300-620 Cisco Implementing Cisco Application Centric Infrastructure (300-620 DCACI) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 300-620 Implementing Cisco Application Centric Infrastructure (300-620 DCACI) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An engineer needs to avoid loops in the ACI network and needs an ACI leaf switch to error-disable an interface if the interface receives an ACI-generated packet. Which action meets these requirements?
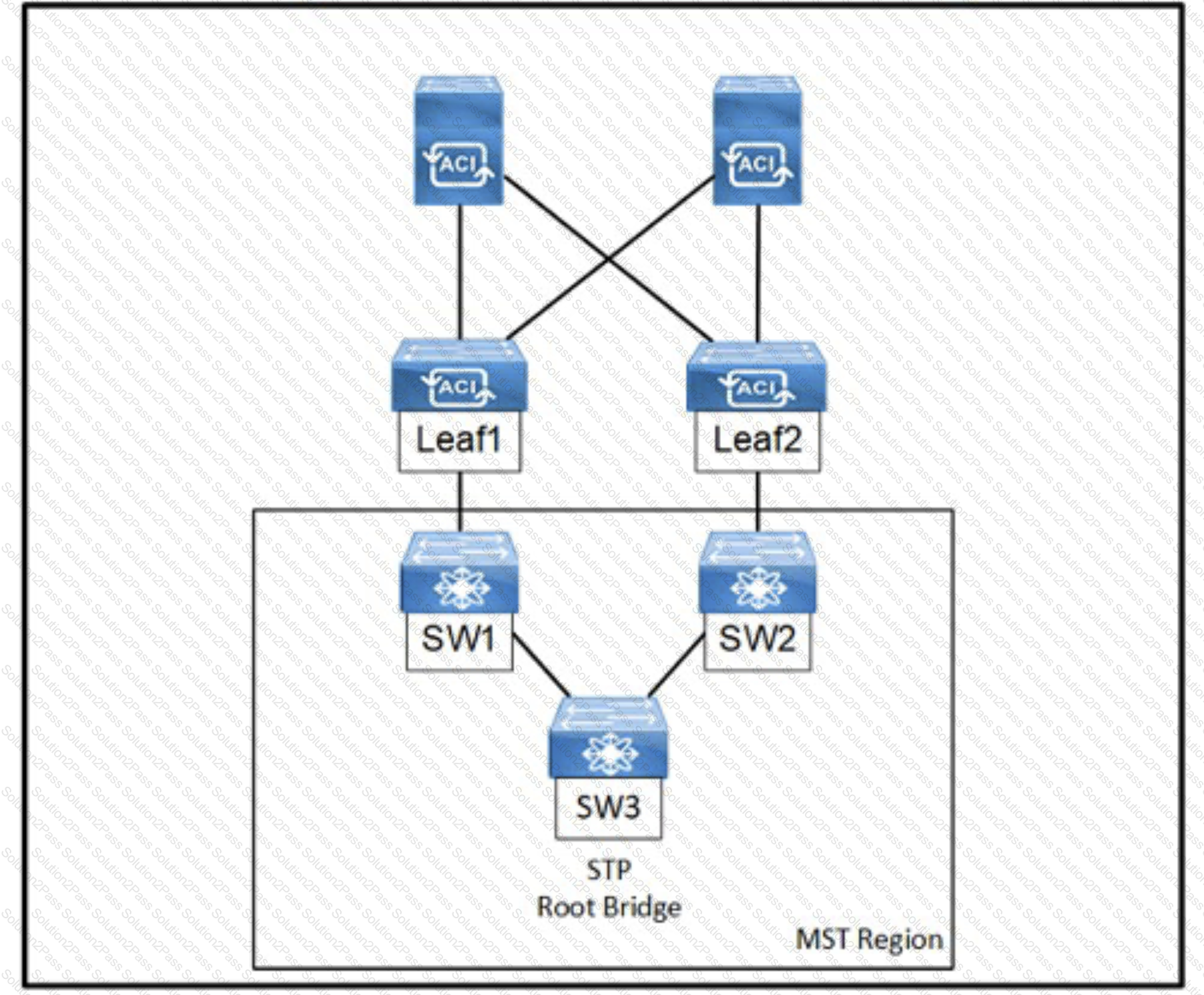
Refer to the exhibit, An engineer is deploying a Cisco ACI environment but experiences a STP loop between switch1 and switch2. Which configuration step is needed to break the STP loop?
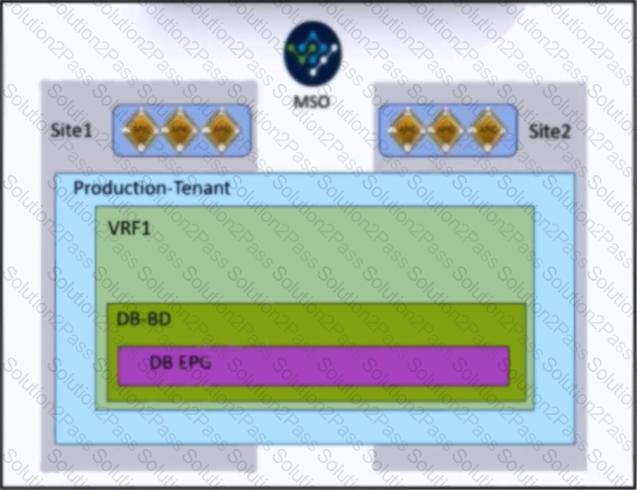
Refer to the exhibit. An engineer must allow IP mobility between Site1 and Site2 in a Cisco ACI Multi-Site orchestrator. The design must meet these requirements:
A disaster recovery (DR) solution must exist between the sites that do not require vMotion support.
The application must be started at a DR site without having to re-IP the application servers.
The solution must avoid any broadcast storms between the sites.
Which two actions meet these criteria? (Choose two.)
Refer to the exhibit.
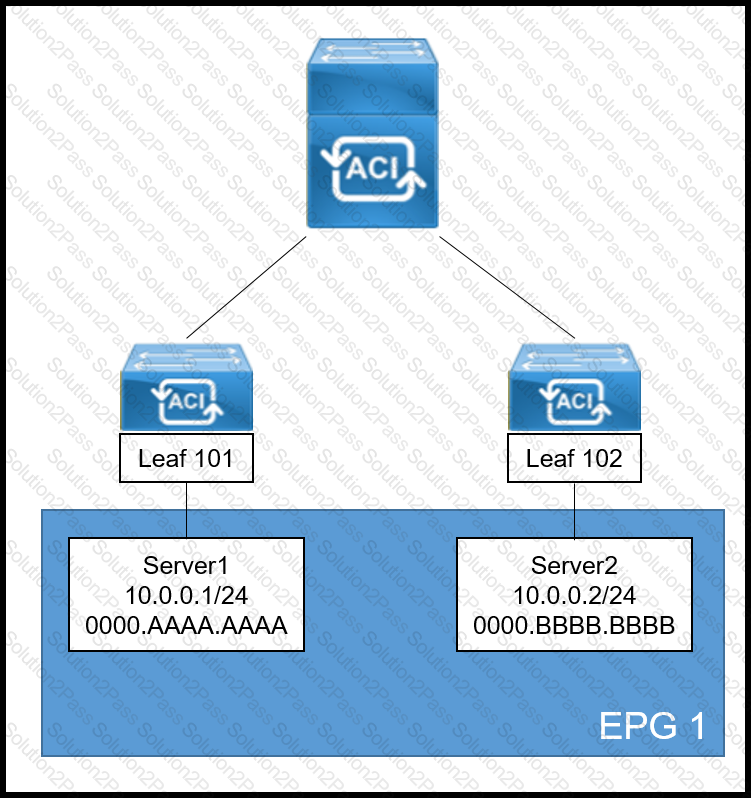
A systems engineer is implementing the Cisco ACI fabric. However, the Server2 information is missing from the Leaf 101 endpoint table and the COOP database of the spine. The requirement is for the bridge domain configuration to enforce the ACI fabric to forward the unicast packets generated by Server1 destined to Server2. Which action must be taken to meet these requirements?
Refer to the exhibit.
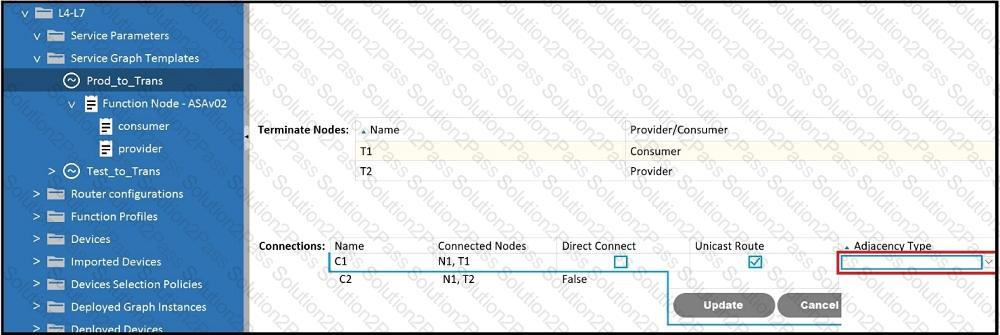
Which Adjacency Type value should be set when the client endpoint and the service node
interface are in a different subnet?
An engineer must attach an ESXi host to the Cisco ACI fabric. The host is connected to Leaf 1 and has its gateway IP address 10.10.10.254/24 configured inside the ACI fabric. A new wall is attached to Leaf 2 and mapped to the same EPG and BD as the ESXi host. The engineer must migrate the gateway of the ESXi host to the firewall. Which configuration set complishes this goal?
An engineer must configure a Layer 3 connection to the WAN router. The hosts in production VRF must access WAN subnets. The engineer associates EPGs in the production VRF with the external routed domain. Which action completes the task?
Refer to the exhibit.
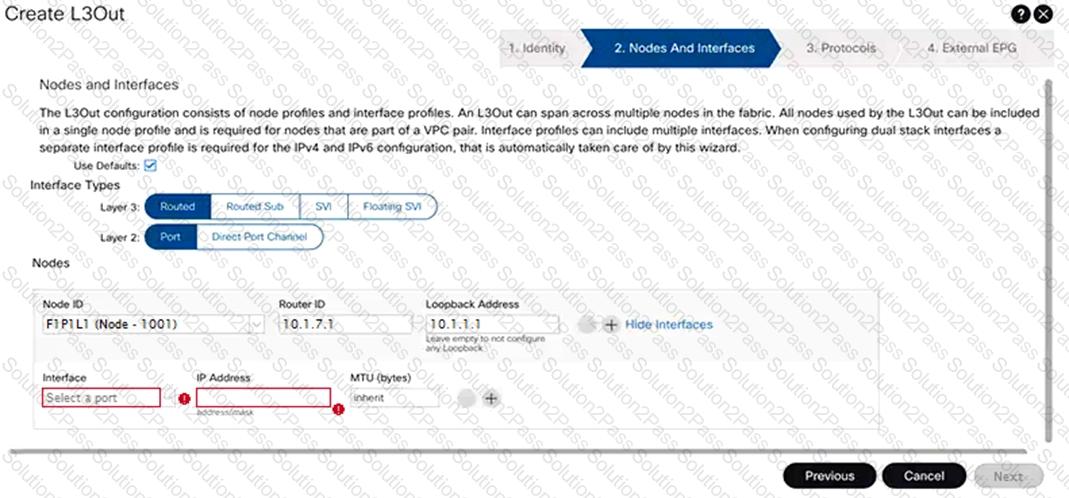
An engineer must configure an L3Out peering with the backbone network. The L3Out must forward unicast and multicast traffic over the link. Which two methods should be used to configure L3Out to meet these requirements? (Choose two.)
An engineer configures a one-armed policy-based redirect service Insertion for an unmanaged firewall. The engineer configures these Cisco ACI objects:
a contract named All_Traffic_Allowed
a Layer 4 to Layer 7 device named FW-Device
a policy-based redirect policy named FW-1Arm-Policy-Based RedirectPolicy
Which configuration set redirects the traffic to the firewall?
An engineer is extending an EPG out of the ACI fabric using static path binding. Which statement about the endpoints is true?
Refer to the exhibit.
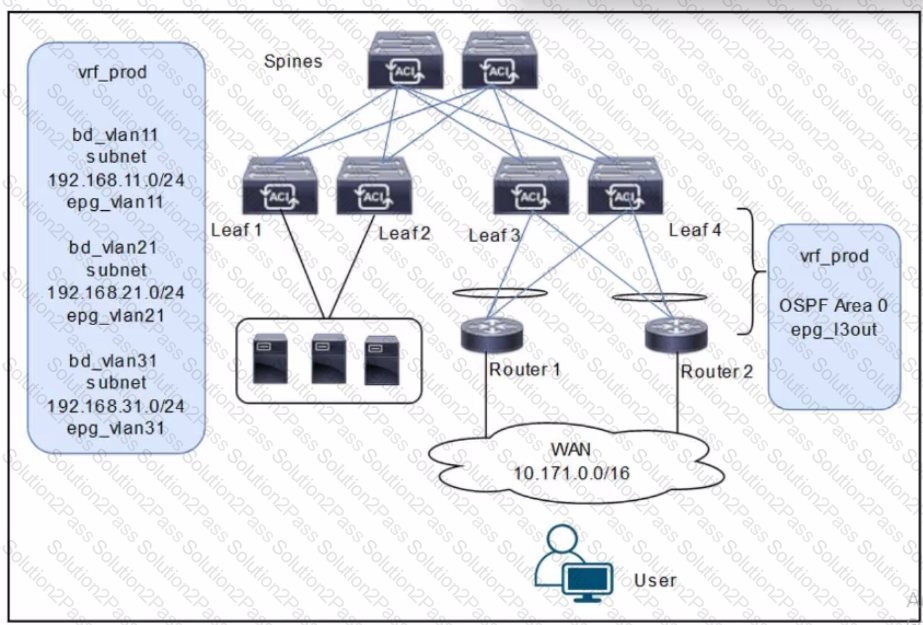
A customer is deploying a WAN with these requirements: •Routers 1 and 2 must receive only routes 192.168.11.0/24 and 192.168.21.0724 from the Cisco ACI fabric •Reachability to the WAN users must be permitted only for the servers that are located in vrf_prod.
Which settings must be configured to meet these objectives?
An engineer implements a configuration backup on the Cisco APIC. The backup job must meet these requirements:
• The backup must transfer the encrypted data to the remote server.
• The transfer must be resumed if the connection is interrupted.
Which configuration set meets these requirements?
A company must connect three Cisco ACI data centers by using Cisco ACI Multi-Site. An engineer must configure the Inter-Site Network (ISN) between the existing sites. Which two configuration steps must be taken to implement the ISN? (Choose two.)
Which new construct must a user create when configuring in-band management?
A Cisco APIC is configured with RADIUS authentication as the default The network administrator must ensure that users can access the APIC GUI with a local account if the RADIUS server is unreachable. Which action must be taken to accomplish this goal?
Which protocol does ACI use to securely sane the configuration in a remote location?
What is MP-BGP used for in Cisco ACl fabric?
A data center administrator is upgrading an ACI fabric. There are 3 APIC controllers in the fabric and all the servers are dual-homed to pairs of leaf switches configured in VPC mode. How should the fabric be upgraded to minimize possible traffic impact during the upgrade?

An engineer must configure a service graph for the policy-based redirect to redirect traffic to a transparent firewall. The policy must be vendor-agnostic to support any firewall appliance, Which two actions accomplish these goals? (Choose two.)
Which two protocols are used for fabric discovery in ACI? (Choose two.)