300-620 Cisco Implementing Cisco Application Centric Infrastructure (300-620 DCACI) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 300-620 Implementing Cisco Application Centric Infrastructure (300-620 DCACI) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
How is broadcast forwarded in Cisco ACI Multi-Pod after ARP flooding is enabled?
An engineer configures a Cisco ACI Multi-Pod for disaster recovery. Which action should be taken for the new nodes to be discoverable by the existing Cisco APICs?
Which description regarding the initial APIC cluster discovery process is true?
A bridge domain for an EPC called “Web Servers” must be created in the Cisco APIC. The configuration must meet these requirements:
Only traffic to known Mac addresses must be allowed to reduce noice.
The multicast traffic must be limited to the ports that are participating in multicast routing.
The endpoints within the bridge domain must be kept in the endpoint table for 20 minultes without any updates.
Which set of steps configures the bridge domain that satisfies the requirements?
What represents the unique identifier of an ACI object?
Which tenant is used when configuring in-band management IP addresses for Cisco APICs, leaf nodes, and spine nodes?
Refer to the exhibit.
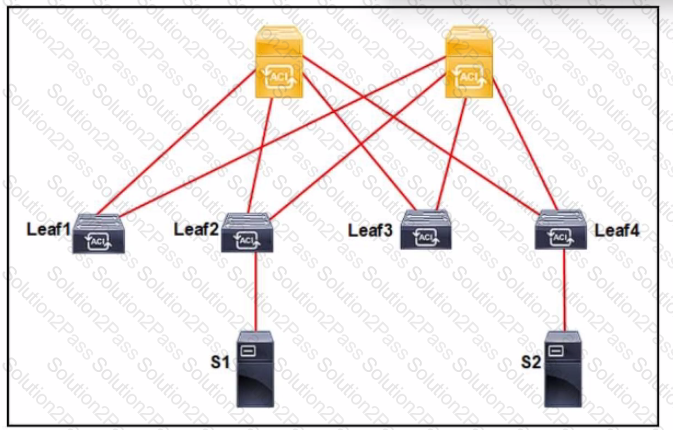
An application called App_1 is hosted on the server called S1. A silent host application. App_2. is hosted on S2. Both applications use the same VLAN encapsulation, which action forces Cisco ACI fabric to learn App_2 on ACI leaf 2?
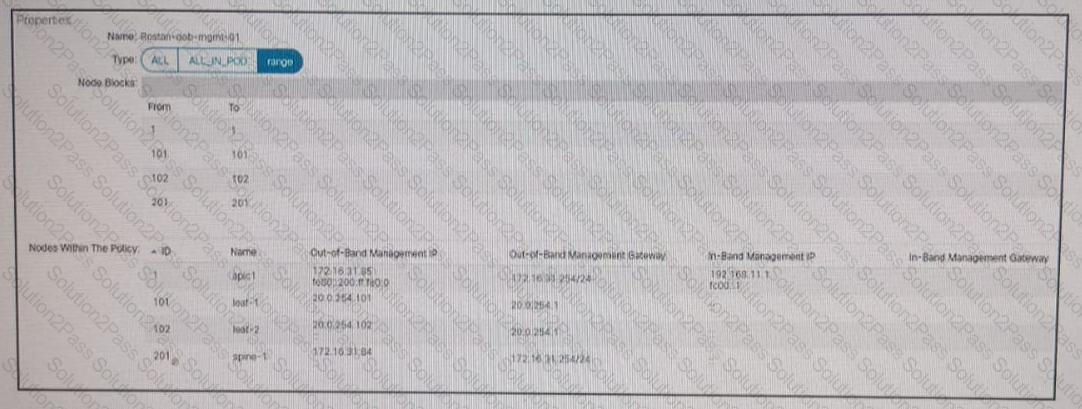
Refer to the exhibit A Cisco ACI fabric is using out-of-band management connectivity The APIC must access a routable host with an IP address of 192 168 11 2 Which action accomplishes this goal?
An engineer created a monitoring policy called Test in a Cisco ACI fabric and had to change the severity level of the monitored object Call home source. Which set of actions prevent the event from appearing in event reports?
A network engineer must integrate VMware vCenter cluster with Cisco ACI. The requirement is for the management traffic of the hypervisors and VM controllers to use the virtual switch associated with the Cisco Application Policy. The EPG called "Vmware-MGMT" with VLAN 300 has been created for this purpose. Which set of steps must be taken to complete the configuration?
Which attribute should be configured for each user to enable RADIUS for external authentication in Cisco ACI?
Refer to the exhibit.
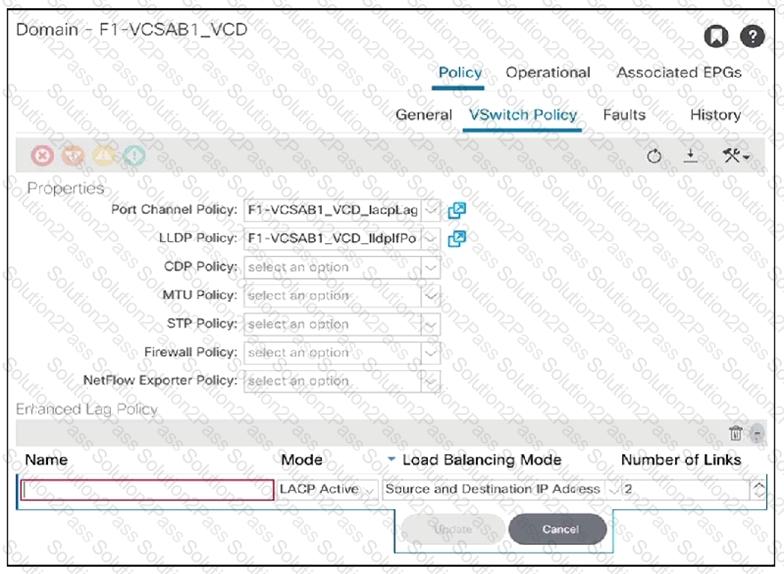
An engineer configures the Cisco ACI fabric for VMM integration with ESXi servers that are to be connected to the ACI leaves. The server team requires the network switches to initiate the LACP negotiation as opposed to the servers. The LAG group consists of two 10 Gigabit Ethernet links. The server learn also wants to evenly distribute traffic across all available links. Which two enhanced LAG policies meet these requirements? (Choose two.)
An Cisco ACI leaf switch learns the source IP address of a packet that enters the front panel port of the switch. Which bridge domain setting is used?
An engineer must advertise a selection of external networks learned from a BGP neighbor into the ACI fabric. Which L3Out subnet configuration option creates an inbound route map for route filtering?
