300-710 Cisco Securing Networks with Cisco Firepower (300-710 SNCF) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-710 Securing Networks with Cisco Firepower (300-710 SNCF) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is the RTC workflow when the infected endpoint is identified?
A network administrator is reviewing a weekly scheduled attacks risk report and notices a host that is flagged for an impact 2 attack. Where should the administrator look within Cisco FMC to find out more relevant information about this host and attack?
An engineer is implementing Cisco FTD in the network and is determining which Firepower mode to use. The organization needs to have multiple virtual Firepower devices working separately inside of the FTD appliance to provide traffic segmentation Which deployment mode should be configured in the Cisco Firepower Management Console to support these requirements?
An engineer wants to change an existing transparent Cisco FTD to routed mode.
The device controls traffic between two network segments. Which action is mandatory to allow hosts to reestablish communication between these two segments after the change?
A network engineer implements a new Cisco Firepower device on the network to take advantage of its intrusion detection functionality. There is a requirement to analyze the traffic going across the device, alert on any malicious traffic, and appear as a bump in the wire How should this be implemented?
What is the role of the casebook feature in Cisco Threat Response?
An engineer wants to connect a single IP subnet through a Cisco FTD firewall and enforce policy. There is a requirement to present the internal IP subnet to the outside as a different IP address. What must be configured to meet these requirements?
Due to an Increase in malicious events, a security engineer must generate a threat report to include intrusion in events, malware events, and security intelligence events. How Is this information collected in a single report?
Which communication is blocked from the bridge groups when multiple are configured in transparent mode on a Cisco Secure Firewall Threat Defense appliance?
In a Cisco AMP for Networks deployment, which disposition is returned if the cloud cannot be reached?
Which feature within the Cisco FMC web interface allows for detecting, analyzing and blocking malware in network traffic?
When packet capture is used on a Cisco Secure Firewall Threat Defense device and the packet flow is wailing on the malware query, which Snort verdict appears?
A VPN administrator converted an instance of Cisco Secure Firewall Threat Defense, which is managed by Cisco Secure Firewall Management Center, from using LDAP to LDAPS for
remote access VPN authentication. Which certificate must be added to allow for remote users to authenticate over the VPN?
An organization does not want to use the default Cisco Firepower block page when blocking HTTP traffic. The organization wants to include information about its policies and procedures to help educate the users whenever a block occurs. Which two steps must be taken to meet these requirements? (Choose two.)
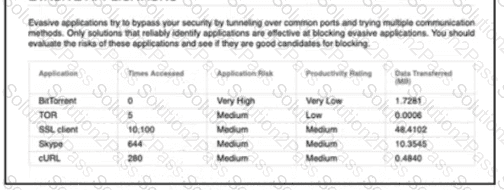
Refertothe exhibit. An engineer is analyzing a Network Risk Report from Cisco FMC. Which application must the engineer take immediate action against to prevent unauthorized network use?
Which CLI command is used to control special handling of clientHello messages?
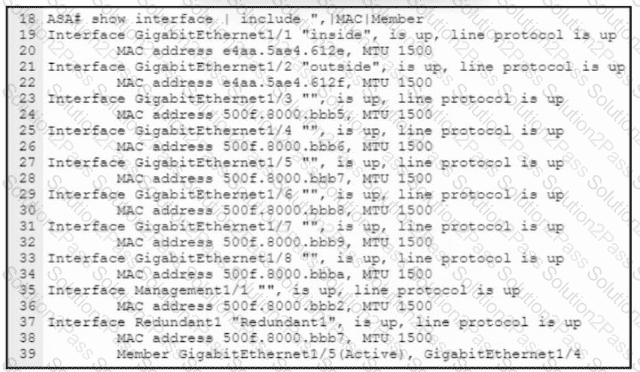
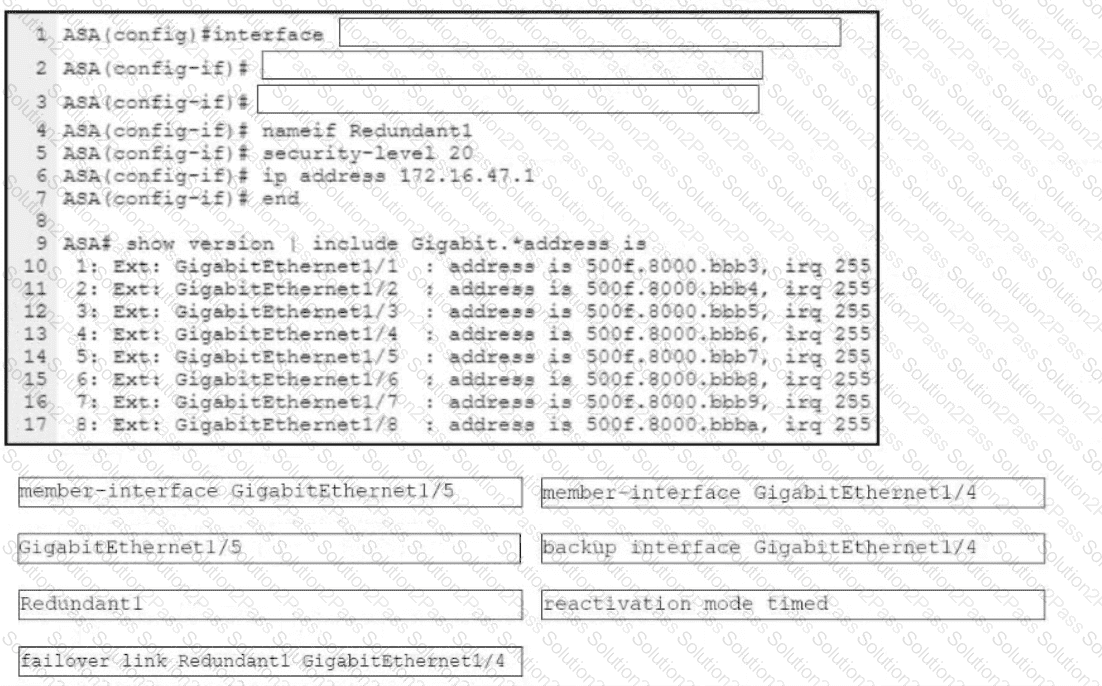
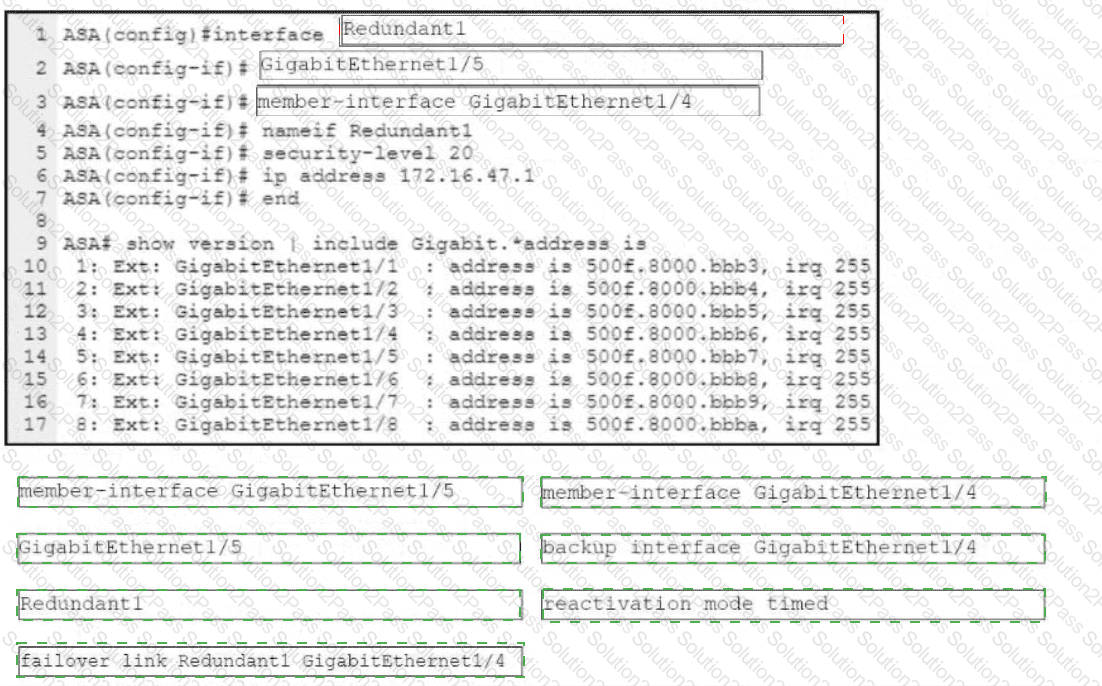
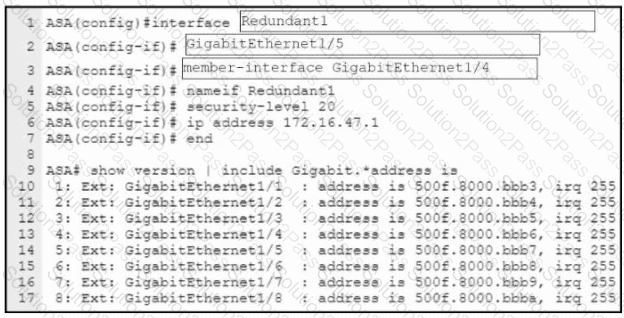
Refer to the exhibit. An engineer must configure a connection on a Cisco ASA Firewall with a Cisco Secure Firewall Services Module to ensure that the secondary interface takes over all the functions of the primary interface if the primary interface fails. Drag and drop the code snippets from the bottom onto the boxes in the CLI commands to configure the failover. Not all options are used.
A user within an organization opened a malicious file on a workstation which in turn caused a ransomware attack on the network. What should be configured within the Cisco FMC to ensure the file is tested for viruses on a sandbox system?
An engineer is creating an URL object on Cisco FMC How must it be configured so that the object will match for HTTPS traffic in an access control policy?
When an engineer captures traffic on a Cisco FTD to troubleshoot a connectivity problem, they receive a large amount of output data in the GUI tool. The engineer found that viewing the Captures this way is time-consuming and difficult lo son and filter. Which file type must the engineer export the data in so that it can be reviewed using a tool built for this type of analysis?
 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.