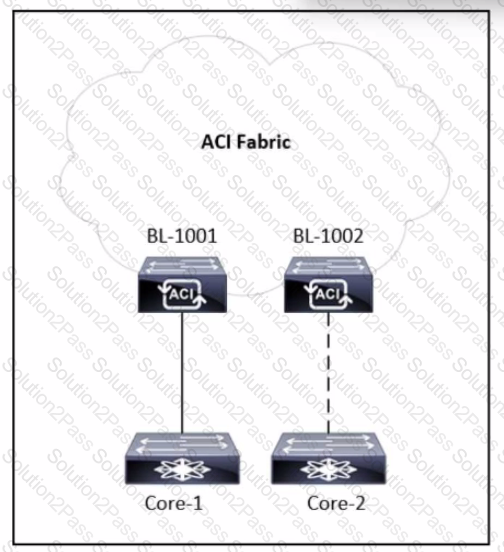
Refer to the exhibit. A tenant is configured with a single L30ut and a single-homed link to the core router called Core-1. An engineer must add a second link to the L30ut that connects to Core-2 router. Which action allows the traffic from Core-2 to BL-1002 to have the same connectivity as the traffic from Core-1 to BL-1001?
An engineer must create a backup of the Cisco ACI fabric for disaster recovery purposes. The backup must be transferred over a secure and encrypted transport. The backup file must contain all user and password related information. The engineer also wants to process and confirm the backup file validity by using a Python script. This requires the data structure to have a format similar to a Python dictionary. Which configuration set must be used to meet these requirements?
Refer to the exhibit.
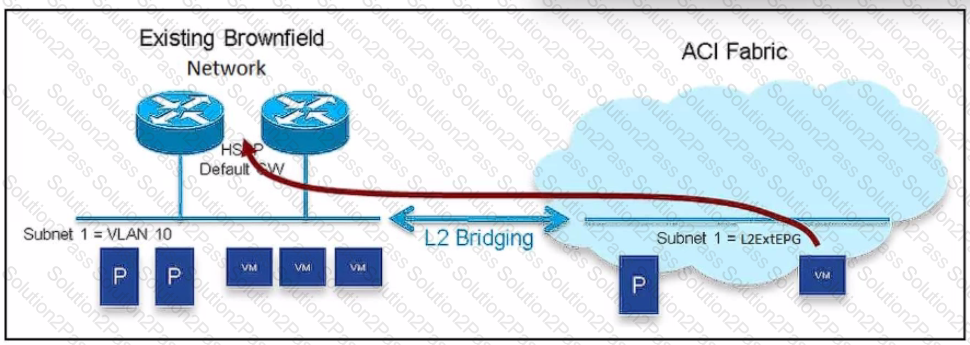
An engineer must migrate workloads from the brownfield network to the Cisco ACI fabric. The VLAN 10 default gateway remains in the router located in the brownfield Network. The bridge domain has already been associated with L20ut. Which two actions must be taken to migrate the workloads? (Choose two.)
